When reviewing a policy, use the “Evidence for Excessive Permission” that pinpoints unnecessary permissions in AWS IAM policies and helps you understand and address excessive permission.
Step 1: Launch Cloud Entitlements
After you login, select Cloud Security from the landing page. Next, click the App Launcher(on top of the page) and choose CIEM(Cloud Infrastructure Entitlement Management).
Step 2: Access the Evidence for Excessive Permission Popup
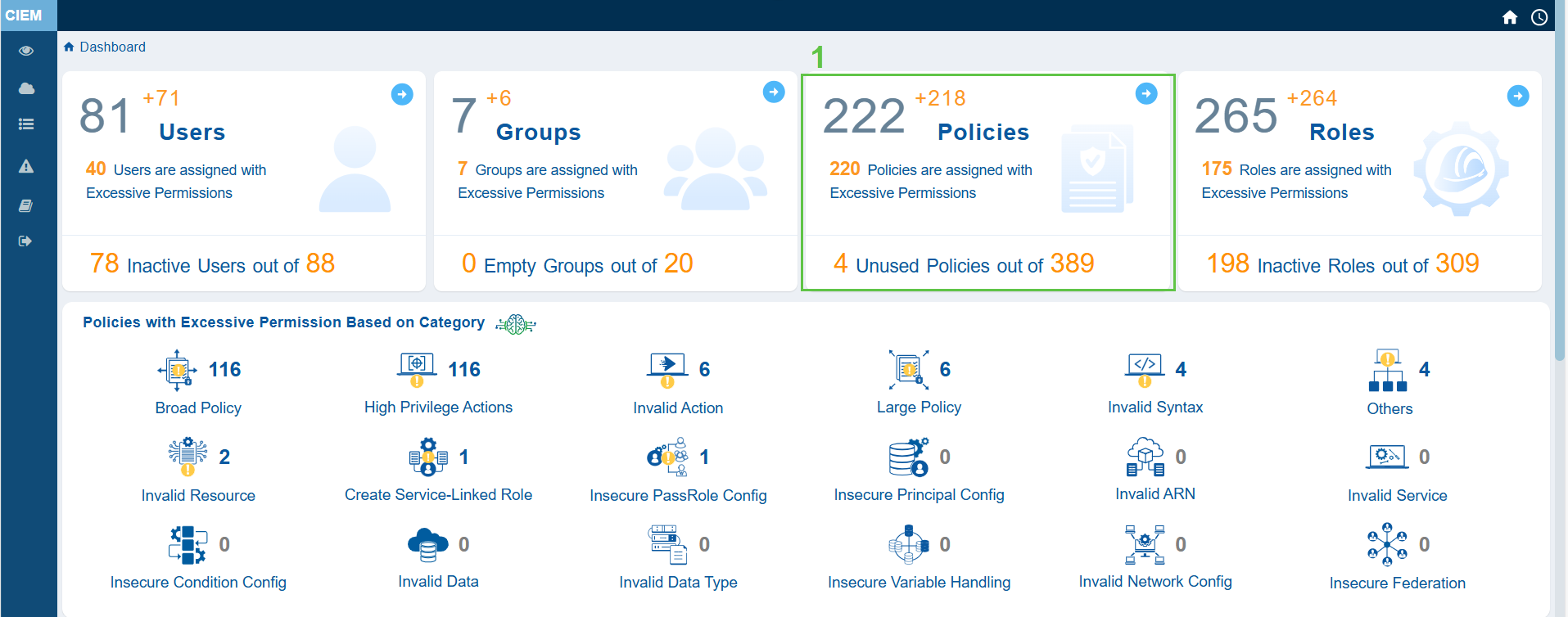
- From the CIEM dashboard, click the “Policies” block to open the detailed statistics page
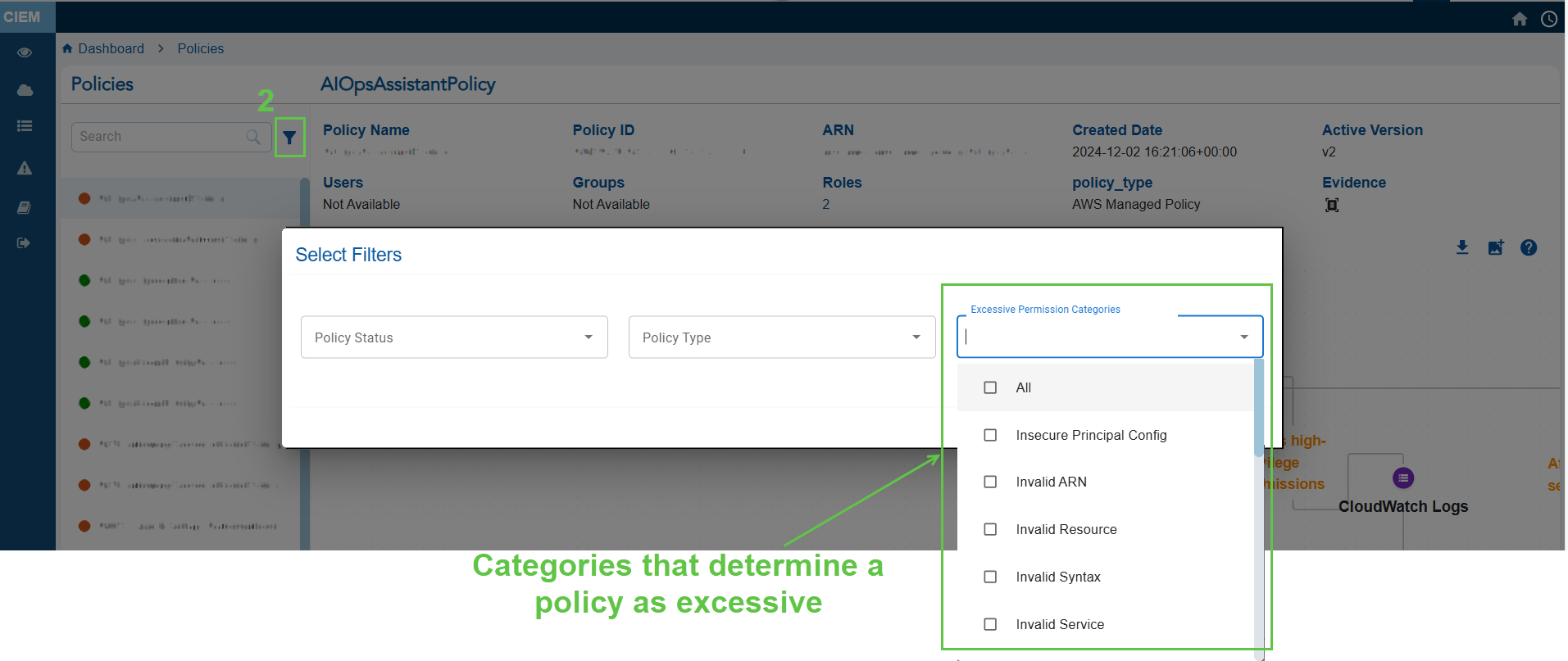
- From the left-hand-side, filter by Permission Categories(Excessive). This lists all the policies that have excessive permissions.
