Excessive permissions in cloud security occur when users or applications have more access than necessary to perform their tasks.
For instance, actions like deleting an S3 bucket or terminating an EC2 instance are considered high-privilege actions and are typically not granted to everyone with access to the AWS account. Instead, these permissions are reserved for a select few individuals, such as administrators or site owners. When managing these high-privilege actions among team members, there is a risk that a team member who is expected to have only read-only access may inadvertently be granted permissions to perform high-privilege actions. In this case, that team member is said to have excessive permissions.
This poses significant security risks, as it allows insiders to exploit permissions or for hackers to take control through phishing attacks.
Step 1: Launch Cloud Entitlements
After you login, select Cloud Security from the landing page. Next, click the App Launcher(on top of the page) and choose CIEM(Cloud Infrastructure Entitlement Management).
Step 2: Access the Infrastructure for Which You Want to Review Excessive Permissions
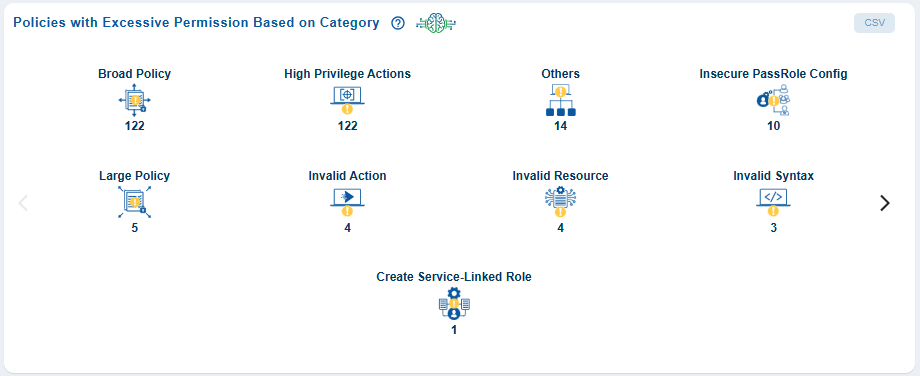
From the CIEM dashboard, click on any of the blocks(user/role/group/policy) to open the additional details page.
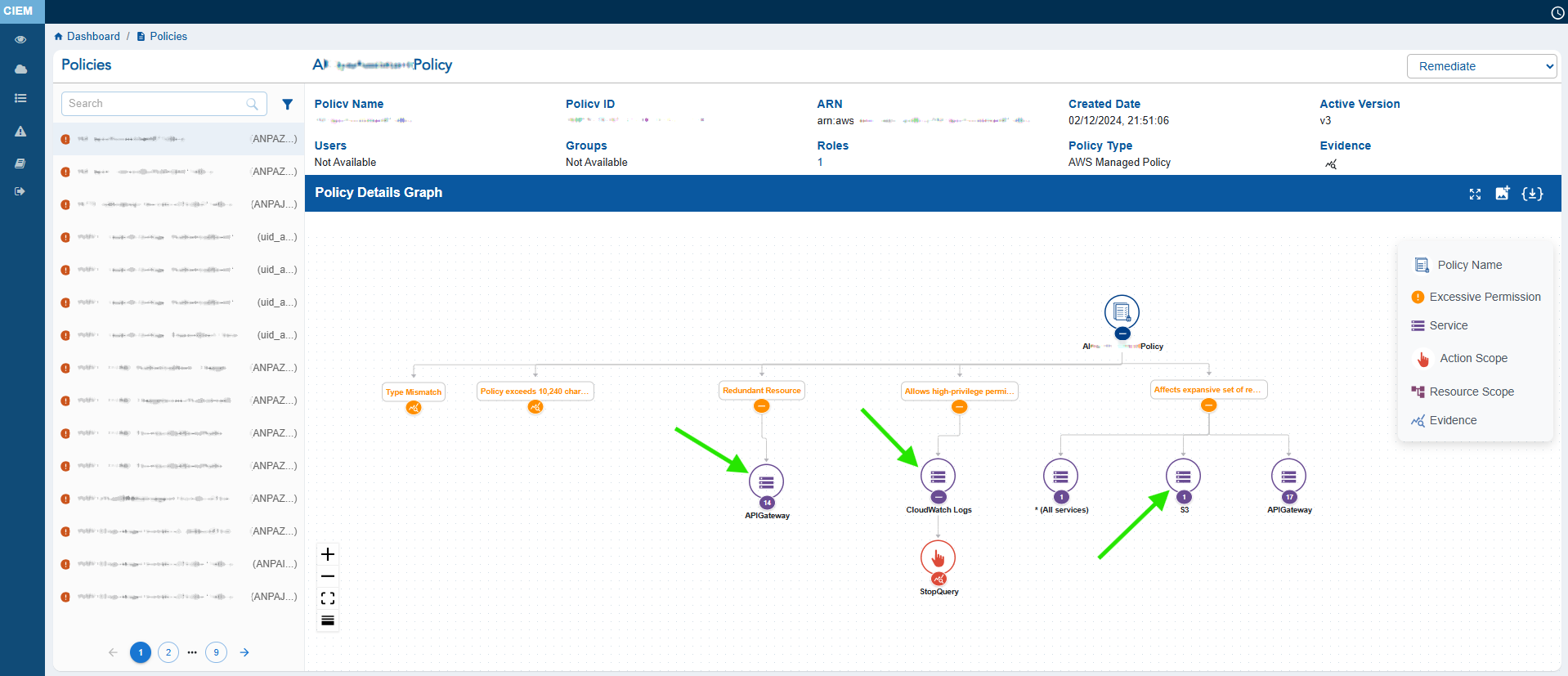
Step 3: Access the Details Map to View the Requisite Service
See Also


