The MITRE ATT&CK framework supports a threat-informed approach to cloud security by aligning identified risks with real-world adversary tactics and techniques. By mapping misconfigurations to known attacker behaviours, organizations can effectively prioritize remediation efforts, enhance threat detection capabilities, and improve incident response. This standardized methodology facilitates clearer communication among security teams, and makes sure to focus on high-impact risks, and supports the development of defense tailored to actual attacker strategies in cloud environments.
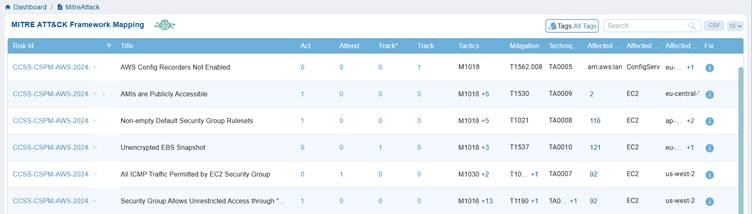
Saner CSRP uses the MITRE ATT&CK Framework Mapping and provides a consolidated view of identified cloud risks aligned with adversarial tactics, techniques, and mitigation strategies in a tabular format. Each risk is mapped to ATT&CK identifiers, showing the impacted assets, affected regions, and recommended fixes. This helps security teams quickly understand how risks relate to real-world attacker behaviours, prioritize response actions, and strengthen defences with a threat-informed approach.
Access the MITRE ATT&CK Framework Mapping
Access the MITRE ATT&CK Framework Mapping from the top-right hand side of the CSRP dashboard.
This opens the MITRE ATT&CK Framework Mapping table. Each column provides details on the identified cloud risks as described:
Identify and Map Cloud Risks to MITRE ATT&CK Behavior with ID and Title
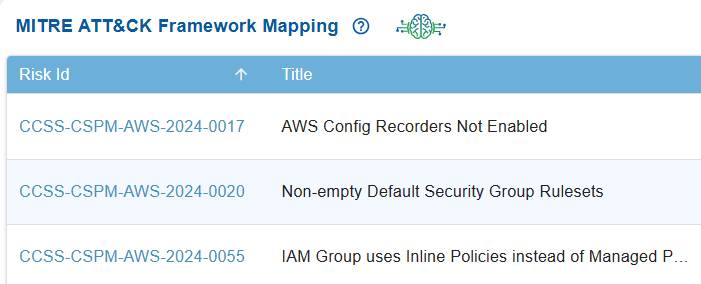
In Saner CSRP MITRE ATT&CK Framework Mapping view, the Risk ID serves as a unique reference for tracking security issues, while the Title describes the specific cloud misconfiguration or weakness, such as disabled AWS Config Recorders or insecure security group rules etc.
Each of these risks is mapped to relevant MITRE ATT&CK tactics, techniques, and mitigations, showing how they can be exploited by adversaries and what defensive actions are recommended. This linkage helps translate cloud risks into the context of real-world attacker actions, helping organizations to prioritize and address them more effectively.
Prioritize and Manage Risks Using Action Categories
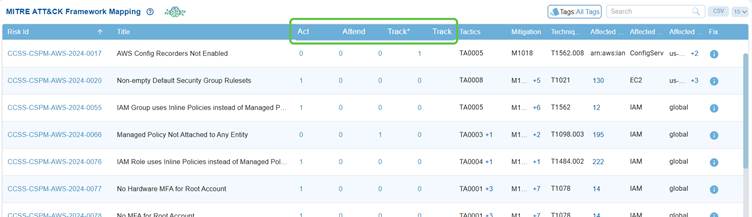
Saner CSRP MITRE ATT&CK Framework Mapping view, the columns Act, Attend, Track*, and Track categorize risks to guide response and remediation efforts.
Act highlights risks that need immediate fixing due to their severity or exploitability, while Attend marks those requiring review and further assessment. Track* is used for risks under closer monitoring because of their higher exposure or links to multiple attacker techniques, and Track covers risks that are monitored on a general basis.
This structured approach helps teams prioritize actions, ensuring the most critical threats are addressed first while maintaining visibility on lower-priority risks.
Understand the MITRE Tactics and Techniques Exploited by Each Risk and Corresponding Mitigation Strategy
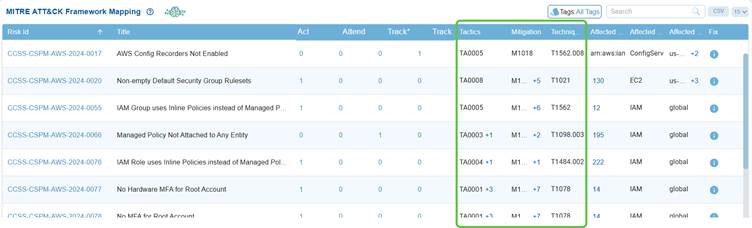
In the MITRE ATT&CK framework, each tactic code represents an attacker’s objective, each technique code describes the specific method used to achieve that objective, and each mitigation code outlines the recommended defense.
