Published Date: January 17, 2026
We are excited to announce a major release, Saner CVEM 6.6, that introduces powerful enhancements across Network Scanning, Vulnerability Management, Patch & Compliance Management, Endpoint Management, and Platform Administration functions. This release focuses on scalability, operational efficiency, improved risk prioritization, and better user control.
1. Global Shared Network Scanner Service Pool
Network scanning is now more flexible and scalable with the introduction of a Global Shared Scanner Service Pool.
- Network scanners can be designated to a shared pool accessible across Organizations and Sites/Accounts within an Organization.
- Scanners in the pool are no longer bound to a single Site or Account and can be dynamically used wherever scanning services are required.
- Scan results are automatically published to the respective Site or Account where the scan was initiated.
- This is especially useful for scanning public-facing resources distributed across multiple Sites, Accounts, or even Organizations.
Benefit: Optimized scanner utilization and simplified scanning of distributed environments.
2. Distributed Network Scanning with Multi-Scanner Tasks
Network scanners can now participate in multiple scanning tasks.
- A single scanner can be associated with multiple scan schedules running at different times.
- Each scanning task supports its own scan policy and configuration.
- Scanners function as shared utilities rather than being locked to a single scan task.
Benefit: Improved efficiency, reduced idle time, and better resource utilization.
3. Remediation SLA for Vulnerabilities and Misconfigurations
Organizations can now define Remediation Service Level Agreements (SLAs).
- Create SLAs to track and enforce remediation timelines for vulnerabilities and misconfigurations.
- Vulnerabilities are traced from discovery through remediation.
- Track Mean Time to Remediate (MTTR) based on severity.
- Enables prioritization and clear remediation goals for operations teams.
- Reports provide visibility into SLA adherence and violations.
Benefit: Stronger accountability and measurable security outcomes aligned with organizational expectations.
4. End-User Patch Deferral Support (Patch & Compliance Management)
