Introduction
This document provides the prerequisites for onboarding to the Saner SaaS Platform, SecPod’s unified solution for managing vulnerabilities, exposures, and security risks across enterprise IT and cloud environments. The Platform is fully hosted and managed by SecPod, with no infrastructure deployment required from customers for the core platform.
Customers must prepare their environment to support the following components:
- Saner Agents: A lightweight agent installed on endpoints to collect asset inventory, detect vulnerabilities and misconfigurations, perform remediation, and execute endpoint operations
- Network Scanner: Performs unauthenticated or authenticated network-based scans to detect vulnerabilities and misconfigurations.
- Active Directory Scanner: Integrates with Active Directory (AD) to automate the discovery and organization of domain-joined devices, groups, and users. This simplifies agent deployment and aligns with your organizational structure.
- Virtual Device Scanners: A lightweight agent installed on virtual machines running in Cloud Service Provider (CSP) environments such as AWS and Azure enabling Saner SaaS Platform’s CWPP capabilities. These agents provide asset visibility, detect vulnerabilities and misconfigurations, perform remediation, and execute workload operations to protect cloud workloads.
- Cloud Scanners: A Saner SaaS Platform component that, once configured with the necessary credentials, scans native cloud resources across Cloud Service Providers (CSPs) such as AWS and Azure to provide comprehensive visibility into security risks, misconfigurations, asset exposure, identity entitlements, and overall cloud security posture.
- External Scanners: A cloud-based scanner within the Saner Platform that, once configured, scans external-facing infrastructure to provide visibility into exposed assets and associated security risks, including vulnerabilities and misconfigurations.
- Patch Repository (Saner CPR): An optional, secure, on-premises patch repository hosted within the customer environment and maintained by SecPod. It provides trusted, internal access to OS and third-party patches for Windows and Linux platforms, optimizing bandwidth and ensuring endpoints do not require direct internet connectivity for patch downloads.
This document details the system requirements, supported operating systems, network configurations, and security considerations required to successfully deploy Saner Agents, onboard cloud workloads, and configure both cloud and external scanners, ensuring seamless communication with the Saner SaaS Platform.
Following these prerequisites ensures successful onboarding and optimal operation of Saner CVEM (Continuous Vulnerability & Exposure Management), CNAPP (Cloud-Native Application Protection Platform), and CWPP (Cloud Workload Protection Platform) within your environment.
Saner SaaS Platform and Component Architecture
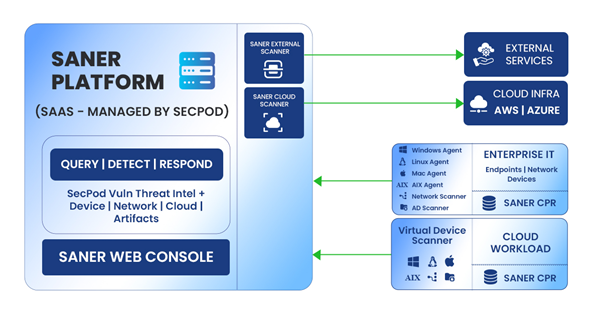
- Saner SaaS Platform: The Saner SaaS Platform is a fully managed and hosted by SecPod. It acts as the central controller for asset management, data collection, remediation orchestration, and security operations. The integrated analytical and correlation engine continuously processes scan data to identify vulnerabilities, misconfigurations, and risks, providing prioritized, actionable insights across CVEM, CNAPP, and CWPP capabilities.
- Saner Web Console: The Saner Web Console is a cloud-hosted, browser-based interface that provides administrators with centralized visibility and control over their security operations. It enables users to access real-time dashboards, generate reports, configure policies, initiate scans, and monitor remediation activities across CVEM, CNAPP, and CWPP environments.
- Scanners: The Saner SaaS Platform incorporates multiple scanners designed to collect data, assess risks, and maintain security across enterprise and cloud environments. These scanners operate in various locations and communicate securely with the Saner SaaS Platform to centralize data and manage remediation actions.
- Saner Agent: A lightweight agent installed on endpoints within enterprise networks. It collects system data, detects vulnerabilities and misconfigurations, enforces security policies, and applies patches. The agent initiates secure, outbound communication to the Saner Platform over port 443 (HTTPS).
- Network Scanner: Performs authenticated or unauthenticated scans of network devices to detect vulnerabilities and misconfigurations. Requires local network access to target devices. An existing Saner Agent can be designated to function as the Network Scanner.