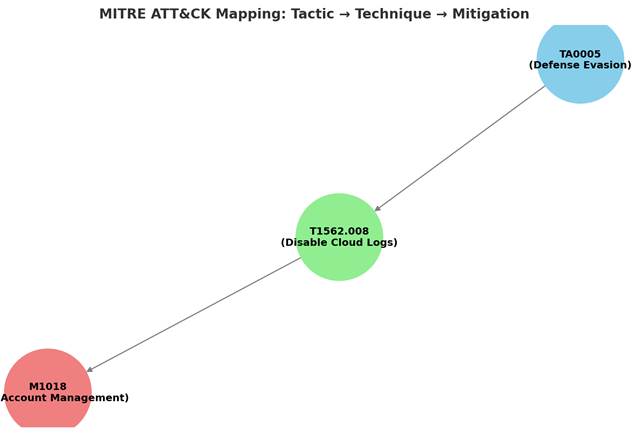
For example in Saner CSRP MITRE ATT&CK Framework Mappingdashboard view, the tactic TA0005 (Defense Evasion) reflects the attacker’s goal of avoiding detection, the technique T1562.008 (Disable Cloud Logs) shows how they might achieve it, and the mitigation M1018 (User Account Management) suggests a defensive action to counter the risk. Together, these codes create a clear mapping from attacker goals to actions and the corresponding defensive strategies.
Here’s a simple visual mapping of how MITRE ATT&CK Tactic (goal) connects to a Technique (method) and then links to a Mitigation (defense measure) based on Saner CSRP MITRE ATT&CK Framework Mapping.
Saner CSRP provides the codes for each Risk ID across the 3 code categories. Move your cursor over the code in Tactics, Mitigation, and Techniques Exploited columns to see the additional associated tactics, techniques, or mitigations beyond the one currently displayed.
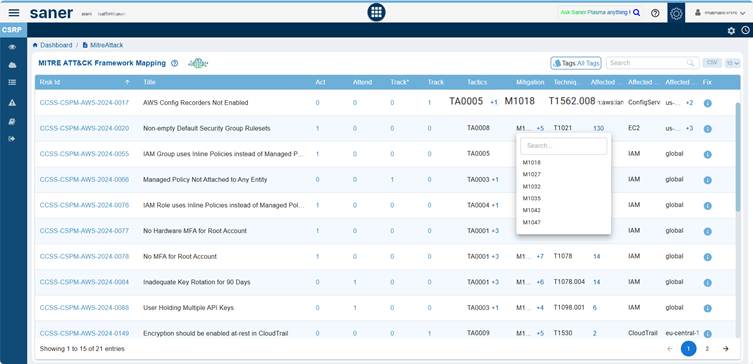
For example:
- M1018 +5 → shows User Account Management plus 5 more mitigations linked to that risk.
- TA0005 +1 → shows Defense Evasion plus 1 additional tactic related to that risk.
This helps avoid clutter by showing only the primary mapping while still allowing access to all related MITRE ATT&CK entries through expansion.
View the Impacted Resources, Services, and Regions
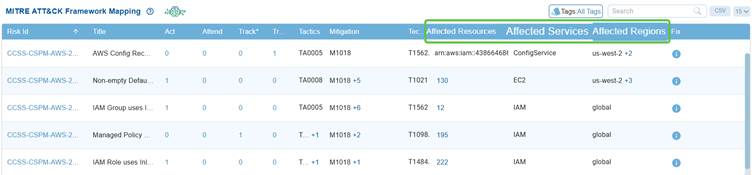
In the Saner CSRP MITRE ATT&CK Framework Mapping view, the Affected Resources, Services, and Regions columns show where and how risks impact the cloud environment. Affected Resources indicate the specific assets or instances exposed, Affected Services identify the cloud services such as IAM, EC2, or ConfigService that adversaries could target, and Affected Regions highlight the geographic scope of the exposure, whether limited to a region like us-west-2 or spanning globally. Together, they provide context on the scale and location of misconfigurations, linking ATT&CK techniques to real-world cloud assets that attackers may exploit.
Remediate Risks from MITRE ATT&CK Framework Mapping
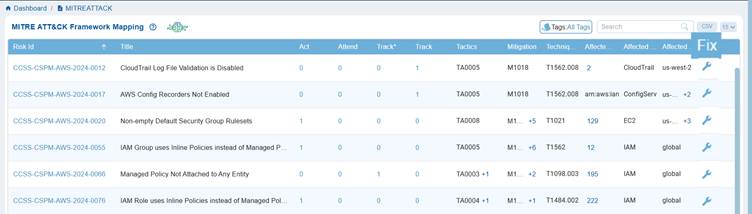
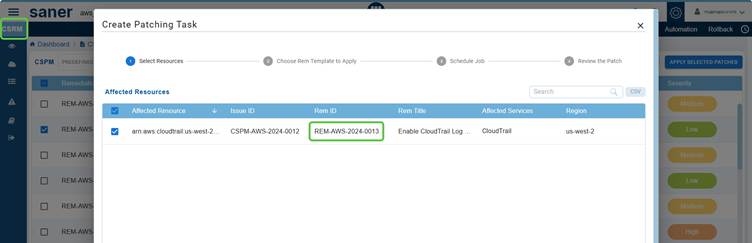
In the Saner CSRP MITRE ATT&CK Framework Mapping view, the Fix column provides direct access to remediation guidance for each identified risk. It links the mapped risk, tactic, and technique to actionable steps that security teams can take to mitigate or eliminate the risk.
Clicking the Fix icon corresponding to a risk redirects you to Saner CSRM to begin your patching activities.
Related Topics