End users now have controlled flexibility during remediation.
- Users can postpone patching and remediation activities until a defined deadline.
- Helps avoid unplanned downtime and interruptions during active work.
- Users retain control over patch installation and reboot timing within allowed limits.
Benefit: Reduced productivity impact while maintaining compliance.
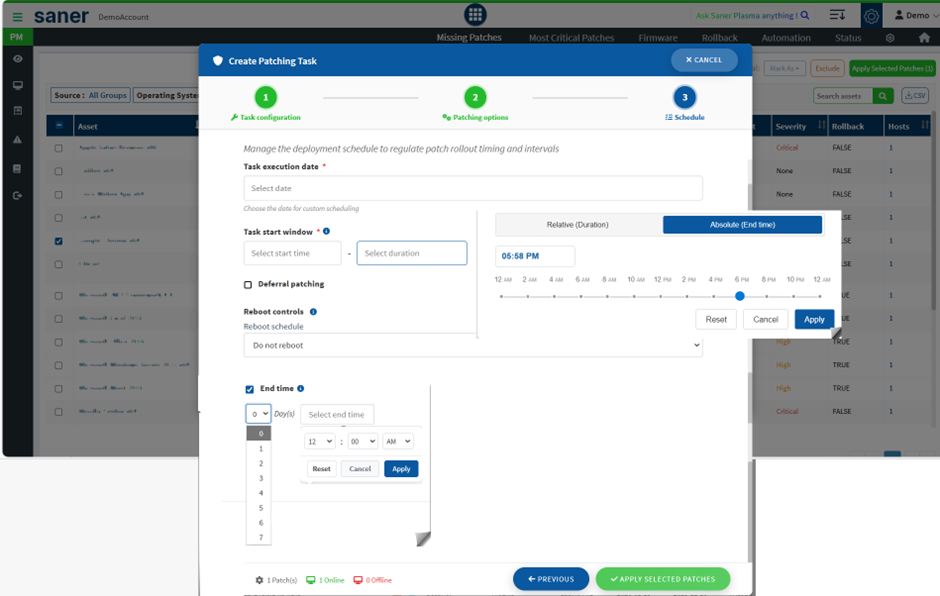
5. Enhanced Reboot and End-Time Scheduling Controls (Patch & Compliance Management)
Remediation jobs and automation rules now offer enhanced scheduling controls.
- Greater control over reboot behavior and job end times.
- Helps align remediation activities with maintenance windows and operational constraints.
Benefit: More predictable and user-friendly remediation execution.
6. Multi-Admin Support
Administrative responsibilities can now be safely delegated.
- Super Admins can designate multiple administrators within the organization.
- Administrative privileges can be delegated or revoked at any time.
Benefit: Improved operational resilience and reduced dependency on a single administrator.
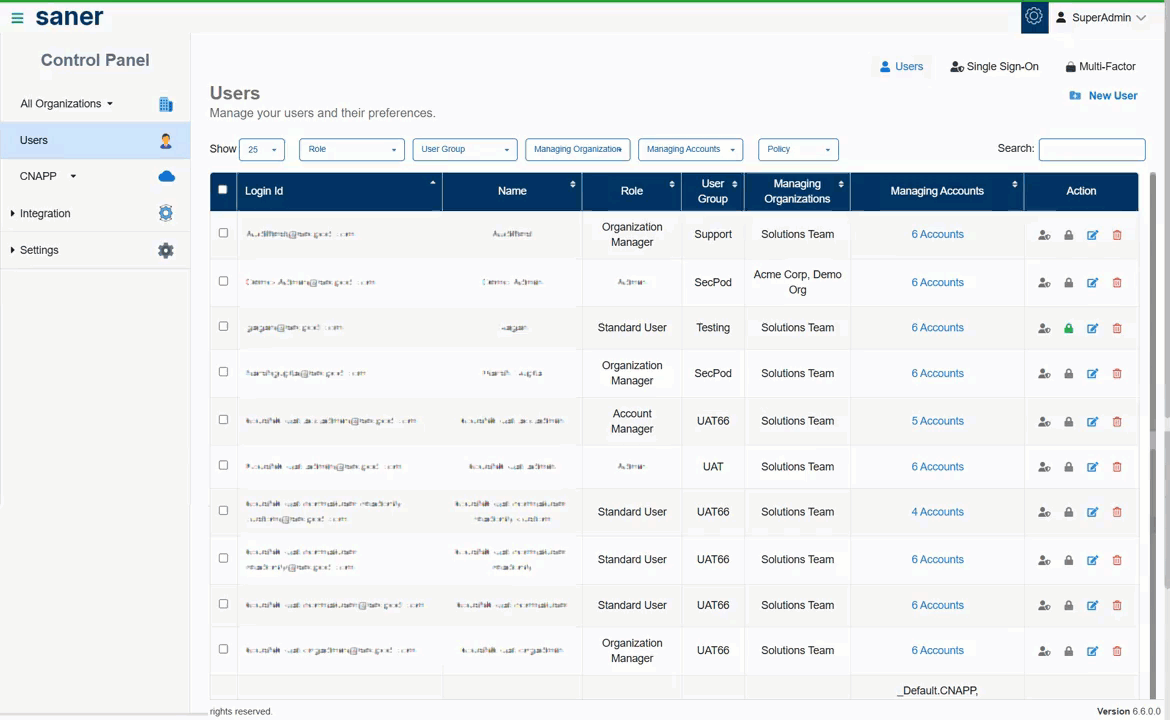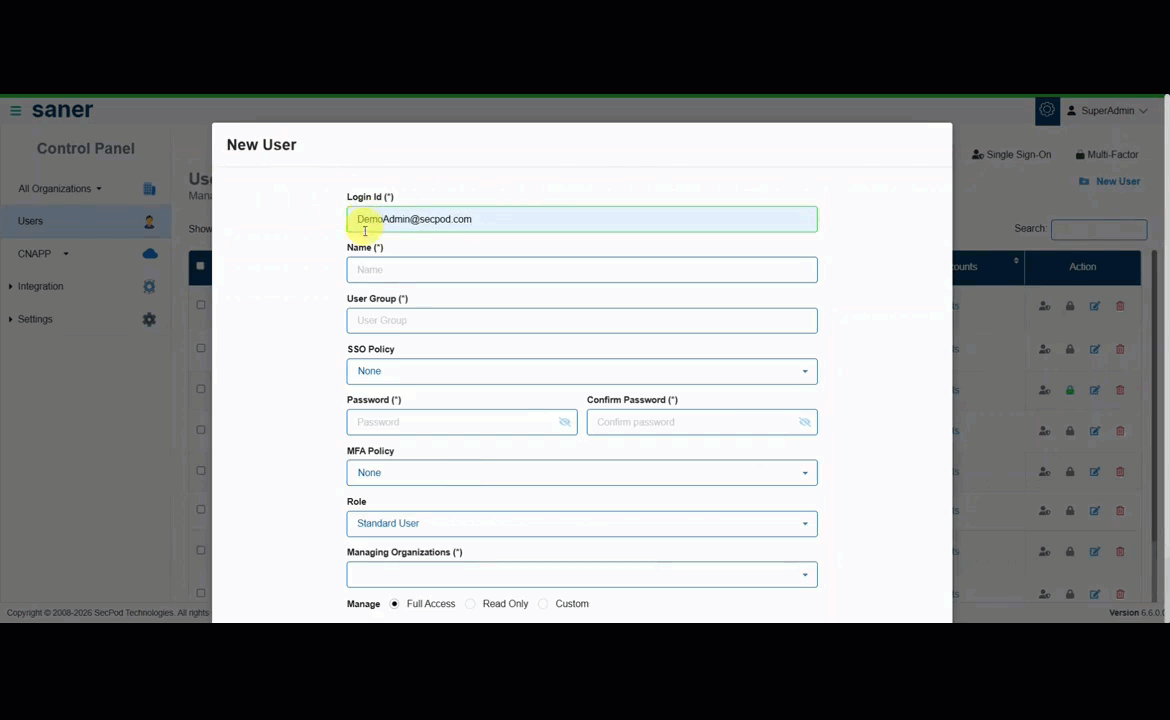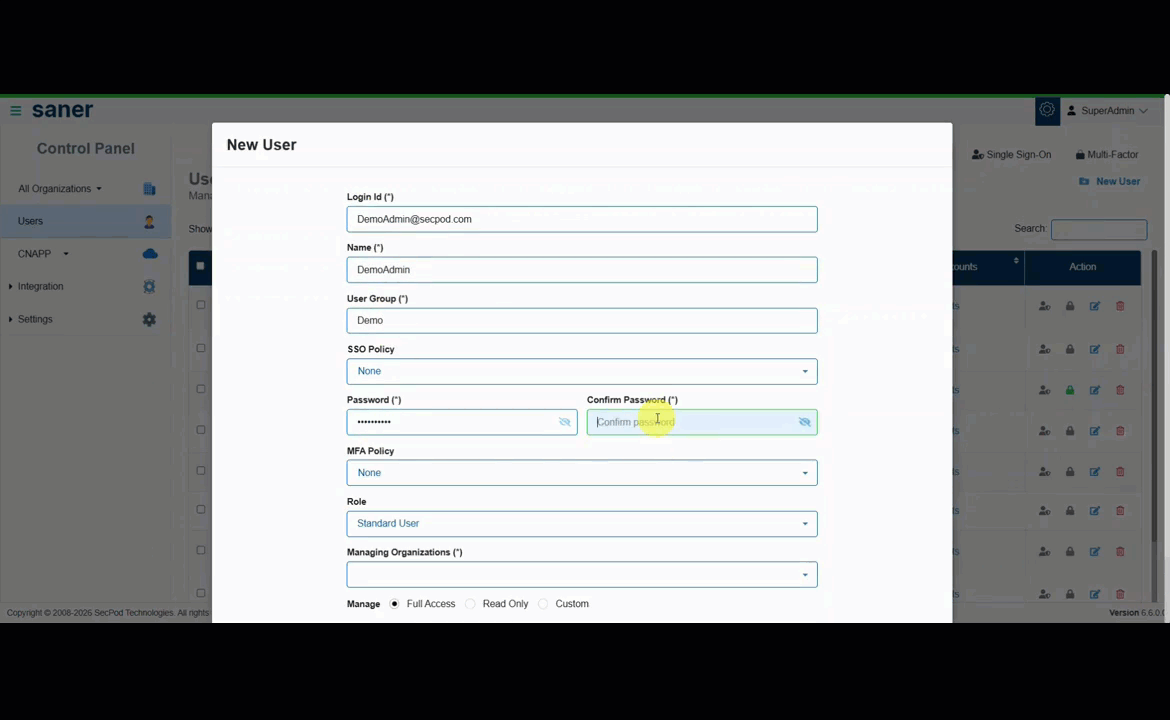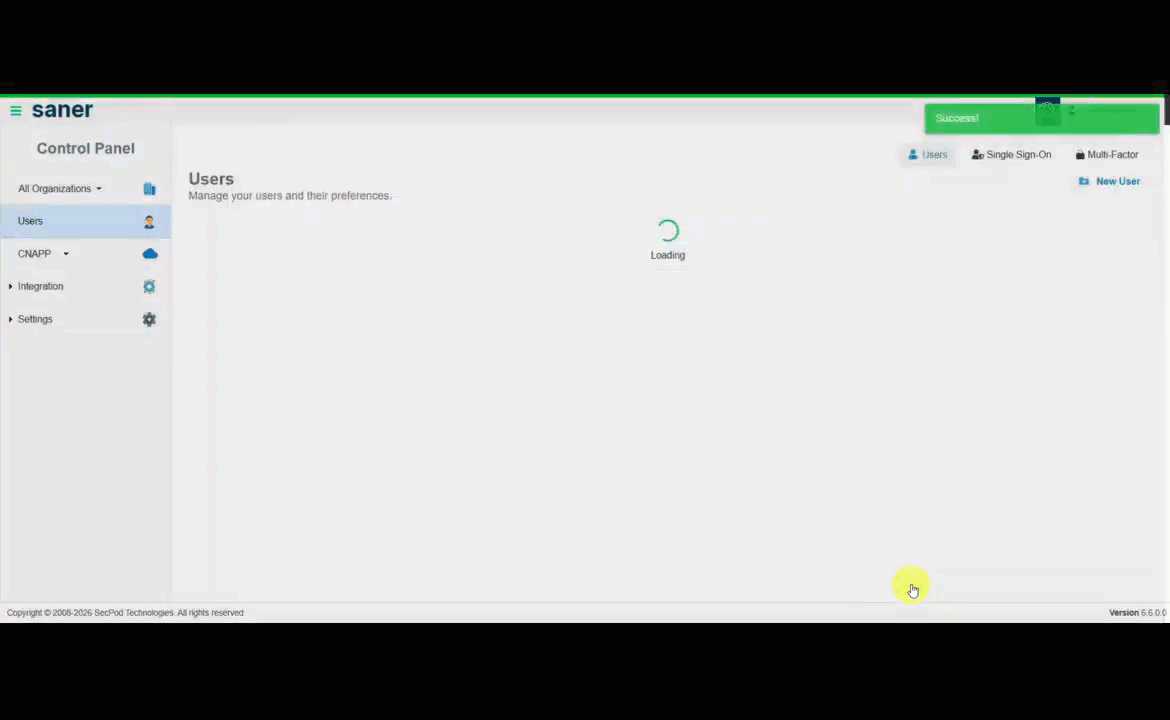
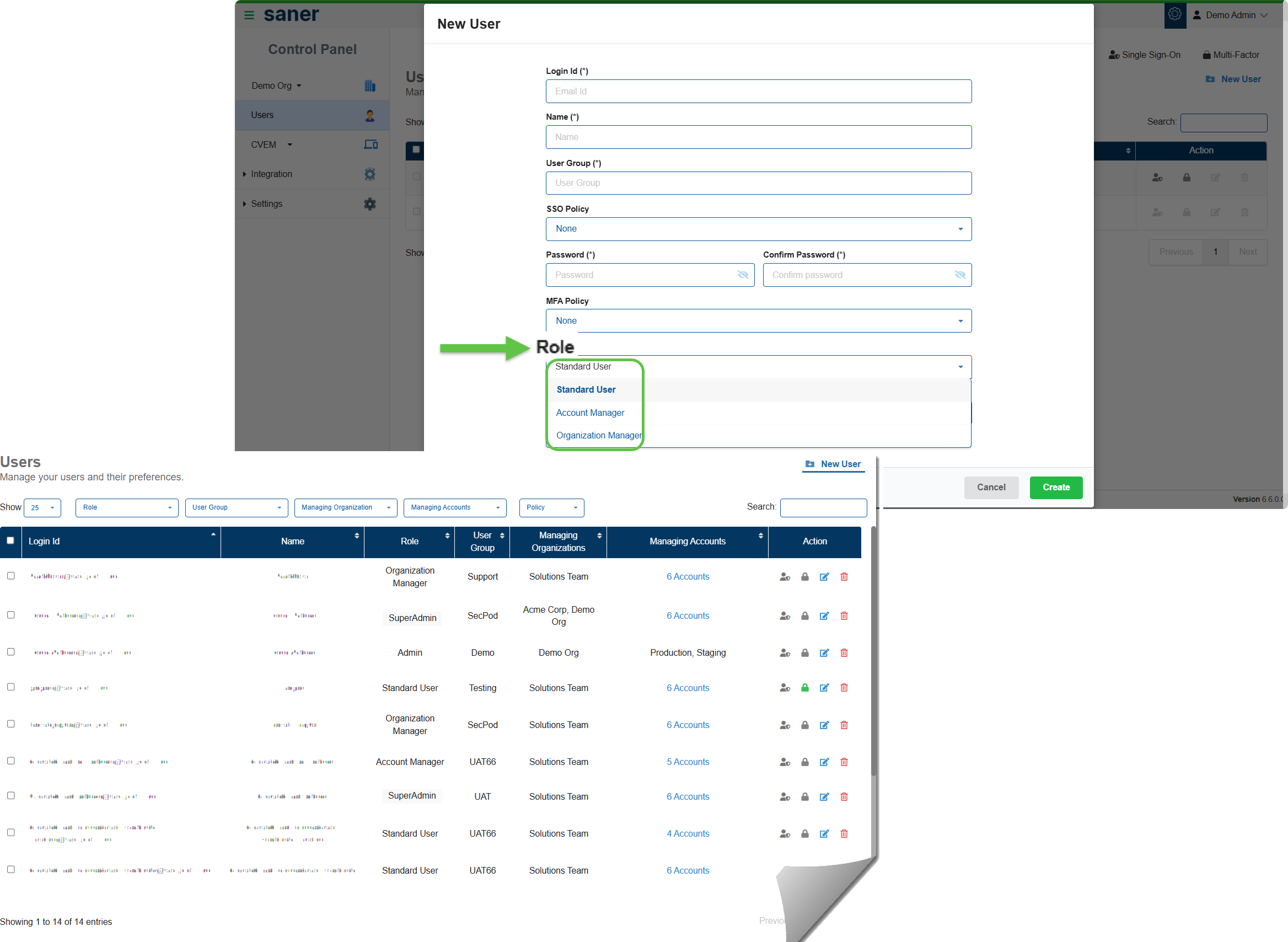
7. User Role Renaming for Improved Clarity
User roles have been renamed to better reflect responsibilities and hierarchy:
- Admin → Super Admin
- Modified role definition: Admin, designated by Super Admin
- Org Admin → Organization Manager
- Account Admin → Account Manager
- Normal User → Standard User
Benefit: Clearer role definitions and easier access management.
8. Authenticated Device Discovery
Device discovery is now more accurate and powerful with authenticated scanning.
- Support for multiple authentication schemes: SMB, SSH, HTTP
- Centralized credential management for reuse across discovery tasks
- Credentials can be assigned per device, device group, or via device tags
- Enhanced scheduling with time zone awareness and configurable scan start times
- Improved overall device discovery user experience
Benefit: Higher discovery accuracy and easier credential management at scale.