- Active Directory Scanner: Discovers domain-joined organizational units (OUs), groups, and devices to simplify agent deployment and align with your organizational structure. Uses a secure, outbound connection to query Active Directory over port 636 (TCP) using LDAPS.
- Virtual Device Scanner: A lightweight agent deployed on virtual devices running on Cloud Service Providers (CSPs) environment such as AWS or Azure to protect Cloud workloads. It collects system data, detect vulnerabilities and misconfigurations, enforces security policies, and apply patches. The agent initiates secure, outbound communication to the Saner SaaS Platform over port 443 (HTTPS).
- Cloud Scanner: A managed component hosted within the Saner SaaS Platform that performs agentless, API-driven scans of native cloud resources across CSPs. It uses authorized API calls to discover assets, detect misconfigurations, and assess posture risks, supporting CNAPP capabilities including CSAE, CSAP, CSPM, CIEM, and CSRM.
- External Scanner: A cloud-hosted component of the Saner SaaS Platform designed to assess internet-facing infrastructure. It scans public IPs, domains, and external services to identify vulnerabilities, misconfigurations, and potential risks—without requiring any agent deployment or outbound access configuration from customer environments.
- Patch Repository (Optional): Saner CPR (Consolidated Patch Repository) is a secure, on-premises patch repository hosted within the customer environment and maintained by SecPod. The Saner CPR establishes secure outbound connections to vendor patch repositories to fetch OS patches for Windows and Linux platforms, and connects to Saner SaaS Platform hosted repositories to retrieve third-party patches. Saner Agents and Virtual Device Scanners are configured to download patches directly from the CPR over the internal network, ensuring faster deployments and compliance with organizational security policies.
Data Flow and Connectivity Summary
| Source | Destination | Direction | Protocol /Port | Mandatory / Optional | Purpose |
| Saner Agent | Saner SaaS Platform | Outbound | HTTPS/443 | Mandatory | Sends inventory, scan results; receives jobs, policies, and security updates for endpoints. |
| Saner Agent | Saner CPR | Outbound | HTTPS/443 (configurable) | Optional | Fetches OS and third-party patches if Saner CPR is deployed |
| Virtual Device Scanner | Saner SaaS Platform | Outbound | HTTPS/443 | Mandatory | Sends inventory, scan results; receives jobs, policies, and security updates for cloud-hosted workloads. |
| Virtual Device Scanner | Saner CPR | Outbound | HTTPS/443 (configurable) | Optional | Fetches OS and third-party patches if Saner CPR is deployed |
| Saner CPR | Vendor Patch Repositories (OS patches) | Outbound | HTTP/80 HTTPS/443 | Optional | Downloads OS patches from vendor repositories |
| Saner CPR | SecPod-hosted Third-Party Patch Repository | Outbound | HTTPS 443 | Optional | Downloads third-party patches from Saner SaaS Platform |
| Active Directory Scanner | Active Directory | Outbound | LDAPs/636 | Optional | Secure directory queries to discover domain-joined devices, groups, and users. |
| Network Scanner | Target Devices | Outbound | Depends on Network scan profile | Optional | Performs authenticated or unauthenticated scans on network devices. |
| Cloud Scanner | Cloud Service Provider API Endpoints | Outbound | HTTPS/443 | Mandatory | Agentless discovery and posture assessment via authorized cloud-native APIs. |
| External Scanner | Public-facing Assets | Outbound | Depends on Network scan profile | Optional | Scans internet-exposed domains, IPs, and public services for vulnerabilities and misconfigurations. |
Saner web console and Prerequisites
Browser Requirements
- Google Chrome
- Microsoft Edge
- Mozilla Firefox
- Apple Safari
Network Requirements
- The web console is accessed over HTTPS (port 443) via the public domain
- https://saner.secpod.com (Global SaaS Platform)
- https://eu.saner.secpod.com (EU Region SaaS Platform)
- https://uk.saner.secpod.com (UK Region SaaS Platform)
- https://in.saner.secpod.com (India Region SaaS Platform)
- Ensure outbound HTTPS traffic is allowed from the administrator’s network to the above domains.
Display Resolution
- Minimum recommended screen resolution: 1366 x 768
- For best experience, use 1920 x 1080 or higher.
Authentication Requirement
- Valid Saner subscription and login credentials.
Security Settings
Avoid browser extensions that block scripts or modify DOM elements, as these can interfere with dashboard rendering.
