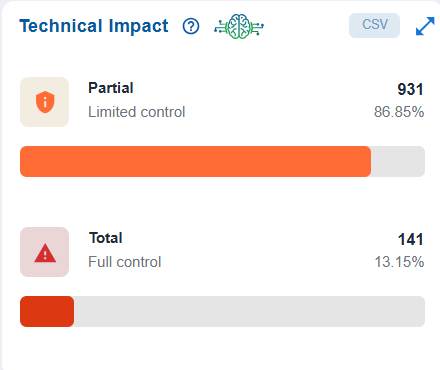
The Technical Impact block presents a clear breakdown of the severity of potential impacts on resources. It highlights that Partial (Limited Control) and Total (Full Control) resources,enabling stakeholders to assess the distribution of control risks and prioritize mitigation efforts accordingly.
For example, Partial (Limited Control) with 931 resources(86.85%) indicates that the majority of affected resources only allow limited control, meaning the impact of exploitation is somewhat constrained.
Total (Full Control) with 141 resources (13.15%) indicates a smaller portion of resources would grant full control if compromised, representing a higher-severity risk.
| If the value is | What it means |
| Partial | The threat actor either gains limited control or experiences information exposure due to the misconfiguration. Additionally, there is a low likelihood of achieving complete control because repeated attempts to exploit the cloud organization are often impractical. One example of limited control is a denial-of-service attack. |
| Total | At the organization level, the system gives the adversary total control over the behavior of the software. In other words, it discloses all the information on the infrastructure that contains the misconfiguration. |
Related Topics