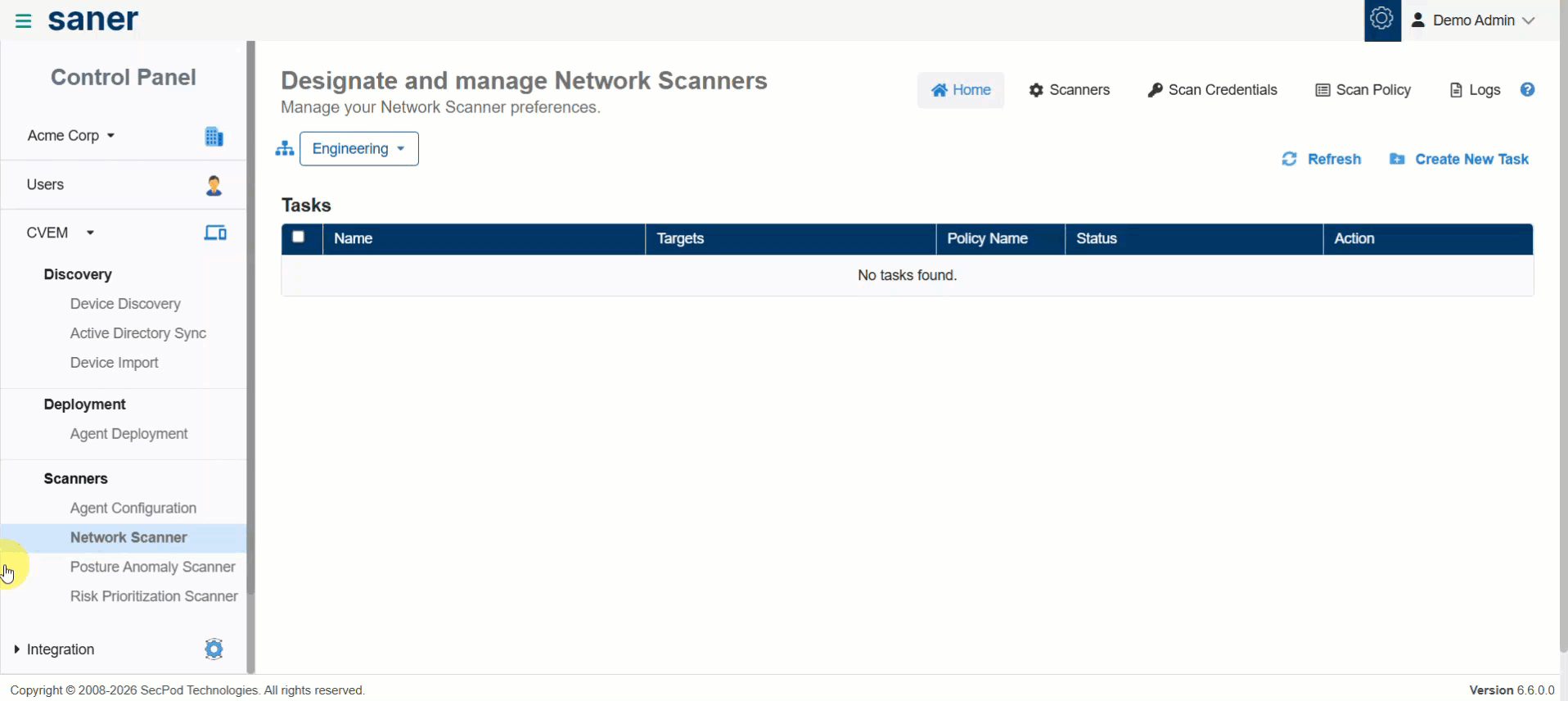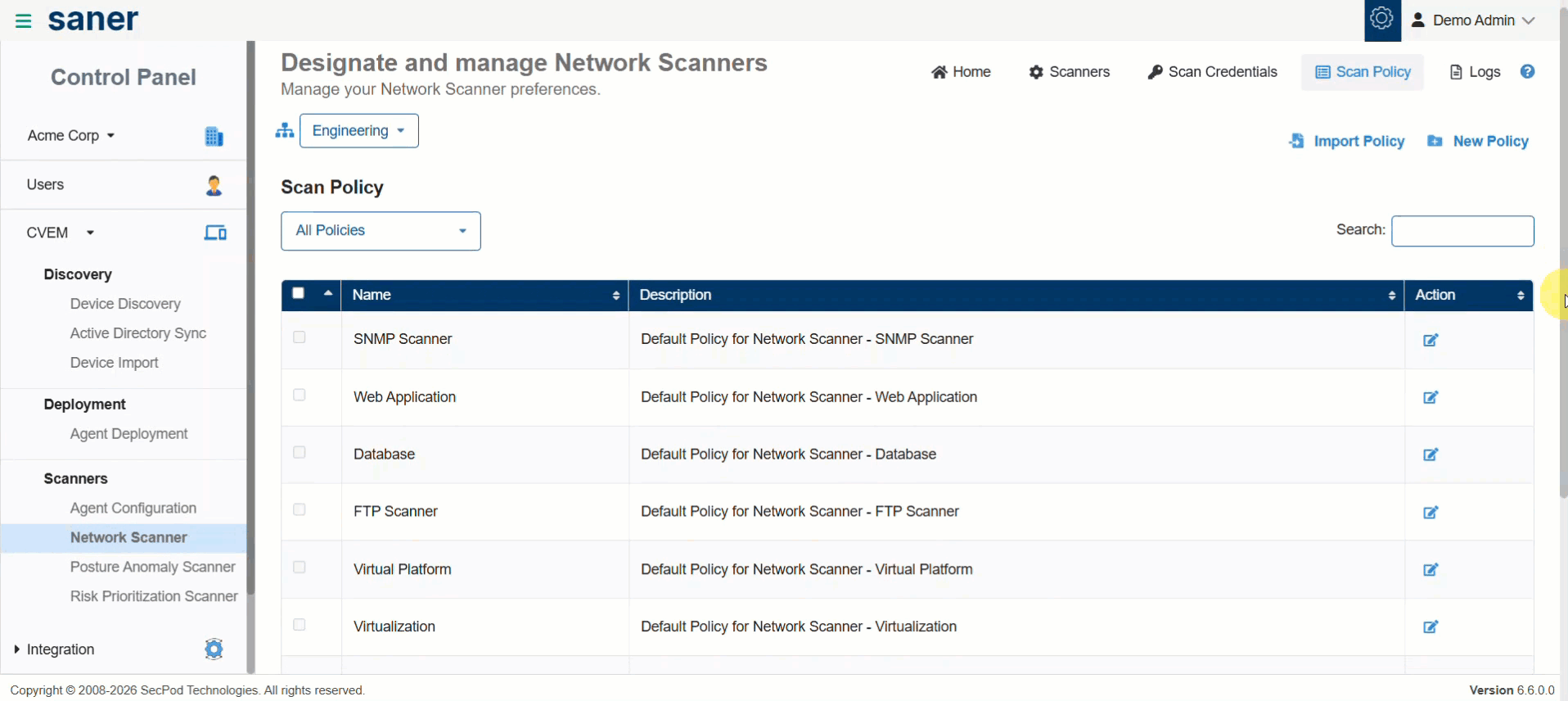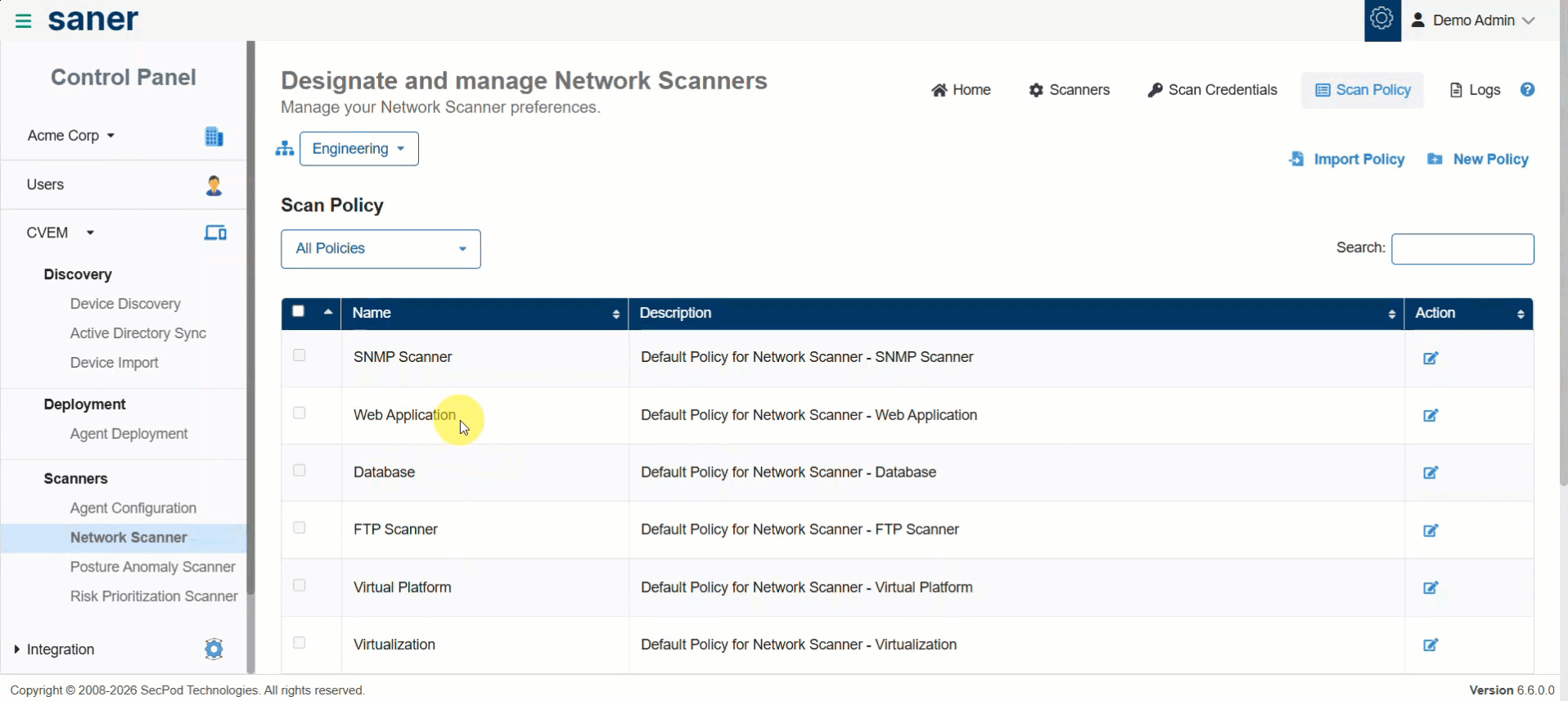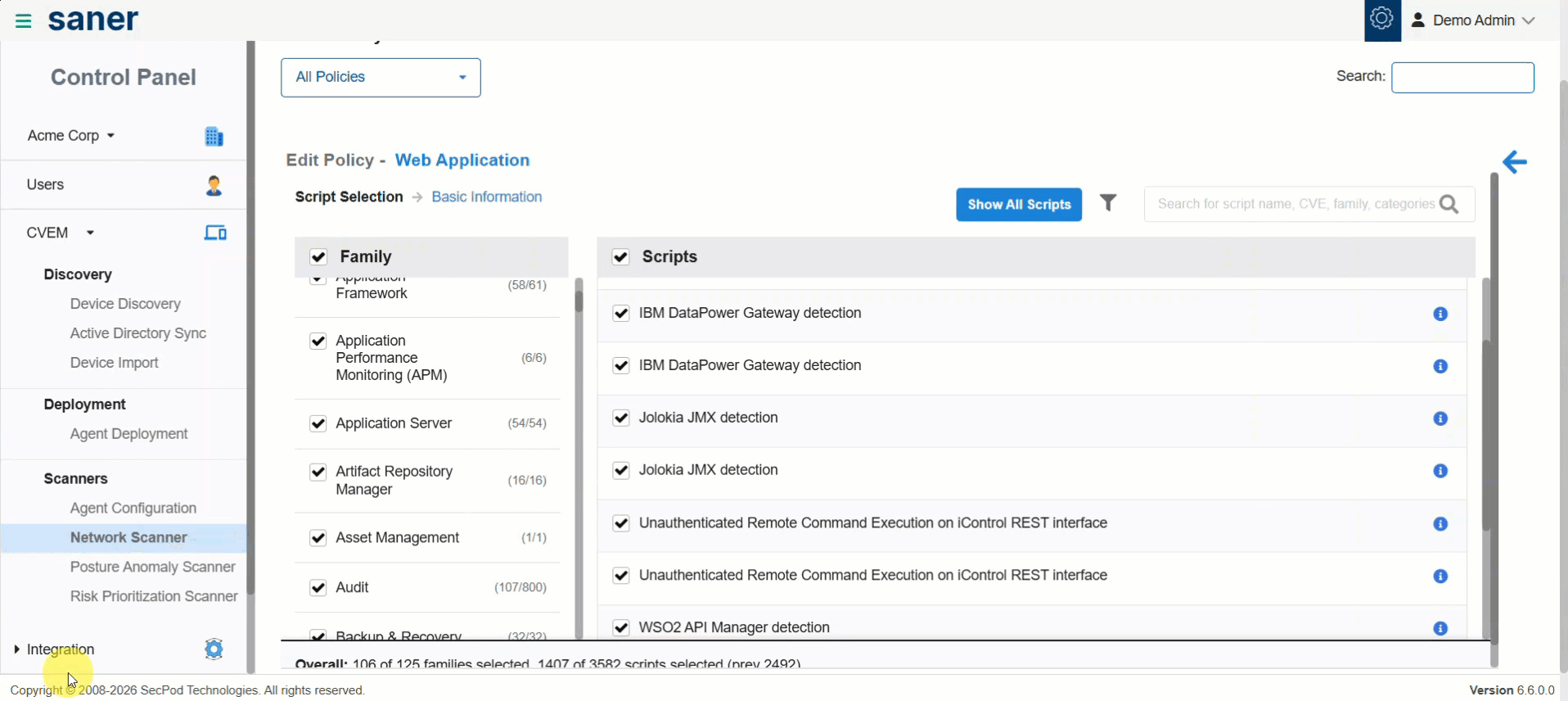
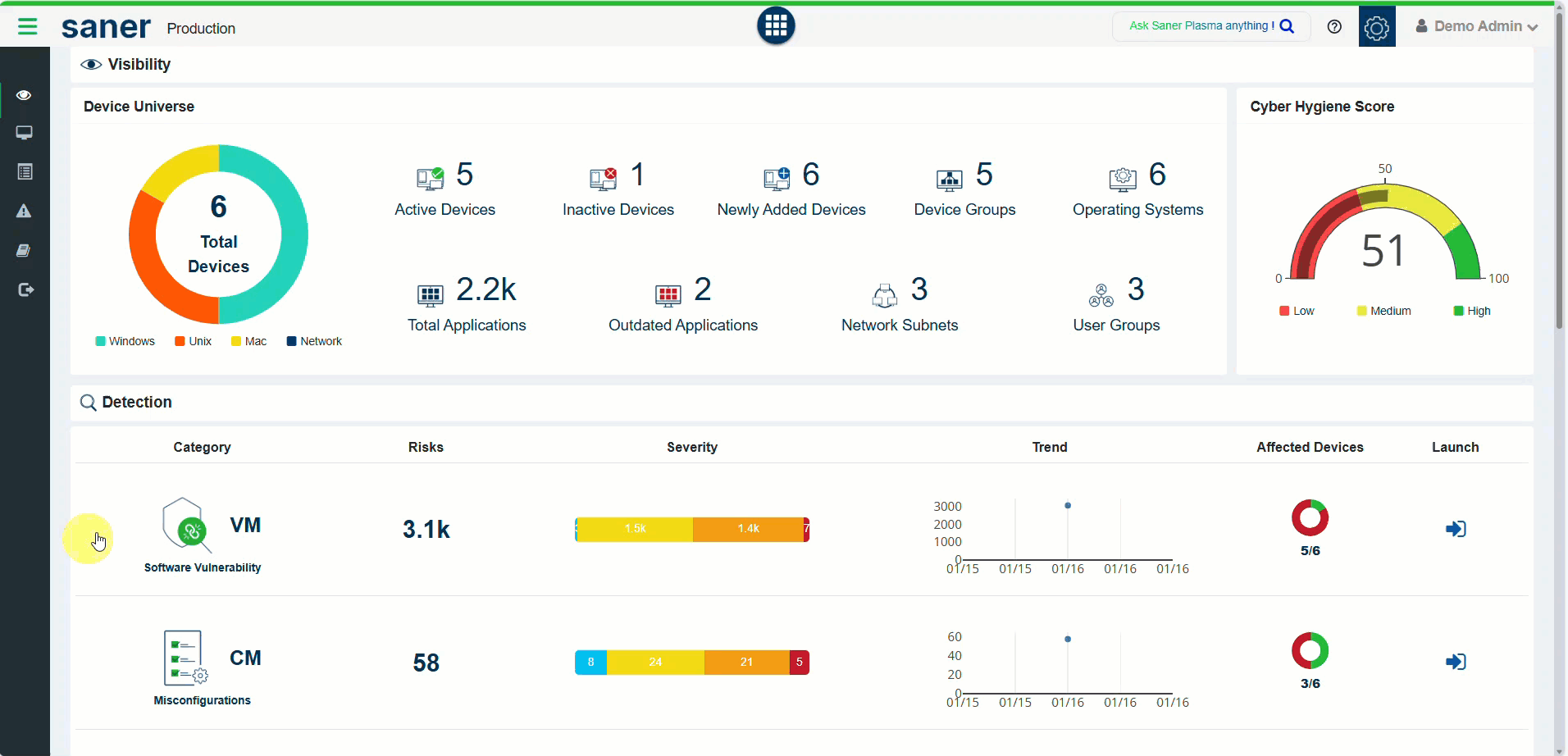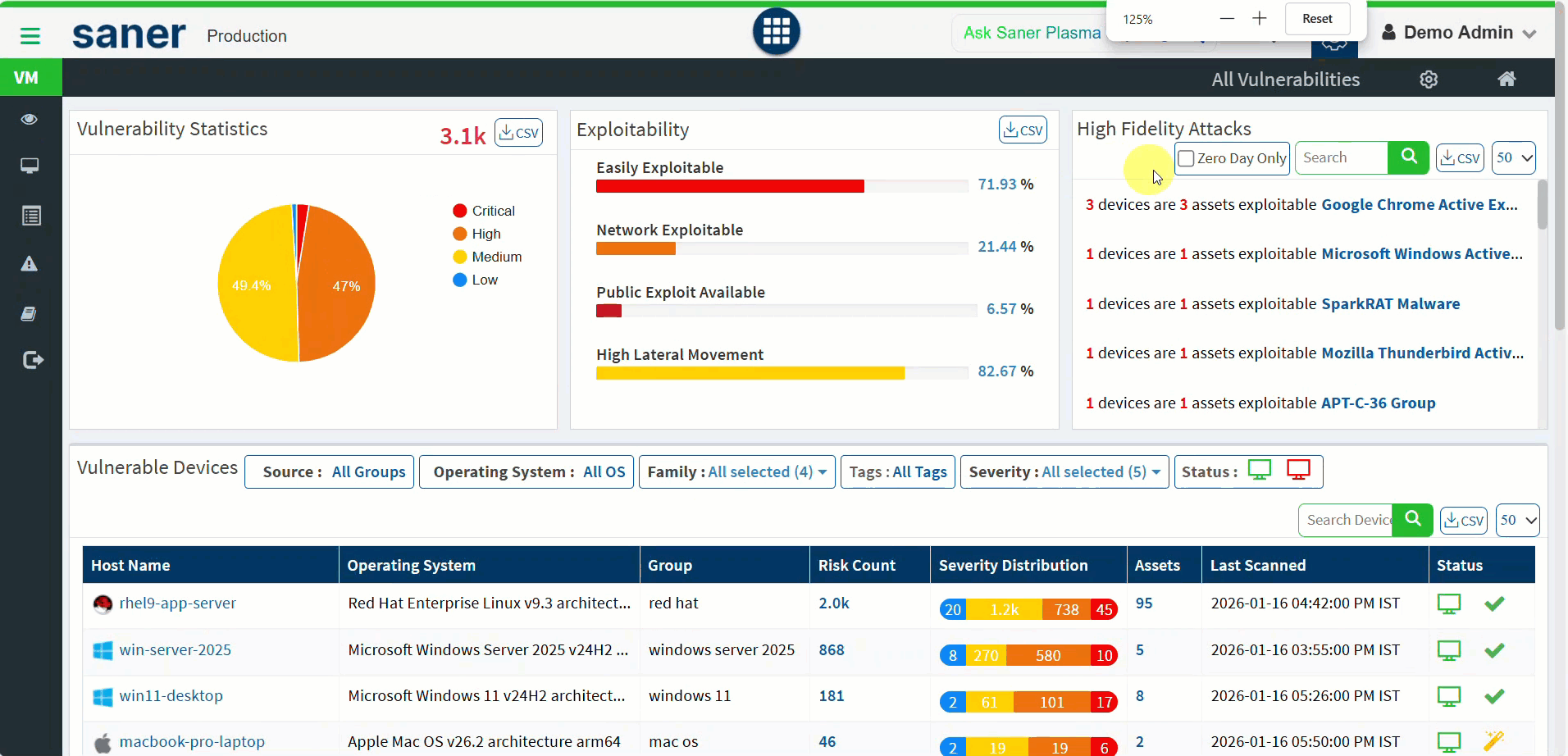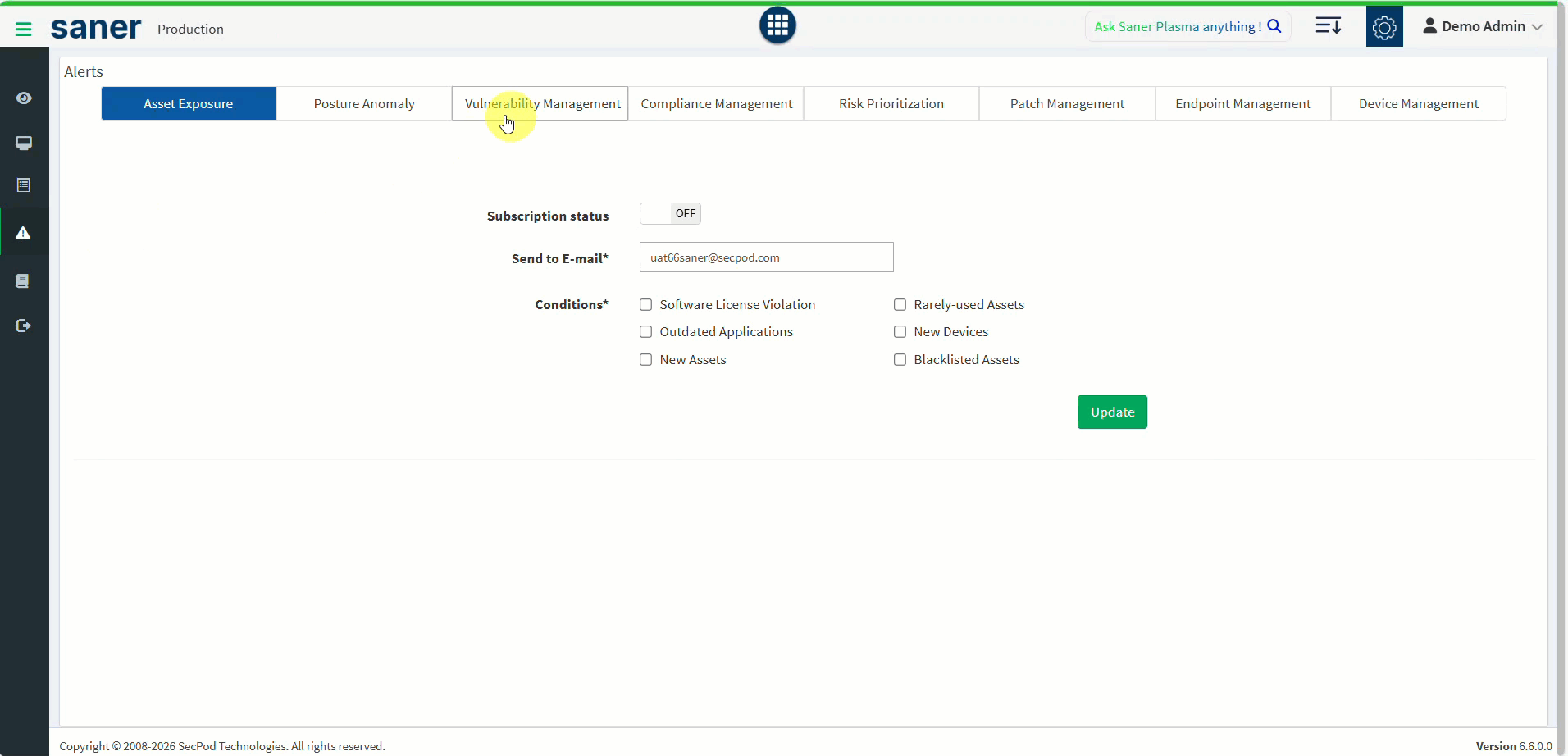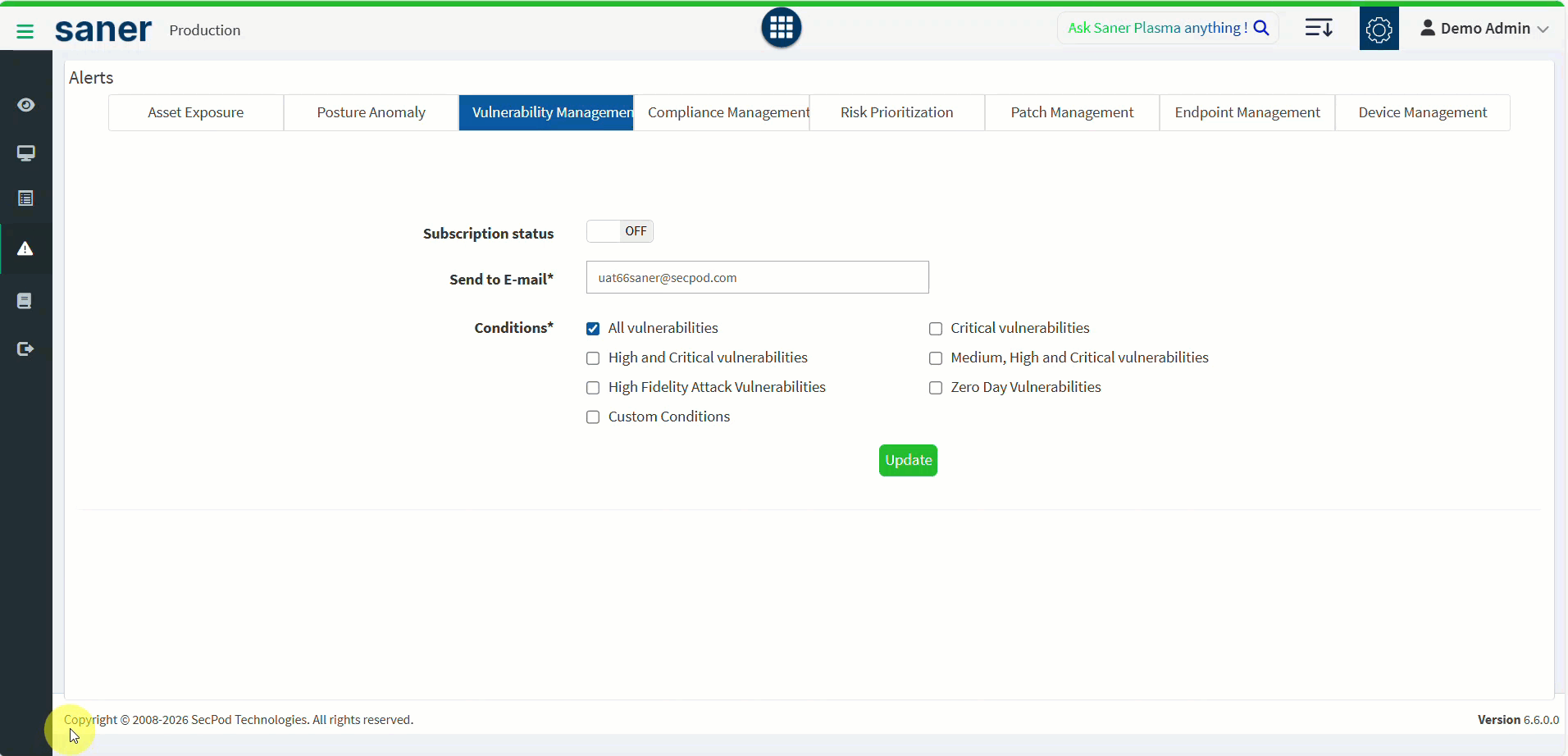