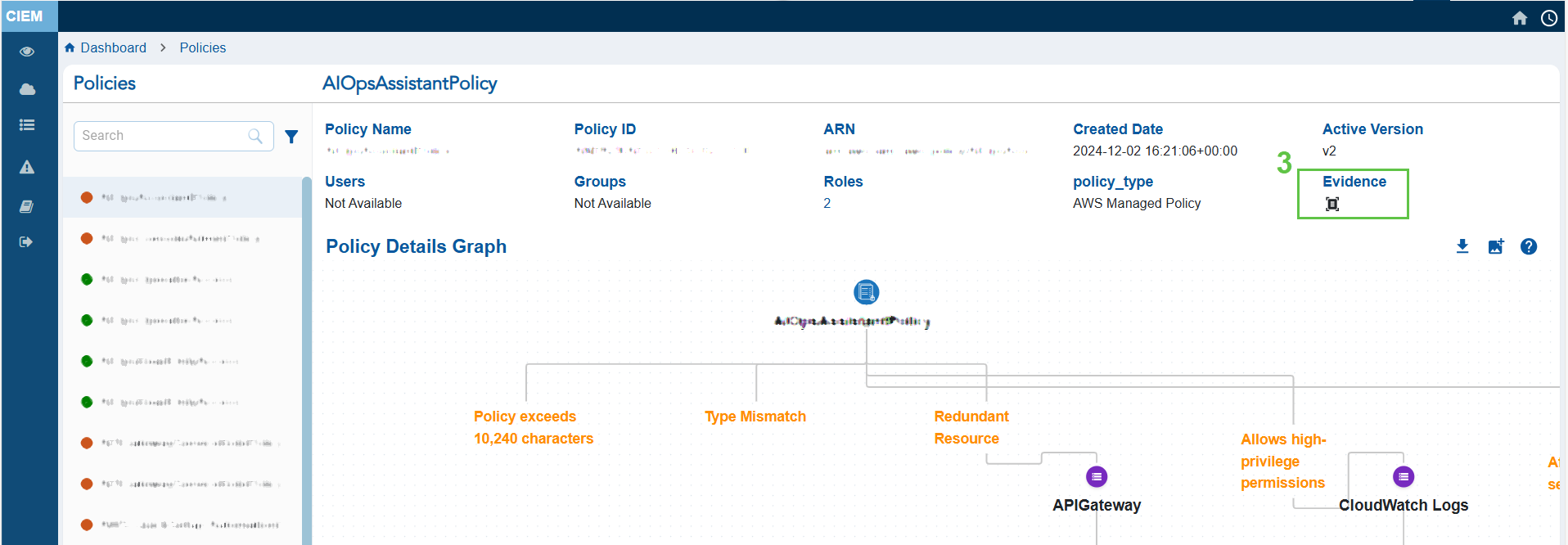
- Click the Evidence for Excessive Permission icon and analyze the information from the pop-up
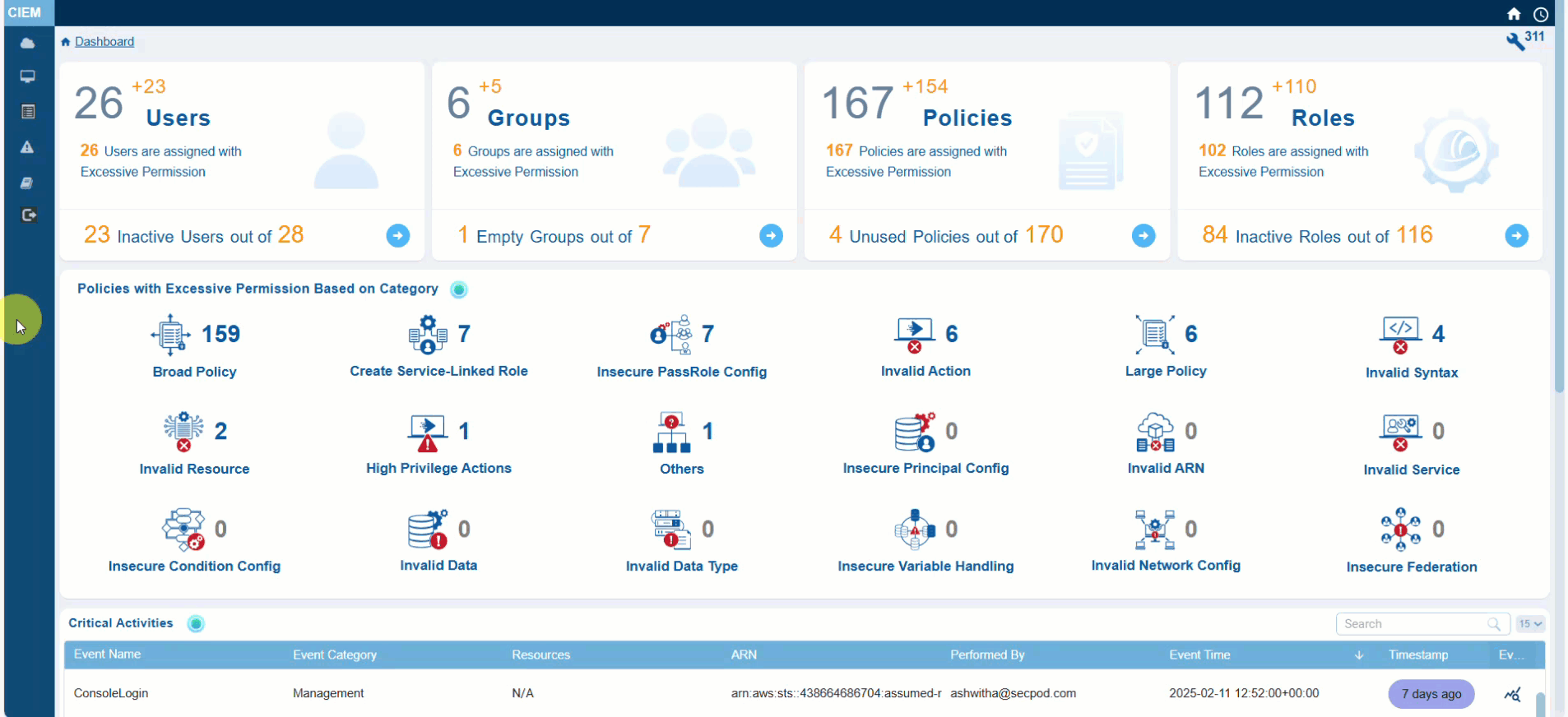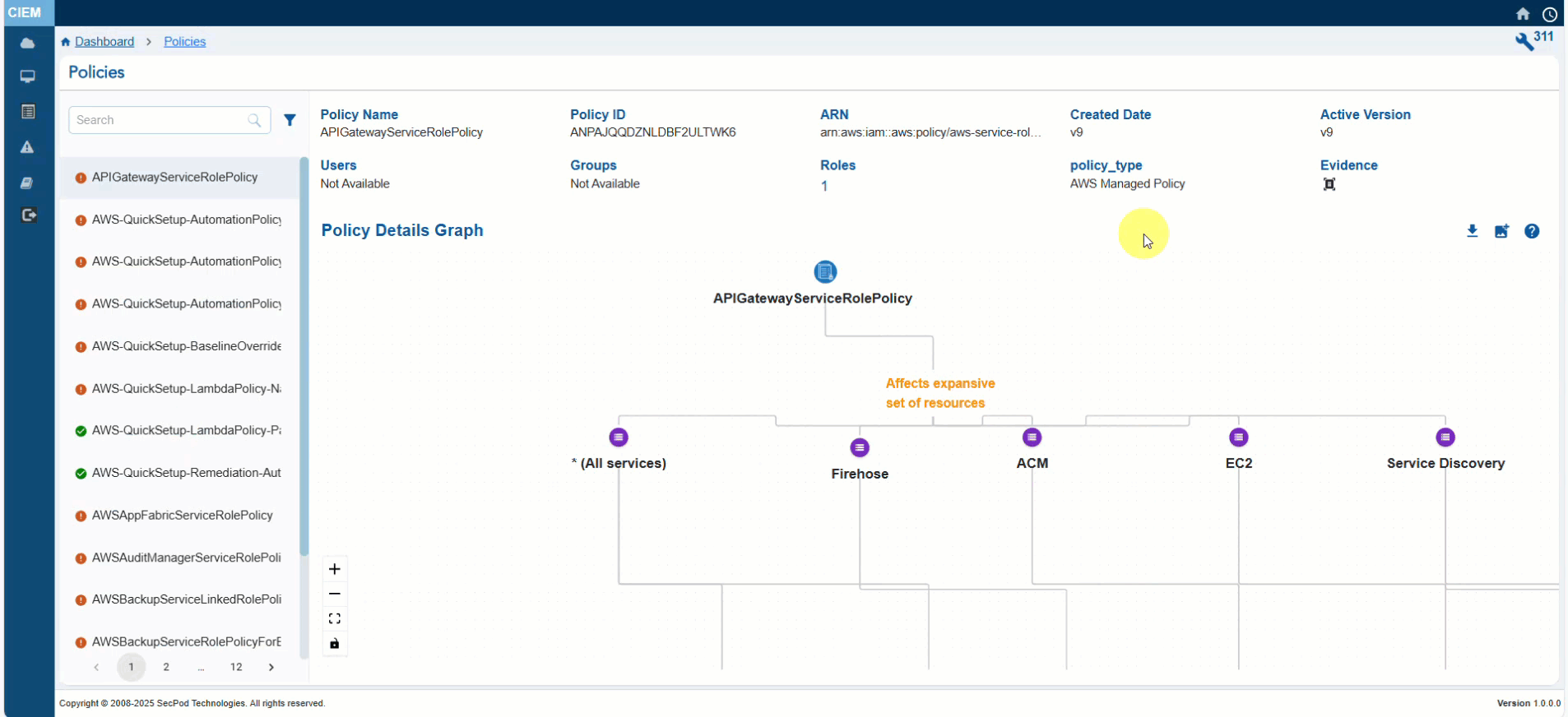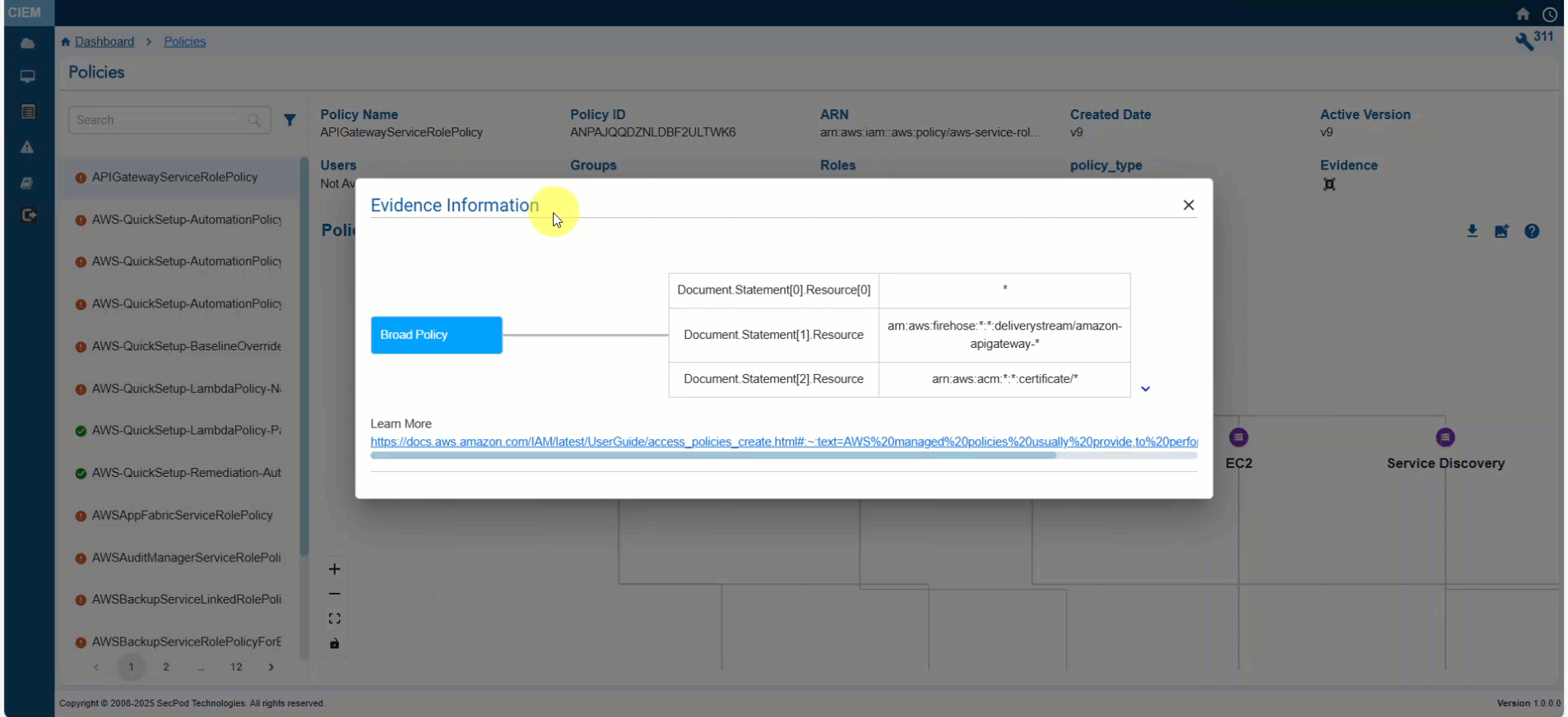