The questionnaire is designed to assist organizations in configuring and evaluating their security posture by addressing various domains of cybersecurity. It provides a fixed set of closed-ended questions with predefined answer options (e.g., Yes/No), making it efficient for data comparison and analysis. Users can also assign mission-critical values and categorize responses, enabling a prioritized view of security areas that require immediate attention.
After completing the configurations and saving, the system automatically runs the scan with the configurations and displays the details in the CSRP dashboard accordingly.
Access the Questionnaire
Click the icon on the top-right of the Saner CSRP dashboard to open the questionnaire. Answering questions from each category in the questionnaire helps categorize risks effectively and produce accurate results.
Complete the Configuration
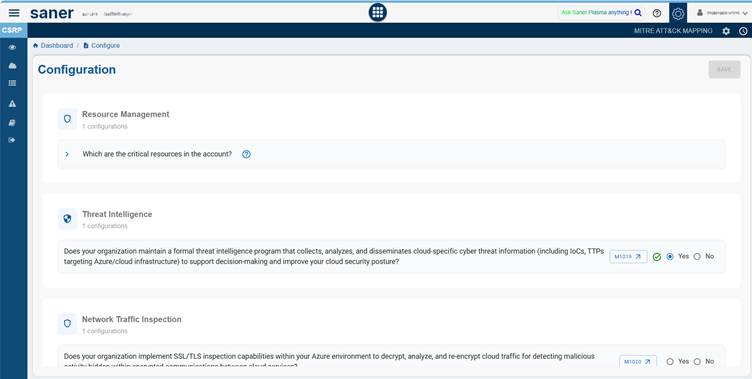
Each section includes task-oriented configurations aimed at ensuring robust protection, compliance, and a proactive defense against threats.
MITRE recommends specific mitigation methods to improve the security of cloud environments. In the configuration questionnaire, only those mitigation checks that cannot be automated are included, while the automated checks are excluded. This approach ensures that manual validation concentrates on areas where automation is not possible, aligning the questionnaire with MITRE’s recommended security practices.
NOTE: As an example, Resource Management and User Training sections are explained. You can follow the same approach to complete the remaining sections of the questionnaire.
Expand the various sections of the questionnaire to provide your response.
Resource Management
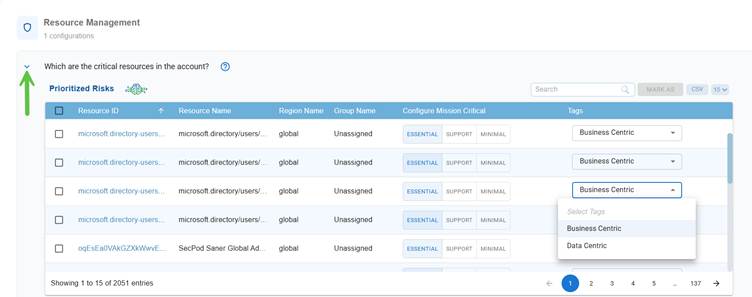
Configuration to identify the critical resources in the account.
Click on the downward arrow to display the Prioritized Risks pane.
Within the Prioritized Risks pane, under the Configure Mission Critical column, click on one of the values(Essential, Support, or Minimal) to configure the status indicating if the risk impacts mission-critical resources. This helps security teams understand the potential business impact of each finding.
Select the tag category(Business Centric or Data Centric) corresponding to a resource from the drop-down list in Tags column.
Click the link to read more on how the configured tags help to Assess and Prioritize Risks Across Resource Categories from the dashboard.
User Training
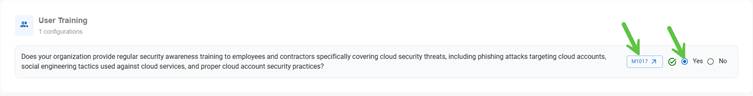
Configuration to confirm if your organization provides regular security awareness training to employees and contractors.
Clicking on the reference MITRE ID (M1017) navigates you to the MITRE ATT&CK framework where you gain insight into User Training information.
Use the slider(Yes) and turn it on or off to enable or disable the User Training configuration. On turning on the configuration, it evaluates your organization provides regular security awareness training to employees and contractors specifically covering cloud security threats, including phishing attacks targeting cloud accounts, social engineering tactics used against cloud services, and proper cloud account security practices.
Save Your Updates
Just click the Save button on the top-right of the questionnaire.
Related Topics