9. New Scan Policies and Expanded Detection Coverage
New scan policies extend coverage across modern and legacy environments.
- New scanning support for:
- Web Applications
- Virtualization platforms
- End-of-Life (EOL) applications and devices
- Databases
- SSL/TLS, SNMP, FTP, and SMTP misconfigurations
- Added detection for Backdoor and Malware instances.
Benefit: Broader visibility into security risks across diverse infrastructure.
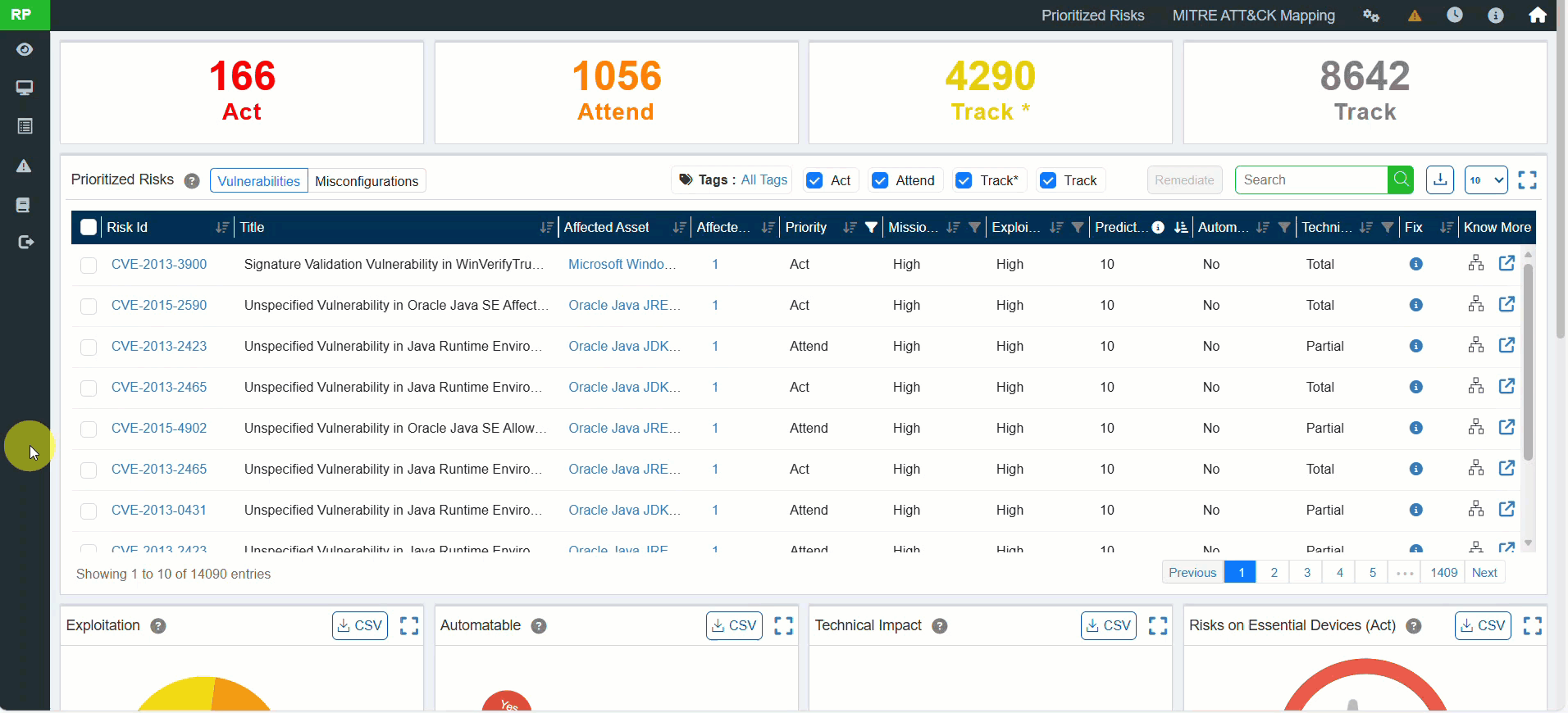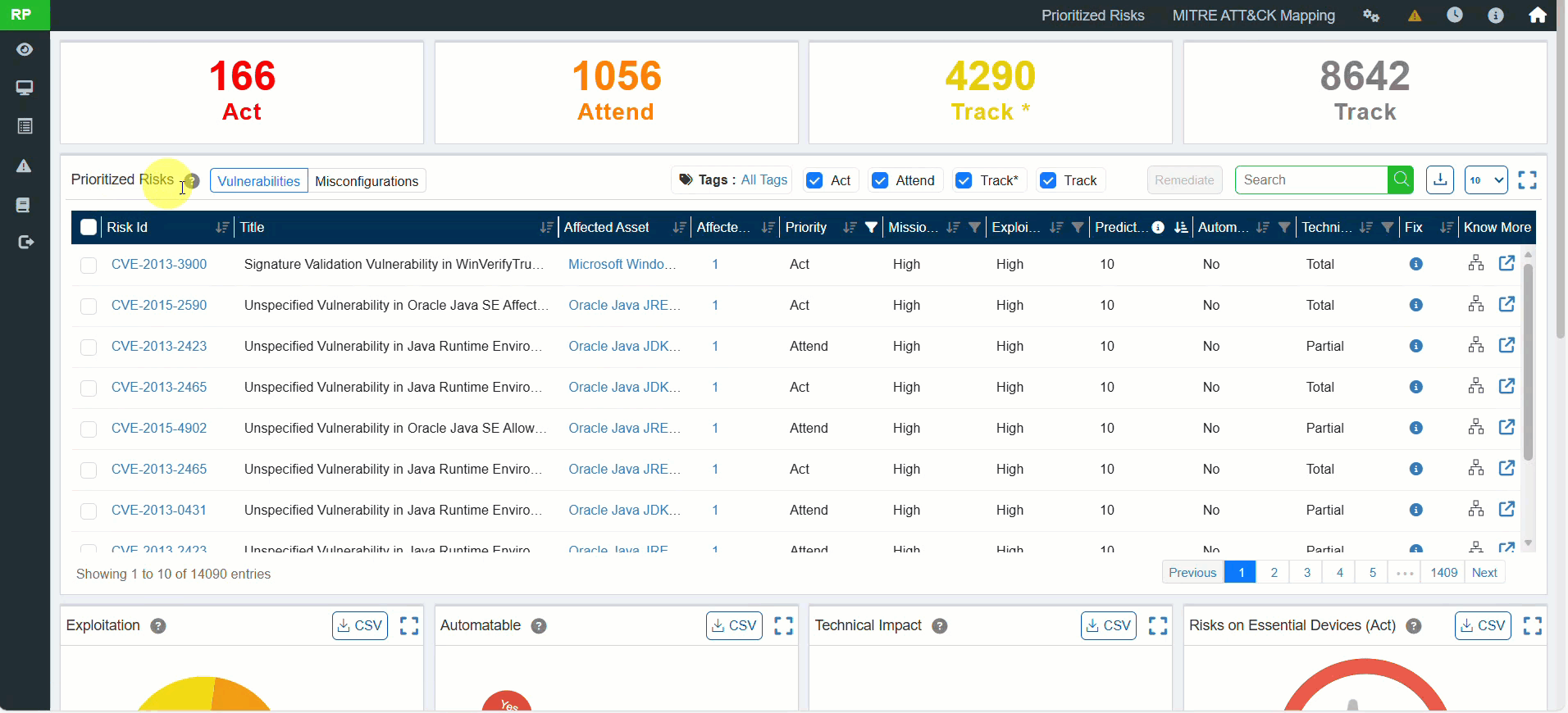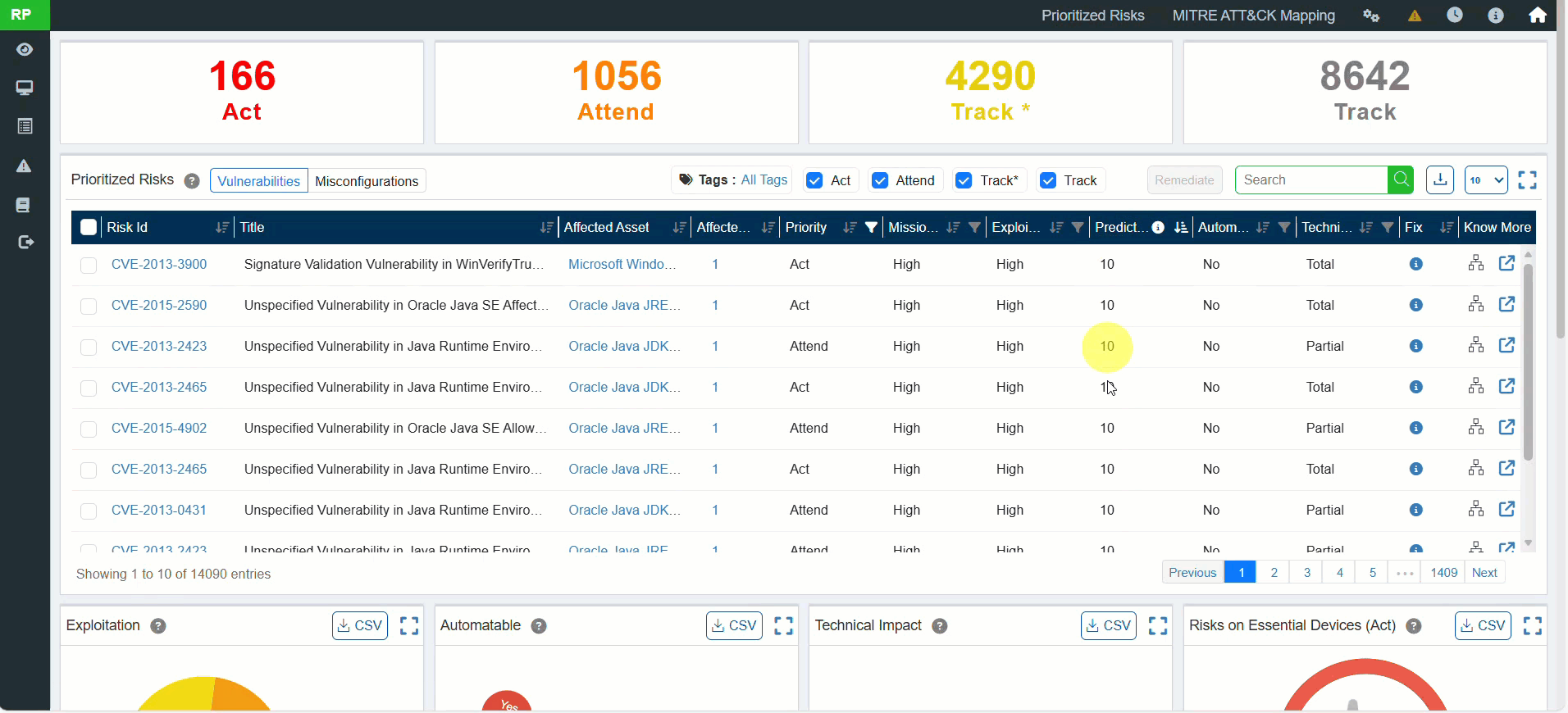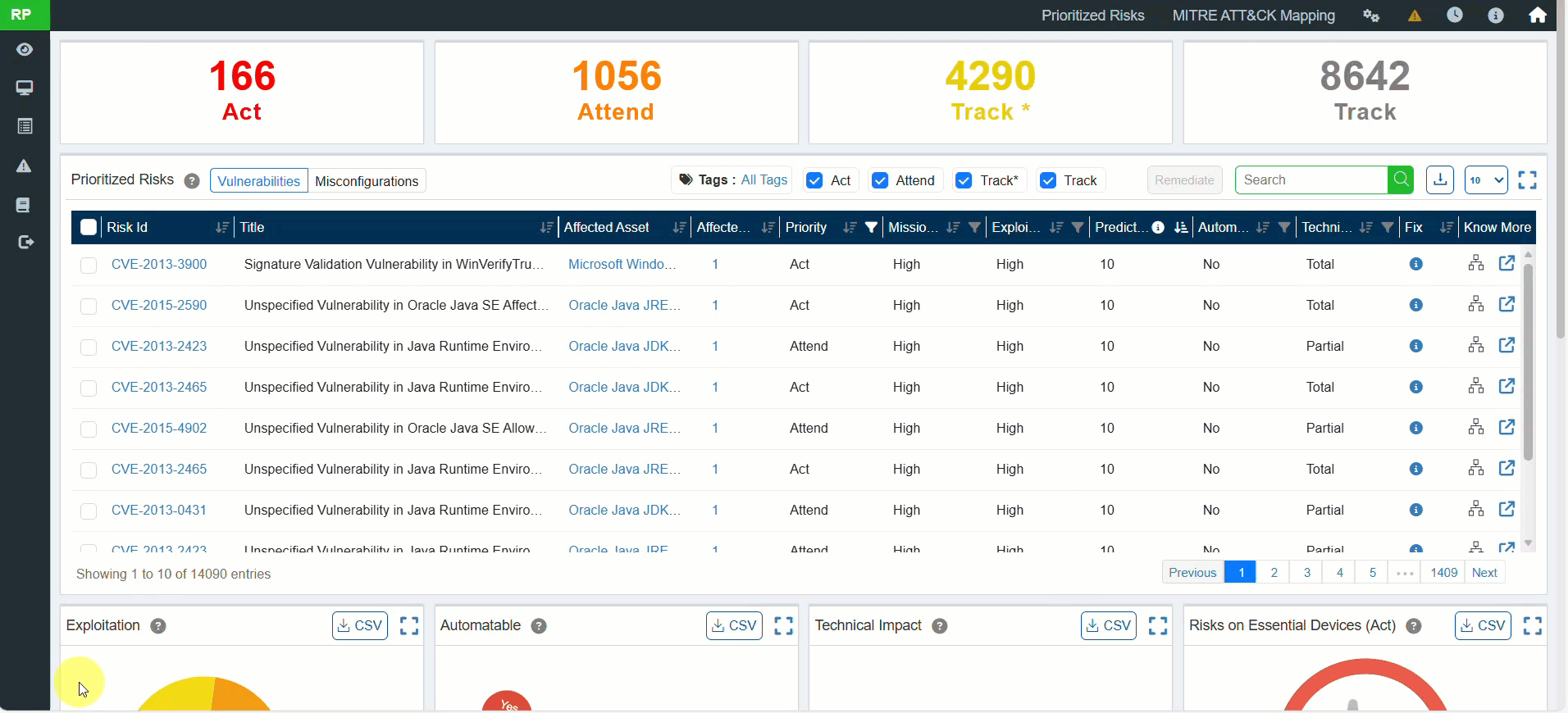
10. Saner Predicted Score (Advanced Risk Prioritization)
A new risk scoring system, Saner Predicted Score, is introduced.
- Modeled after EPSS (Exploit Prediction Scoring System).
- Provides better insight into real-world exploitability than traditional CVSS.
