To setup alerts across the different SanerCloud tools with a subscription-enabled model involves defining conditions for the alerts and setting up responses.
Pre-requisites
- Configure your email settings before proceeding to enable the alerts
- Choose the relevant organization associated to the account
Step1: Access Cloud Alerts
From the side menu, click on the Cloud Alerts icon. Just hover over the icon to see the name.
Step2: Enable Subscription
Subscription allows you to customize alerts according to your specific needs. You can establish criteria based on the tool you subscribed to receive notifications (for example, about particular roles being assigned, privileged actions being taken, or changes to access permissions). The system triggers alerts based on these criteria.
To enable subscription, just turn on the slider for the tool you subscribed. The relevant alert criteria for the selected tool gets enabled for you to update.
Step3: Define the Alert Recipient Email Ids
Provide the email ids for which you want to trigger the alert. You can key in one or more recipient email ids. If you want to enter multiple email addresses, then separate them with commas.
Step4: Setup Conditions
Select the checkbox to specify the alert criteria for the tool.
| Tool/Alert | Condition(s) |
|---|---|
| Asset Exposure | Publicly Accessible Resources, Watchlisted Resources, Newly Created Resources, Outdated Resources |
| Posture Anomaly | Posture Anomaly Detection: All Anomalies and Custom Detection Custom Detection Rules: All queries and Custom Detection Rules High Confidence Anomalies: All anomaly rules that call for immediate attention |
| Identity Entitlement Management | Compliance checks include: All compliance checks, Custom checks(CIEM ids), Inactive Users, Users with Excessive Permissions, Groups with Excessive Permissions, Roles with Excessive Permissions, Policies with Excessive Permissions, and Critical Log Activities Log checks include: Critical Log Activities |
| Remediation Management | All Issues, Critical Issues |
| Posture Management | All Compliance Checks, Critical and High Severity Checks, Custom Checks |
Understand the Function of Notification Condition in Each Tool
Saner Cloud provides proactive security by triggering alerts based on comprehensive scan results. The system conducts scheduled or on-demand scans to evaluate the configurations, access permissions, and anomalies, aligning them with the defined security policies. When issues such as misconfigurations, emerging vulnerabilities, or unauthorized changes are identified, Saner Cloud promptly generates targeted alerts to help take timely action. Note that neither detection nor alerts trigger for changes introduced and resolved between scans, such as a temporary port exposure. For example, if a critical port is opened at 2:00 PM and closed at 3:00 PM, but the scan runs at 4:00 PM, then the issue is neither identified nor alerted about. This approach ensures that alerts are meaningful, relevant, and actionable, helping you focus on persistent or high-risk issues.
After selecting the conditions and entering the email, clicking the Update button saves the subscription preferences and activates alerting.
Cloud Security Asset Exposure(CSAE)
Choose the asset exposure condition that must trigger notifications.
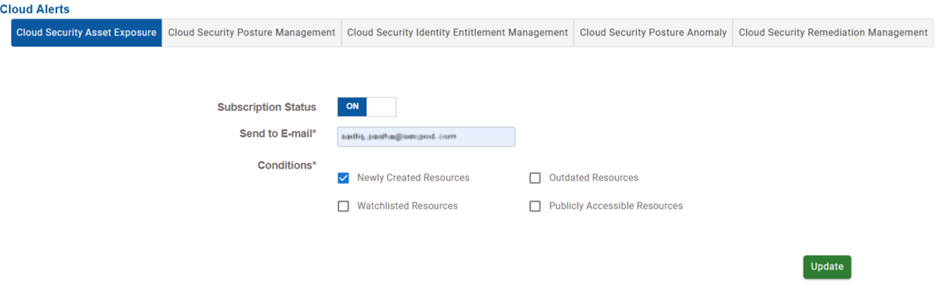
| Condition | Function |
|---|---|
| Newly Created Resources | Notifies when new cloud resources are provisioned |
| Outdated Resources | Alerts on resources that are deprecated or outdated |
| Watchlisted Resources | Alerts if flagged or critical resources are involved |
| Publicly Accessible Resources | Triggers alert when resources become publicly accessible |
Cloud Security Posture Management(CSPM)
Choose the compliance conditions that must trigger notifications.
