- Download the Saner agent from the Offline Deployer option in the Control Panel.
- Deployment tool can be used for device discovery and saner agent installation. SecPod Saner deployer options are as shown in the image below:
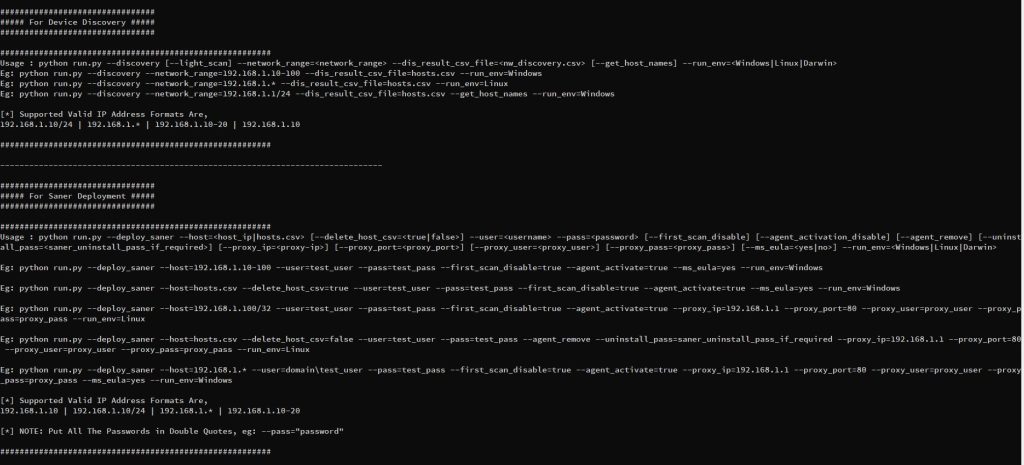
Note: To deploy Saner agents on Windows, we need to run the deployer script from a Windows system, and to install on Linux/macOS systems we need to run the deployer from Linux/macOS operating systems respectively.
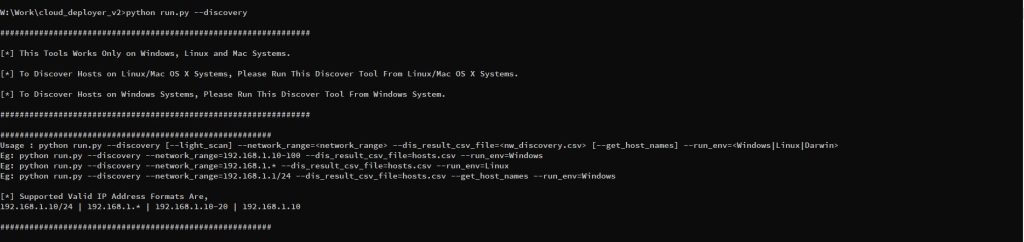
3. To discover devices in the network, run the following command and pass the CSV filename as a command-line argument to the deployer,
Options:
| –discovery | To Run device discovery |
| –network_range | Network IP Range |
| –light_scan | Does only ICMP scan (Optional) (Default: full scan) |
| –dis_result_csv_file | Discovered IPs/Hosts will be stored in this CSV file |
| –get_host_names | Save hostname instead of host IPs (Optional) (Default: Won’t collect hostnames) |
| –run_env | Running OS: From where this tool is being run (Values: Windows|Linux|Darwin) |
> python.exe run.py –discovery options
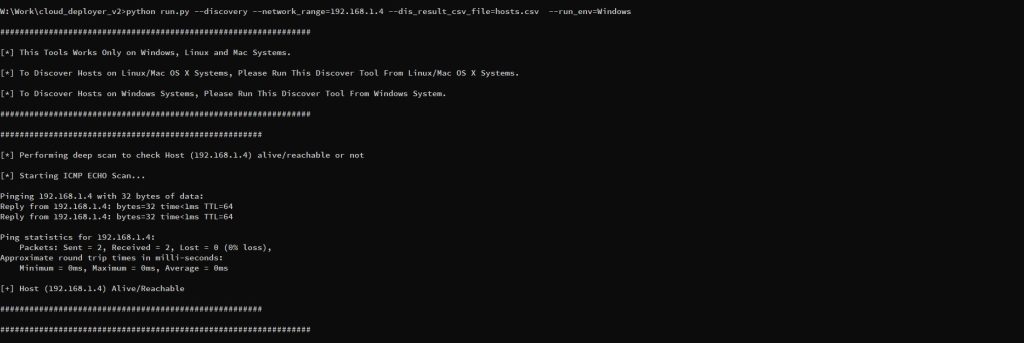
> python.exe run.py –discovery –network_range=192.168.1.1/24 –dis_result_csv_file=hosts.csv –run_env=Windows