- Available for all identified vulnerabilities and misconfigurations.
Benefit: More accurate risk prioritization and smarter remediation decisions.
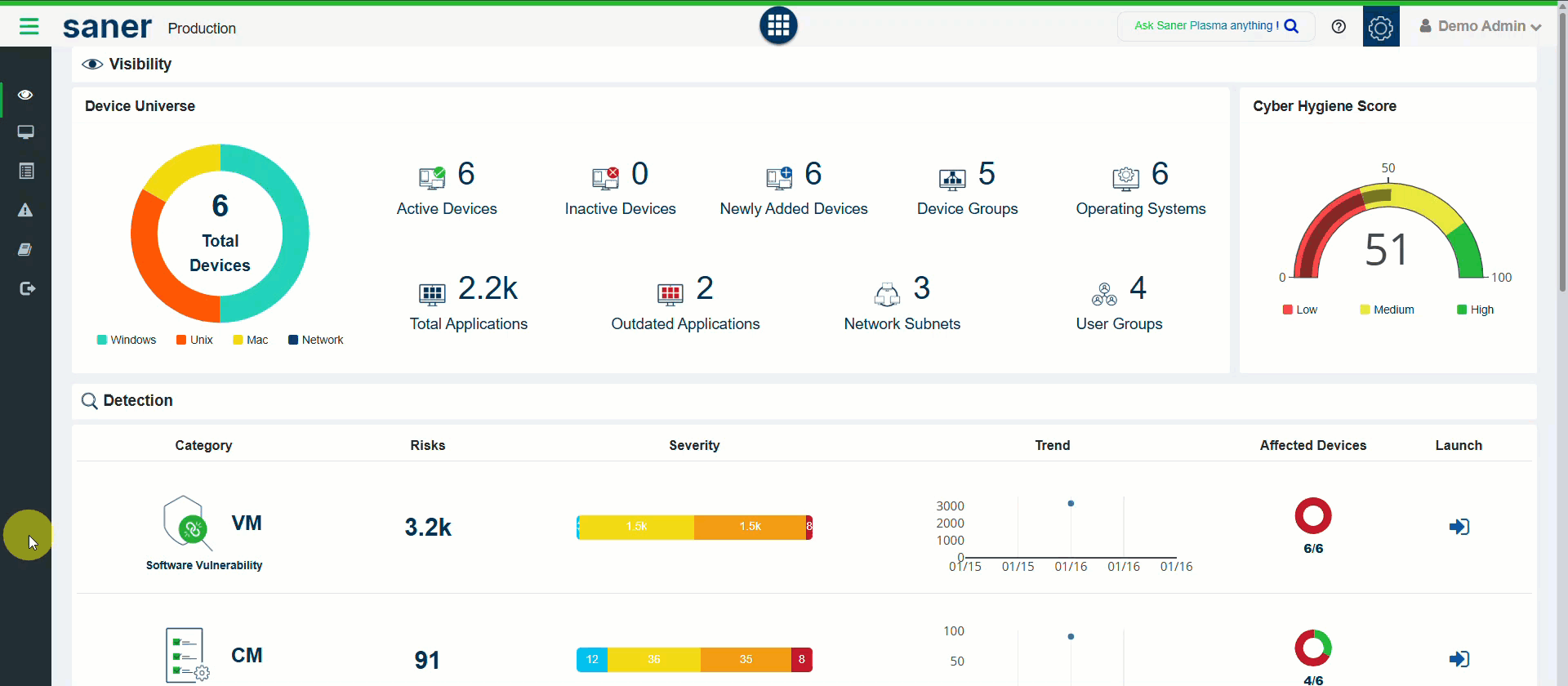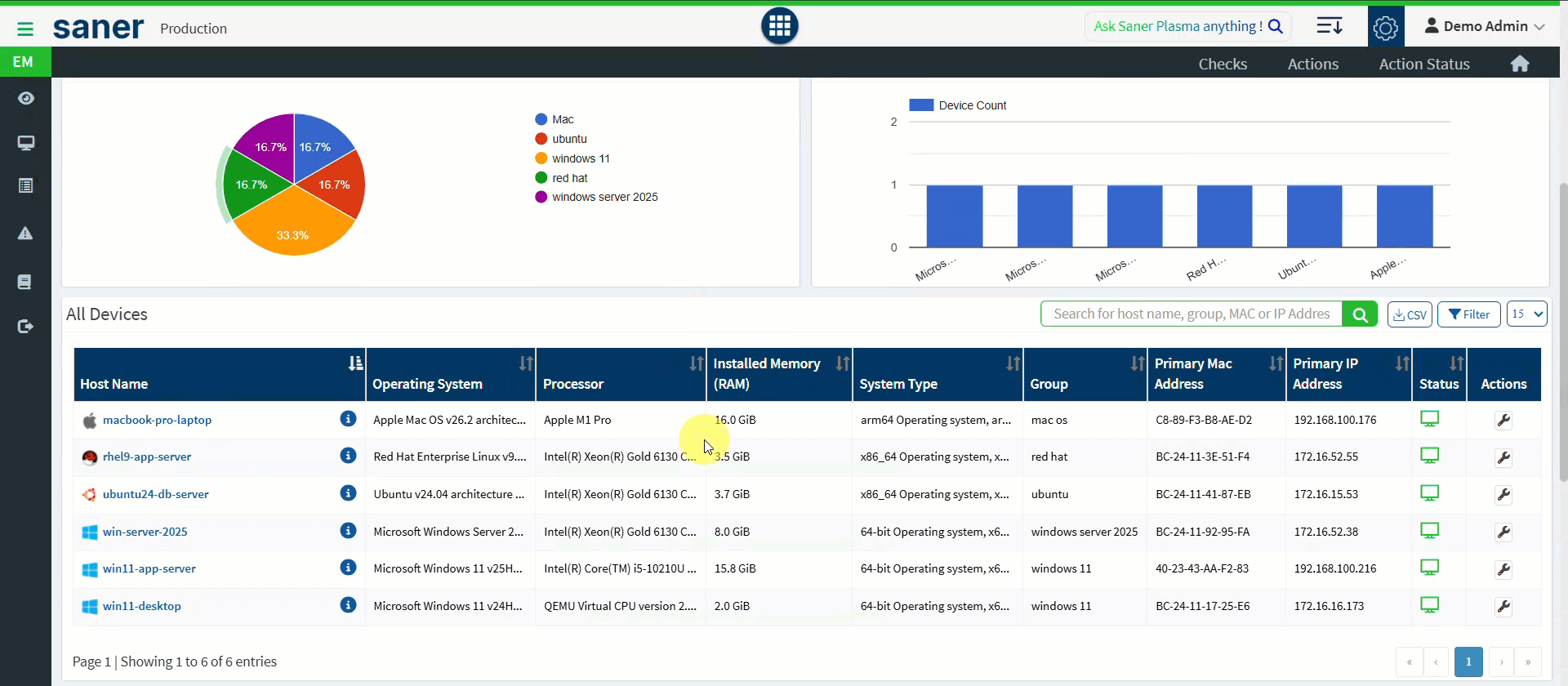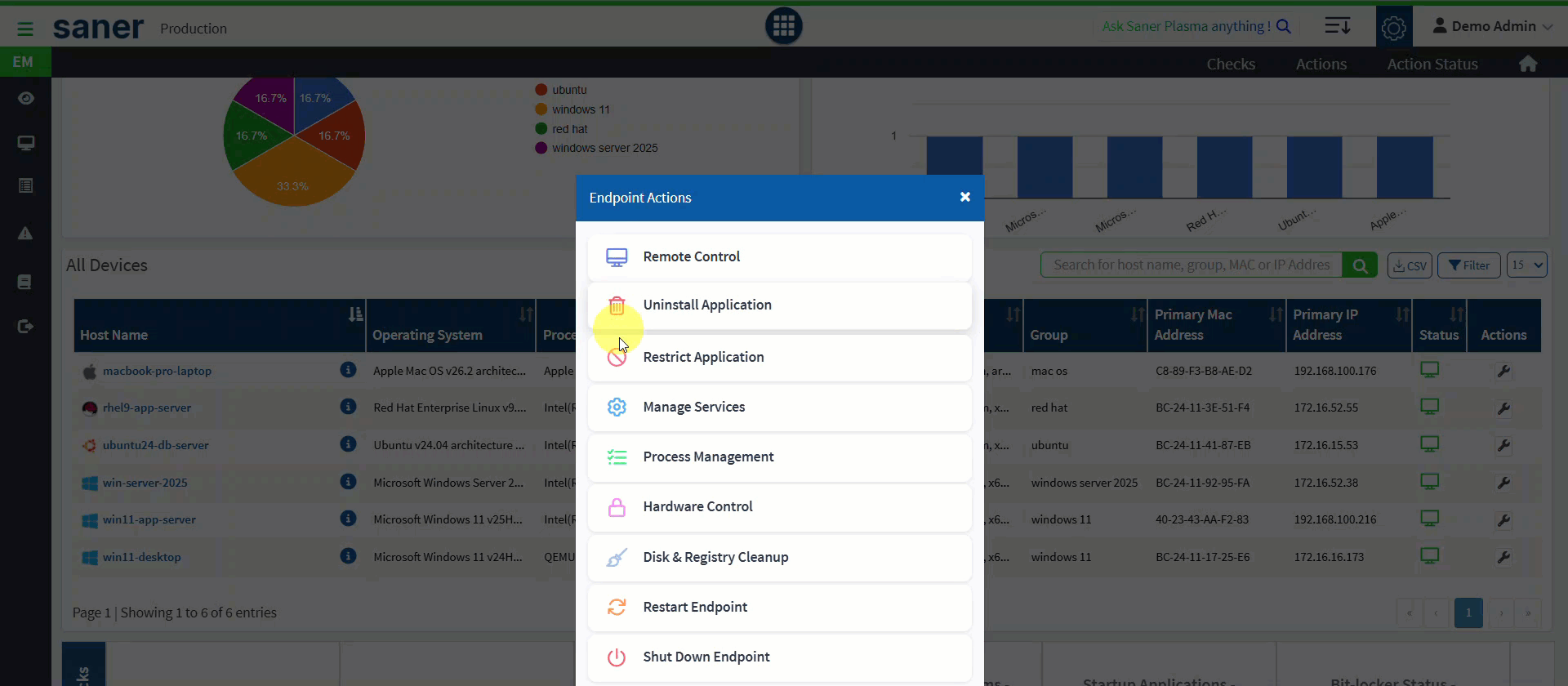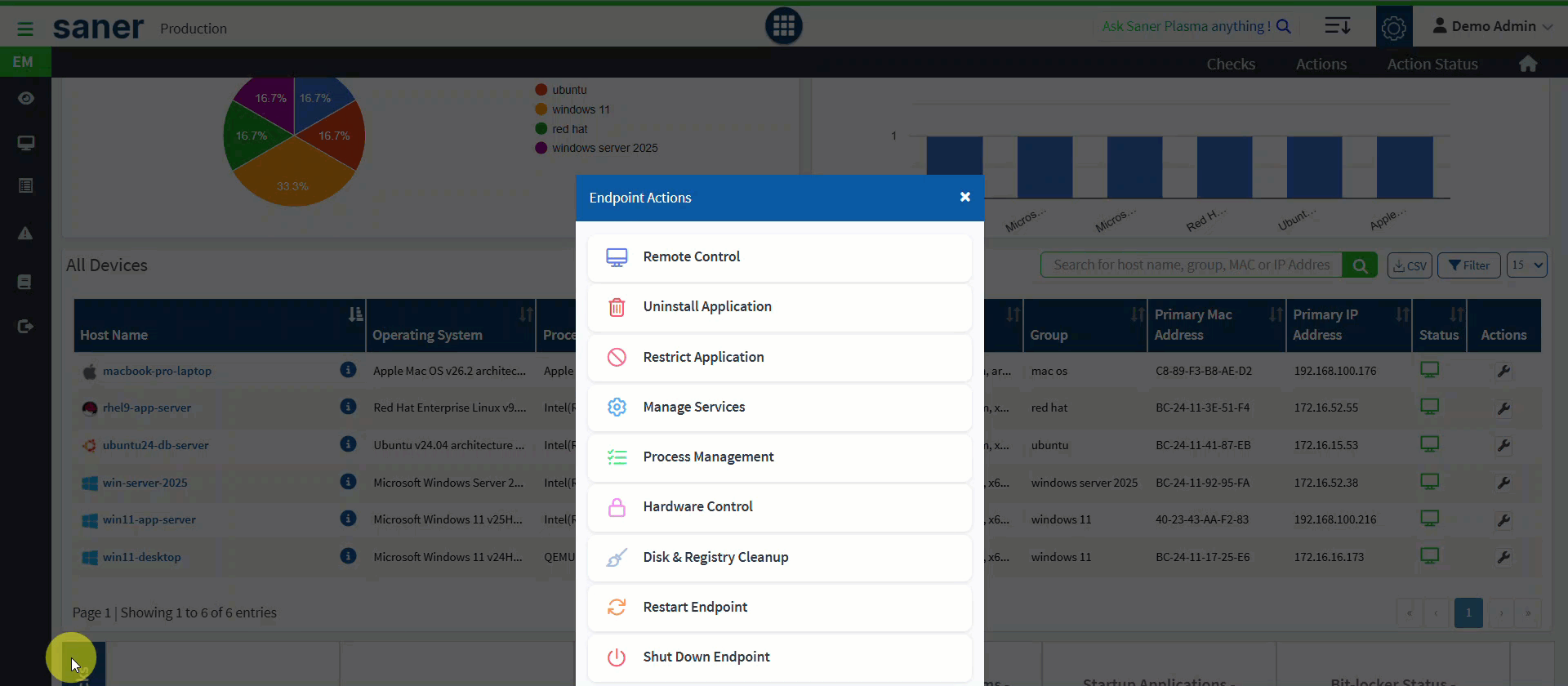
11. Endpoint Management: Device-Level Quick Actions