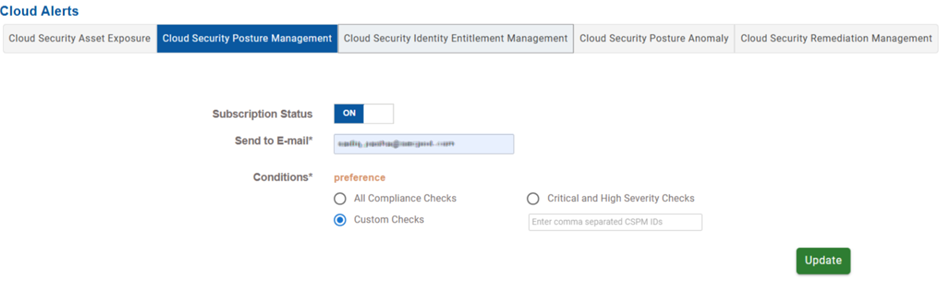
| Condition | Function |
|---|---|
| All compliance checks | Triggers alert for all types of compliance deviations detected by CSPM |
| Critical and High Severity Checks | Limits alerts to only the most severe or critical compliance failures |
| Custom Checks | Allows users to manually enter specific CSPM check IDs (comma-separated) that they want to be alerted on. Useful for focusing on controls aligned with specific regulatory or business priorities. |
Cloud Identity Entitlement Management(CIEM)
Choose the type of identity or permission-related events that trigger alerts.
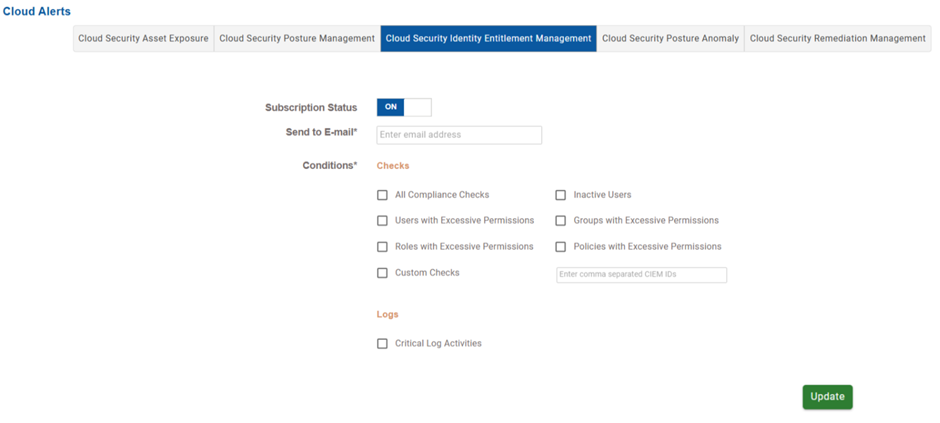
Alert Criteria for CIEM is organized into 2 categories namely Checks and Logs.
| Condition for Checks | Function |
|---|---|
| All Compliance Checks | Alerts for all entitlement-related security and policy violations |
| Users with Excessive Permissions | Detects and alerts when individual user accounts have more permissions than necessary |
| Roles with Excessive Permissions | Detects and alerts when individual roles have more permissions than necessary |
| Custom Checks | Entering specific CIEM check IDs (comma-separated) triggers alerts on targeted conditions |
| Inactive Users | Alerts when users have been idle for a set period but still retain permissions |
| Groups with Excessive Permissions | Detects and alerts when groups have more permissions than necessary |
| Policies with Excessive Permissions | Triggers alerts when permission policies allow overly broad or risky actions |
| Condition for Logs | Function |
|---|---|
| Critical Log Activities | Triggers alerts for key events in access or permission logs, such as role changes, privilege escalation, or unauthorized access attempts |
Cloud Security Posture Anomaly(CSPA)
Choose the alerts related to unusual behavior or deviations in the cloud environment.
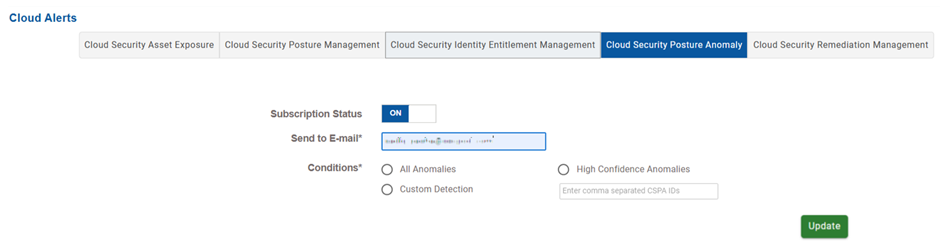
Choose the scope of anomaly detection.
| Condition for Logs | Function |
|---|---|
| All Anomalies | Triggers alerts for every detected anomaly, irrespective of the confidence level or severity. |
| High Confidence Anomalies | Triggers alerts only for anomalies that meet high-certainty thresholds (reduced false positives) such as unauthorized access from unusual location. For example, Saner Cloud has detected a login attempt to an administrator account from an IP address located in a foreign country that has never been associated with the organization. This login occurred outside of business hours. Furthermore, the same account had just successfully logged in from the corporate network a few minutes earlier. Given that this activity significantly deviates from the user’s typical behavior and involves a privileged account, it meets the criteria for high-certainty anomalous behavior. As a result, the system triggers a high-confidence alert, reducing the likelihood of a false positive. |
| Custom Detection | Allows input of specific CSPA anomaly IDs (comma-separated) |
Cloud Security Remediation Management(CSRM)
Choose the alert notifications related to remediation actions taken in response to cloud security issues.