Saner Agent Prerequisites
Operating System Support
Saner Agent is supported on Windows, Linux (dpkg, rpm), macOS, and AIX platforms. For the complete list of supported operating system versions, refer to: Supported Operating Systems
System Requirements
| Operating System | Disk Space | Memory | Privileges Required |
| Windows | 800 MB | 400 MB | Administrator |
| Linux | 800 MB | 400 MB | root or equivalent privileges |
| macOS | 800 MB | 400 MB | root or equivalent privileges |
| AIX | 800 MB | 400 MB | root or equivalent privileges |
| Note Ensure sufficient disk space is available during patch download or remediation workflows |
Network Access Requirements
Saner Agent establishes secure outbound connections to the Saner SaaS Platform and associated content delivery services hosted by SecPod. These connections are required for agent-server communication, security intelligence synchronization, and patch content downloads.
Ensure that your organization’s firewall or proxy configuration allows HTTPS (port 443) access to the following Saner SaaS Platform URL based on your deployment region.
Global SaaS Platform
| Saner SaaS Platform URL | Port | Protocol | Direction | Purpose |
| https://saner.secpod.com | 443 | HTTPS | Outbound | Agent-to-server communication |
| https://resources.secpod.com | 443 | HTTPS | Outbound | Downloading Security Intelligence and related resources |
Validation
curl -v https://saner.secpod.com
curl -v https://resources.secpod.comExpected Output
- Connection should succeed.
- Look for HTTP/2 200 or HTTP/1.1 200 OK in the response headers.
Validation (Via Proxy)
curl -v -x http://<proxy-server>:<port> https://saner.secpod.com
curl -v -x http://<proxy-server>:<port> https://resources.secpod.com
Replace <proxy-server>:<port> with your proxy details.Expected Output
Look for HTTP/2 200 or HTTP/1.1 200 OK in the response headers.
Connection should succeed.
EU SaaS Platform
| Saner SaaS Platform URL | Port | Protocol | Direction | Purpose |
| https://eu.saner.secpod.com | 443 | HTTPS | Outbound | Agent-to-server communication |
| https://eu.resources.secpod.com | 443 | HTTPS | Outbound | Downloading Security Intelligence and related resources |
Validation
curl -v https://eu.saner.secpod.com
curl -v https://eu.resources.secpod.comExpected Output
Look for HTTP/2 200 or HTTP/1.1 200 OK in the response headers.
Connection should succeed.
Validation (Via Proxy)
curl -v -x http://<proxy-server>:<port> https://eu.saner.secpod.com
curl -v -x http://<proxy-server>:<port> https://eu.resources.secpod.com
Replace <proxy-server>:<port> with your proxy details.Expected Output
- Connection should succeed.
- Look for HTTP/2 200 or HTTP/1.1 200 OK in the response headers.
UK SaaS Platform
| Saner SaaS Platform URL | Port | Protocol | Direction | Purpose |
| https://uk.saner.secpod.com | 443 | HTTPS | Outbound | Agent-to-server communication |
| https://uk.resources.secpod.com | 443 | HTTPS | Outbound | Downloading Security Intelligence and related resources |
Validation
curl -v https://uk.saner.secpod.com
curl -v https://uk.resources.secpod.comExpected Output
- Connection should succeed.
- Look for HTTP/2 200 or HTTP/1.1 200 OK in the response headers.
Validation (Via Proxy)
curl -v -x http://<proxy-server>:<port> https://uk.saner.secpod.com
curl -v -x http://<proxy-server>:<port> https://uk.resources.secpod.com
Replace <proxy-server>:<port> with your proxy details.Expected Output
- Connection should succeed.
- Look for HTTP/2 200 or HTTP/1.1 200 OK in the response headers.
IN SaaS Platform
| Saner SaaS Platform URL | Port | Protocol | Direction | Purpose |
| https://in.saner.secpod.com | 443 | HTTPS | Outbound | Agent-to-server communication |
| https://in.resources.secpod.com | 443 | HTTPS | Outbound | Downloading Security Intelligence and related resources |
Validation
curl -v https://in.saner.secpod.com
curl -v https://in.resources.secpod.comExpected Output
- Connection should succeed.
- Look for HTTP/2 200 or HTTP/1.1 200 OK in the response headers.
Validation (Via Proxy)
curl -v -x http://<proxy-server>:<port> https://in.saner.secpod.com
curl -v -x http://<proxy-server>:<port> https://in.resources.secpod.com
Replace <proxy-server>:<port> with your proxy details.Expected Output
- Connection should succeed.
- Look for HTTP/2 200 or HTTP/1.1 200 OK in the response headers.
Additional Notes
- Outbound HTTPS traffic must support TLS 1.2 or higher.
