The term “automatable” refers to how easily and quickly a cyber threat actor can automate the exploitation events. It addresses the question, “Can an attacker easily automate the creation of exploitation events for this risk?” Several factors determine if an actor can quickly trigger multiple exploitation events. These factors include the complexity of the attack, the specific code that the actor needs to write or configure, and the typical network deployment of the vulnerable system, including how exposed the system usually is.
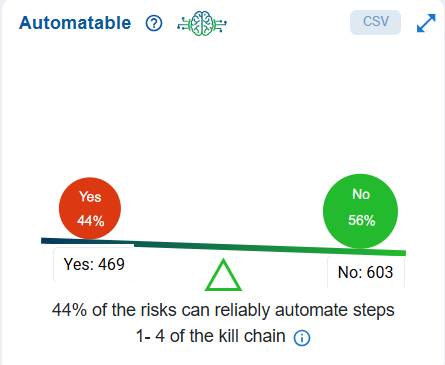
The Automatable block displays the distribution of risks based on the reliability of triggering multiple exploitation events.
| If the value is | Then |
| No | The attacker cannot automate the creation of exploitation events for this risk |
| Yes | The attacker can easily automate the creation of exploitation events for this risk |
The dashboard chart illustrates the prioritization of risks from an automation perspective. In this case, it indicates that 44% or 439 of the identified risks are automatable across steps 1–4 of the kill chain, meaning that the remaining 56% or 603 are not automatable. As a result, attackers cannot currently depend on automation to exploit these risks at scale, which lowers the likelihood of widespread and rapid compromise. However, even though automation is not a factor for the non-automatable attacks, these risks still require attention if they can be exploited through manual efforts.
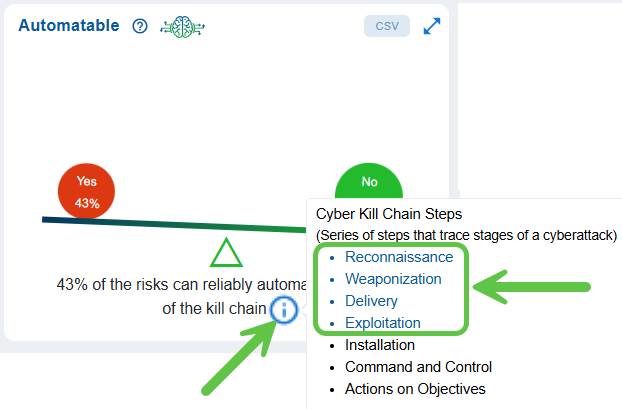
To see the series of steps that trace stages of a cyber-attack, move your cursor over the information icon.
Related Topics