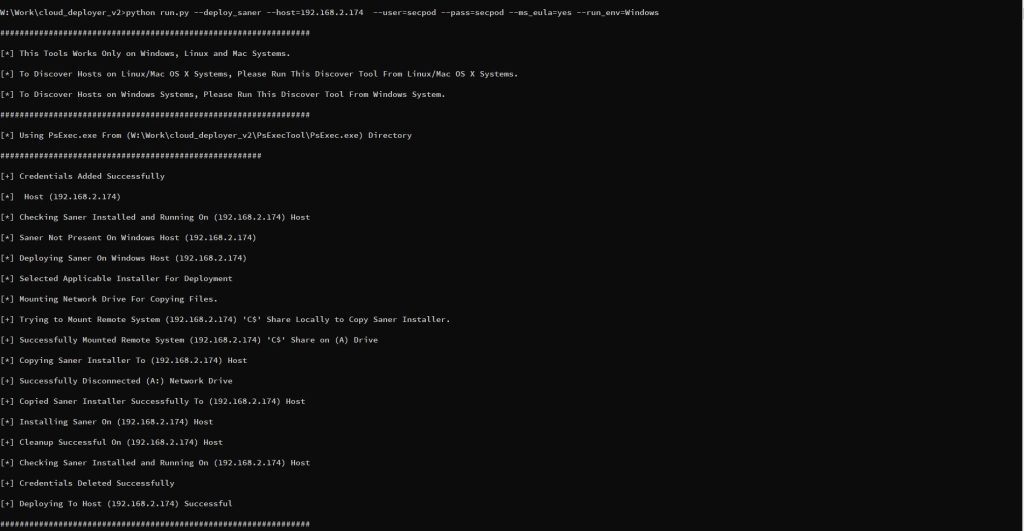
4. To deploy the Saner agent on Windows, run the following commands.
| –deploy_saner | To deploy Saner agent |
| –host | Network IP Range OR CSV file (Format: “ip address”,”username”,”password”) (credentials: optional, if passed from command-line) |
| –delete_host_csv | To delete/keep host CSV file, NOTE: We advise to delete this file, if credentials are present (Values: true|false) |
| –user | Username |
| –pass | Password (passwords should be in double Quotes eg: –pass=”password”) |
| –first_scan_disable | To disable agent first scan just after the agent installation (Optional) (Default: First scan will be enabled) |
| –agent_activation_disable | To disable agent activation just after the agent installation (Optional) (Default: Agent activation will be enabled) |
| –agent_remove | Include to remove saner agent from endpoint (Optional) (Default: Agent will not be removed) |
| –uninstall_pass | Required if Saner agent uninstallation require password (Optional) |
| –ms_eula | Accept Microsoft eula to run psexec tool (Values: yes|no) (Optional) |
| –run_env | Running OS: From where this tool is being run (Values: Windows|Linux|Darwin)(Optional)(Default: Tries to find out automatically) |
| –proxy_ip | Proxy Server IP (Optional) |
| –proxy_port | Proxy Server Port (Optional) |
| –proxy_user | Proxy Username (Optional) |
| –proxy_pass | Proxy Password (Optional) |
> python.exe run.py –deploy_saner –host=192.168.2.1-100 –user=”Administrator” –pass=”password” –ms_eula=yes –run_env=Windows
5. To deploy the saner agent on Linux/macOS, run the following command
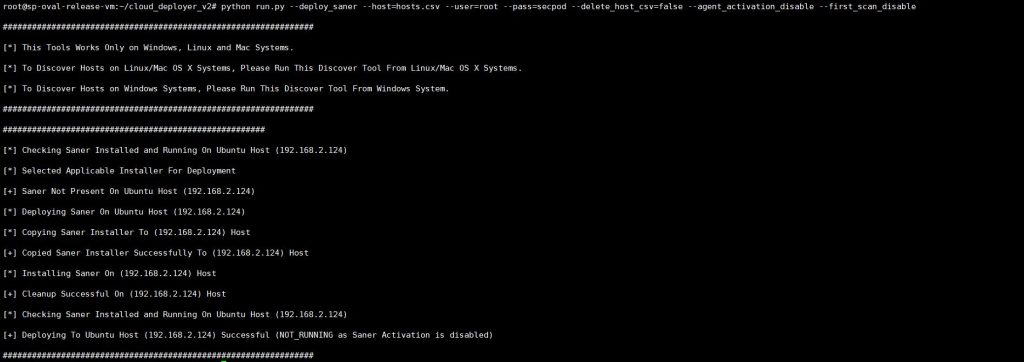
> python run.py –deploy_saner –host=hosts.csv –user=”root” –pass=”password” –delete_host_csv=false –agent_activation_disable –first_scan_disable
6. If a proxy is enabled, pass proxy details to the deployer script as shown below,
–proxy_ip=192.168.1.1 –proxy_port=80 –proxy_user=”proxy_user” –proxy_pass=”proxy_pass”
> python run.py –deploy_saner –host=192.168.1.100 –user=”root” –pass=”password” –proxy_ip=192.168.1.1 –proxy_port=80 –proxy_user=”proxy_user” –proxy_pass=”proxy_pass”
7. Other deployer tool options,
> python run.py –deploy_saner –host=hosts.csv –delete_host_csv=true –run_env=Linux –first_scan_disable
> python run.py –deploy_saner –host=hosts.csv –delete_host_csv=true –user=test_user –pass=”test_pass” –run_env=Linux –agent_activation_disable –first_scan_disable
> python run.py –deploy_saner –host=192.168.2.1-100 –user=domain\test_user –pass=”test_pass” –proxy_ip=192.168.1.1 –proxy_port=80 –proxy_user=”proxy_user” –proxy_pass=”proxy_pass” –ms_eula=yes –run_env=Windows