- If
curlreturns errors likeConnection refused,403 Forbidden, or TLS handshake failures, verify firewall, proxy, or SSL interception policies. - For customers using SSL interception or forward proxies, ensure these endpoints are excluded from inspection or have proper root certificates installed.
Antivirus, EPP, and EDR Exclusions
Saner Agent performs continuous vulnerability assessment, compliance checks, remediation actions and endpoint monitoring. To ensure these tasks are not disrupted by antivirus (AV), endpoint detection and response (EDR), or endpoint protection platforms (EPP), you must exclude specific binaries and directories.
Why Exclusions are Needed
- Prevent agent binaries from being quarantined, delayed, or flagged as suspicious.
- Avoid interference during scans, checks, remediation action and endpoint monitoring.
- Ensure timely completion of scanning and remediation tasks.
Required Exclusions
Windows
Directory
C:\Program Files\SecPod Saner\
C:\ProgramData\SecPod Saner\
Executables
spdialogbox.exe
spdialogbox20.exe
spfileindexer.exe
spsanerrun.exe
spsaneruninstall.exe
spscriptrun.exe
spsaneragnt.exe
spscanmanager.exe
spagentwatchdog.exe
spupgradecontroller.exe
spldapmanager.exe
spfirmware32.exe
spfirmware64.exe
spdiagnostictool.exe
sptaskhandler.exe
spmessagebox.exeLinux, macOS, and AIX
Directory
/etc/saner/
/var/saner/
/var/log/saner/
/opt/saner/
/usr/lib64/saner (Linux only)
/usr/lib/saner (AIX only)
/usr/local/lib/saner (macOS only)
Executables
/usr/bin/spsaner.service
/usr/bin/spscanmanager
/usr/bin/spagentwatchdog
/usr/bin/spsanerupgradecontroller
/usr/bin/spscriptrun
/usr/bin/spmessagebox
/usr/sbin/spsaneragent
/usr/sbin/spdiagnostictool
/usr/sbin/sptaskhandlerSaner Remote Access
Saner Remote Access is an on-demand remote support tool included with Saner Endpoint Management (EM). In addition to the prerequisites listed for Saner Agent, the following additional requirements apply if you plan to use Saner Remote Access.
Network Requirements
In environments where direct P2P connections are not possible, Saner Remote Access uses relay servers to facilitate communication. Ensure the following URLs are whitelisted in your firewall or proxy settings:
| Deployment Region | Relay Server to Whitelist |
| Global SaaS (saner.secpod.com) | relay.secpod.com |
| EU SaaS (eu.saner.secpod.com) | eu.relay.secpod.com |
| UK SaaS (uk.saner.secpod.com) | uk.relay.secpod.com |
| India SaaS (in.saner.secpod.com) | in.relay.secpod.com |
Antivirus Exclusions
To ensure uninterrupted operation of Saner Remote Access, add the following executables to your antivirus exclusion list:
Windows
Directory
C:\ProgramData\SecPod Saner\remoteconnector
Executables
spremoteconnector.exeLinux & macOS
Directory
/opt/saner/spremoteconnector
Executables
/var/saner/bin/spremoteconnectorActive Directory Scanner Prerequisites
Saner Agent can be designated as Active Directory Scanner. Ensure that your organization’s firewall or proxy configuration allows outbound to TCP access from designated Saner Agent to Active Directory (hostname or IP Address) using the ports specified below.
Network Prerequisites
| Hostname or IP Address | Port | Protocol | Direction | Purpose |
| Active Directory Server | 636 (recommended) | TCP | Outbound | Querying for users, groups, devices and OUs. |
| Active Directory Server | 389 (Optional) | TCP | Outbound | Querying users, groups, devices and OUs. |
| Note It is strongly recommended that port 636 (LDAPS) be used for communication with the Active Directory, as it provides secure, encrypted communication over TLS. Port 389 (LDAP) transmits data in plaintext and should only be used in trusted and internal networks. |
Network Scanner Prerequisites
Saner Agent can be designated as Network Scanner. In addition to the prerequisites listed for Saner Agent, the following additional requirements apply if you plan to use Network Scanner.
The following executable should be added to your antivirus exclusion list. The following executable should be added to your antivirus exclusion list.