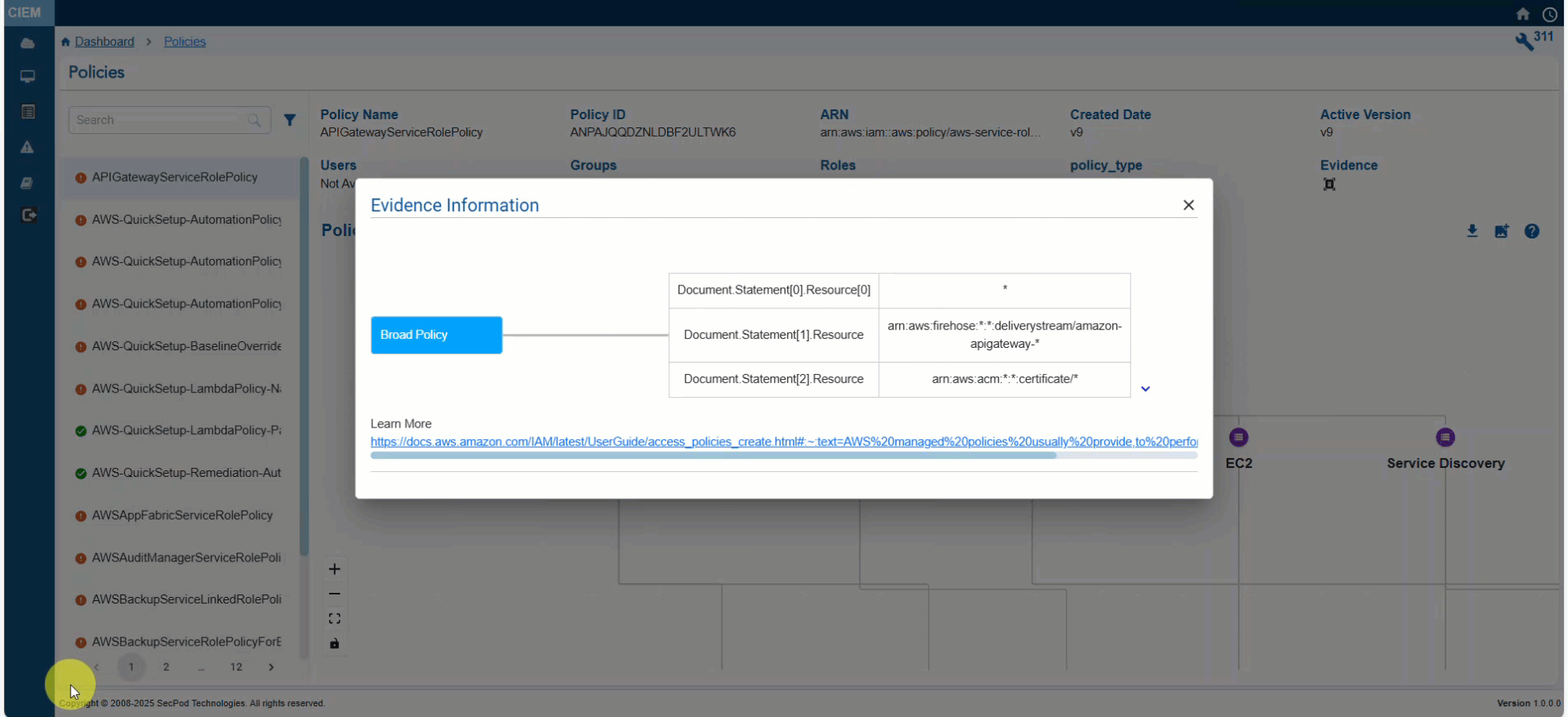
Step 3: Analyze the Evidence Information
- Look at the “Reference Path” to understand where in the policy structure the excessive permission is defined
- Review the “Response” to identify the action that may be unnecessarily allowed or denied
| Evidence Path | Structured representation of the policy’s JSON document, highlighting where the permission is defined. For example, “Policies.PolicyVersionList.Document.Action” refers to the Action field in the policy’s Document structure where permissions like “s3:ReplicateDelete” are specified. |
| Response | Specific permission or action evaluated for excessive access. For example, ” s3:ReplicateDelete” indicates a permission related to s3 bucket replication. |
See Also