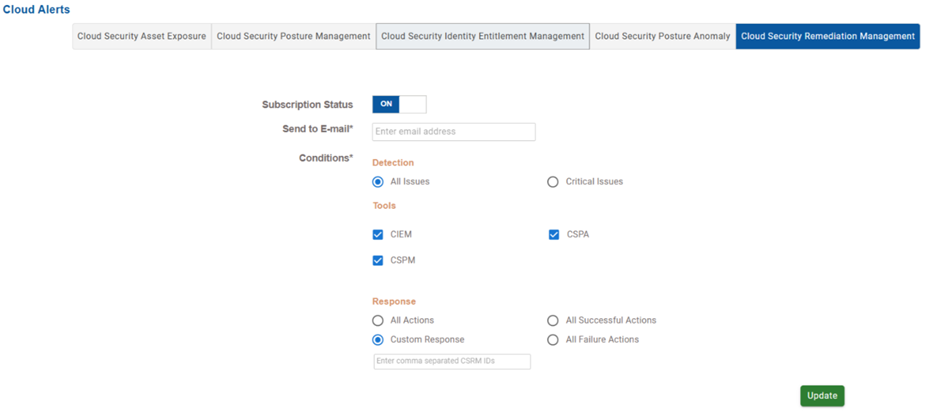
The configuration conditions are classified into three sections: Detection, Tools, and Response.
| Condition | Function |
|---|---|
| Detection | If the detection condition is “All Issues”, then the system triggers alerts for any remediation-worthy issue, irrespective of the severity If the detection condition is “Critical Issues”, then the system restricts alerts to only critical or high-severity findings. |
| Tools | The tools from which remediation issues are detected. One or more tools can be selected to include different detection sources in the subscription. |
| Response | Determines the types of remediation outcomes that triggers alerts: All Actions include successful, failed, and ongoing remediations All Successful Actions alerts only when remediations are completed successfully All Failure Actions alerts only on failed or blocked remediation attempts. Custom Response allows the user to enter specific CSRM IDs (comma-separated) for targeted alerting. |
Step 5: Setup Response
Select the checkbox to specify the automated response for the alert.
| Tool | Response |
|---|---|
| Asset Exposure | Not Applicable |
| Remediation Management | All actions, All successful actions, All failure actions, Custom Response |
| Identity Entitlement Management | Not Applicable |
| Posture Anomaly | All Anomalies, High Confidence Anomalies, Custom Detection |
| Posture Management | Not Applicable |
Step6: Complete Your Configuration
Click the Update button to complete your alert setup. The successful completion message displays and notifications trigger based on your setup.
Commonly Asked Questions
What are Alerts in SanerCloud and why are they important?
Alerts in SanerCloud notify administrators and stakeholders about specific issues or events that call for immediate attention or remediation.
What are the different types of alerts in SanerCloud?
Follow the link to: Learn About the different types of Alerts and their Purpose in SanerCloud
Why am I not receiving the cloud alerts even though conditions are met?
— Check the notification recipient ids are configured correctly
— Check if notification recipient ids has the appropriate permissions
— Make sure the alerting condition is configured correctly
What are the pre-built conditions provided by SanerCloud?
SanerCloud offers pre-defined alert conditions based on standard compliance frameworks (e.g., CIS, HIPAA, PCI-DSS) and general security posture checks like missing patches, unauthorized access attempts, and exposed assets.
What are the different types of alerts I can configure?
— Asset Exposure Alerts: Detect when sensitive data or systems are exposed.
— Compliance Violation Alerts: Notify when systems deviate from compliance standards.
— Patch Management Alerts: Identify missing patches or vulnerabilities.
— Posture Anomaly Alerts: Highlight deviations from expected security configurations.
— Risk Management Alerts: Detect issues, threats, or vulnerabilities that need to be addressed or fixed within a system or network.
How does the subscription-enabled model in SanerCloud affect alert configuration?
Turning on the subscription enables users to setup the required alert conditions for any SanerCloud tool.
Can I set up alerts across multiple SanerCloud tools simultaneously?
Yes, SanerCloud integrates various security tools under one dashboard, allowing centralized alert configuration across all services tied to your subscription.
Are there limitations to the number of alerts I can configure under my subscription?
This may vary based on the subscription plan you have opted for.
Can I perform patch remediation directly from an alert notification?
Users can only review the details from the alert notification and log into the application to take the necessary patch remediation actions.
What information can I find in the SanerCloud alert emails?
— The tool in SanerCloud that triggered the alert and the time of the activity
— Description about the specific activity detected
— Impacted Resources
Related Topics