Windows
Directory
C:\Program Files\SecPod Saner\
Executables
nmap.exe
npcap.exeLinux & macOS
Directory
/var/saner
Executables
/usr/bin/nmapresultmanager| Note Excluding nmap is necessary to prevent scans from being blocked or misclassified as intrusion attempts. |
Virtual Device Scanner Prerequisites
The Virtual Device Scanner operates on cloud-based virtual machines and shares the same prerequisites as the Saner Agent, including:
- Supported Operating Systems
- System Requirements
- Network Access Requirements
- Antivirus, EPP, and EDR Exclusions
- Patch Repository Requirements
For detailed prerequisites, refer to the Saner Agent Prerequisites section.
Cloud Scanner Prerequisites
Cloud Scanner is a managed component hosted within the Saner SaaS Platform by SecPod. There is no deployment or infrastructure setup required from your side. However, to enable successful operation, you must complete the following::
- Provide valid cloud account credentials with necessary API permissions for resource discovery and security assessment.
- Example:
- AWS: IAM Role or Access Key with permissions to describe resources, fetch configurations, and read entitlement details.
- Azure: Subscription Owner and Global Administrator with read-write privileges for onboarding.
API Permission Requirements
- You should verify that no API restrictions (such as IP allowlists, network policies, or firewall rules) prevent the Saner Cloud Scanner from accessing supported CSP APIs (AWS, Azure).
- Ensure required cloud APIs are enabled and accessible for inventory and posture assessments.
Defined Scope of Scanning
- Clearly identify which accounts, subscriptions, or resource groups you want the Cloud Scanner to assess.
External Scanner Prerequisites
The External Scanner is a managed component hosted within the Saner SaaS Platform. There is no deployment or infrastructure setup required from your side. To enable scanning, configure the public-facing IPs or domains, target ports, scan schedule, and Scan Policy. Additionally, ensure you have authorization to conduct scans on identified public resources
Patch Repository Requirements
Saner Agents and Virtual Device Scanners require access to patch repositories to download and apply missing patches during remediation. These repositories serve as the source for operating system and third-party application patches. Based on your environment and security requirements, Saner SaaS Platform supports multiple repository configurations.
OS Patch Repositories
Saner supports the following three options for delivering OS patches to endpoints and virtual devices:
Option 1 – Saner CPR (Consolidated Patch Repository) [Recommended]
Saner CPR is a secure, on-premises patch repository hosted within your environment and maintained by SecPod. It provides trusted, internal access to OS patches, eliminating the need for direct internet connectivity on endpoints.
- Saner CPR connects to vendor patch sources to download OS patches.
- Saner Agents and Virtual Devices fetch patches directly from Saner CPR over the internal network (HTTPS, configurable).
Use Cases
- Air-gapped deployments
- Bandwidth optimization
- Environments with strict security or compliance requirements
Option 2 – Organization-Managed Repositories
Organizations can configure endpoints and Virtual Device Scanners to fetch OS patches from existing internal repositories.
| Note For Red Hat systems, repository URLs differ based on the subscription model. Direct Red Hat subscriptions use the Red Hat CDN, whereas Satellite-managed environments must configure Satellite-specific repository URLs as per their internal setup. |
Option 3 – Vendor Cloud Repositories
Organizations can configure endpoints and Virtual Devices to fetch OS patches directly from vendor-hosted patch repositories over the internet.
| Note For Red Hat systems, repository URLs differ based on the subscription model. Direct Red Hat subscriptions use the Red Hat CDN, whereas Satellite-managed environments must configure Satellite-specific repository URLs as per their internal setup. |
Third-Party Application Patch Repositories
Saner supports the following options for delivering third-party application patches:
Option 1 – Saner CPR (Consolidated Patch Repository) [Recommended]
Saner CPR connects to the Saner SaaS Platform Hosted Repository to download third-party application patches, providing secure, internal access to patch content for endpoints and virtual devices.
- Saner CPR downloads third-party patches from Saner SaaS Platform Hosted Repository and provides internal access for endpoints.
- Ensures bandwidth optimization and removes the need for direct internet access on endpoints.
Option 2 – Saner SaaS Platform Hosted Repository
Endpoints and Virtual devices fetch third-party patches from Saner SaaS Platform Hosted repository.
- Supported over HTTPS
- Dynamically updated with latest patches and versions
- Regional mirrors (EU, UK, and IN) used based on customer SaaS location
Option 3 – Customer-Hosted Repository
Organizations can create an internal HTTP/HTTPS/FTP server to host patches downloaded from Saner SaaS Platform Hosted repository or other trusted sources.
Best Practices:
- Whitelist necessary URLs/domains in firewall/proxy settings
- Monitor repository availability to avoid remediation delays
- If using WSUS or internal repos, ensure they are regularly synced with upstream vendors
- For air-gapped deployments, sync patch content using staging servers or external media