Administrators can now perform quick actions directly from the Endpoint Management dashboard.
- Reboot or shutdown devices
- Deploy or uninstall applications
- Execute actions at an individual device level
Benefit: Faster response and simplified day-to-day device management.
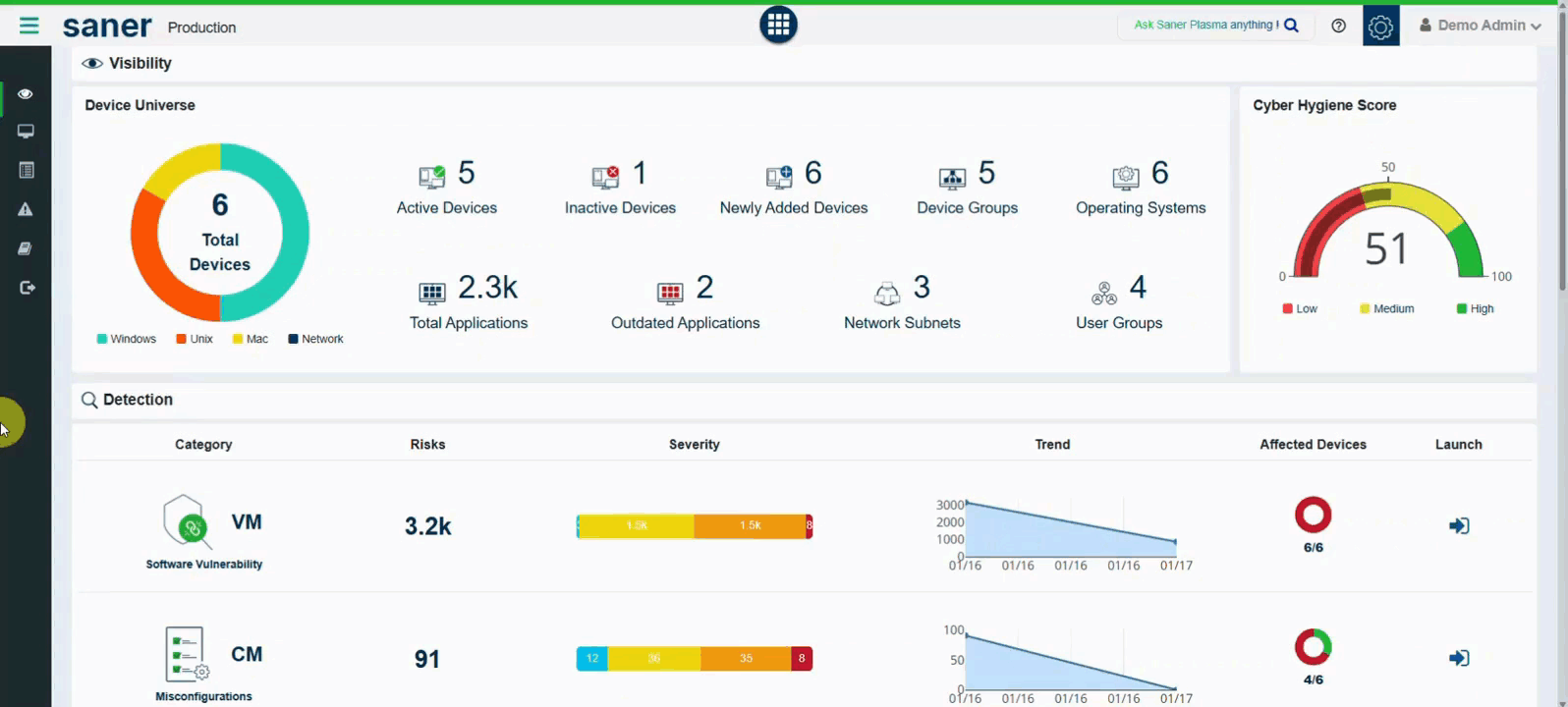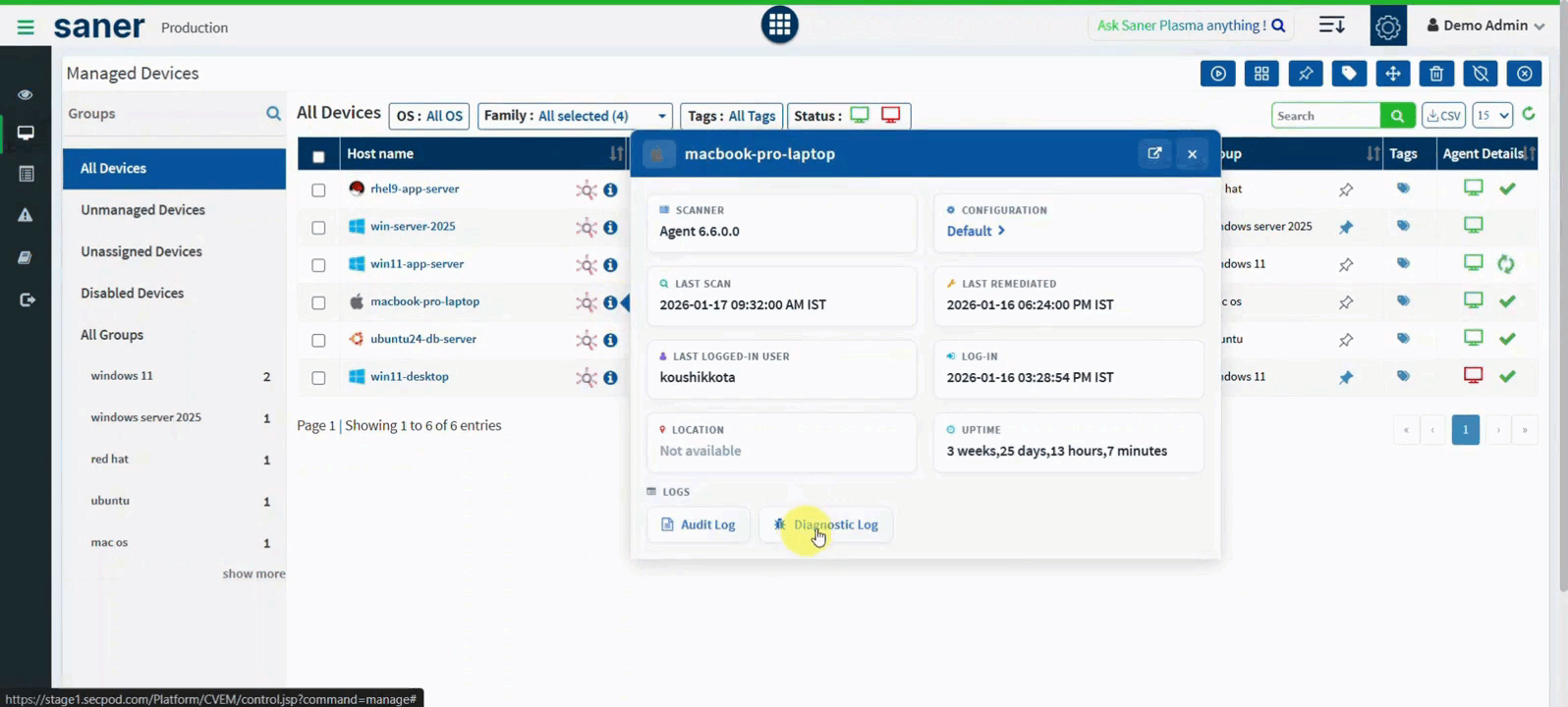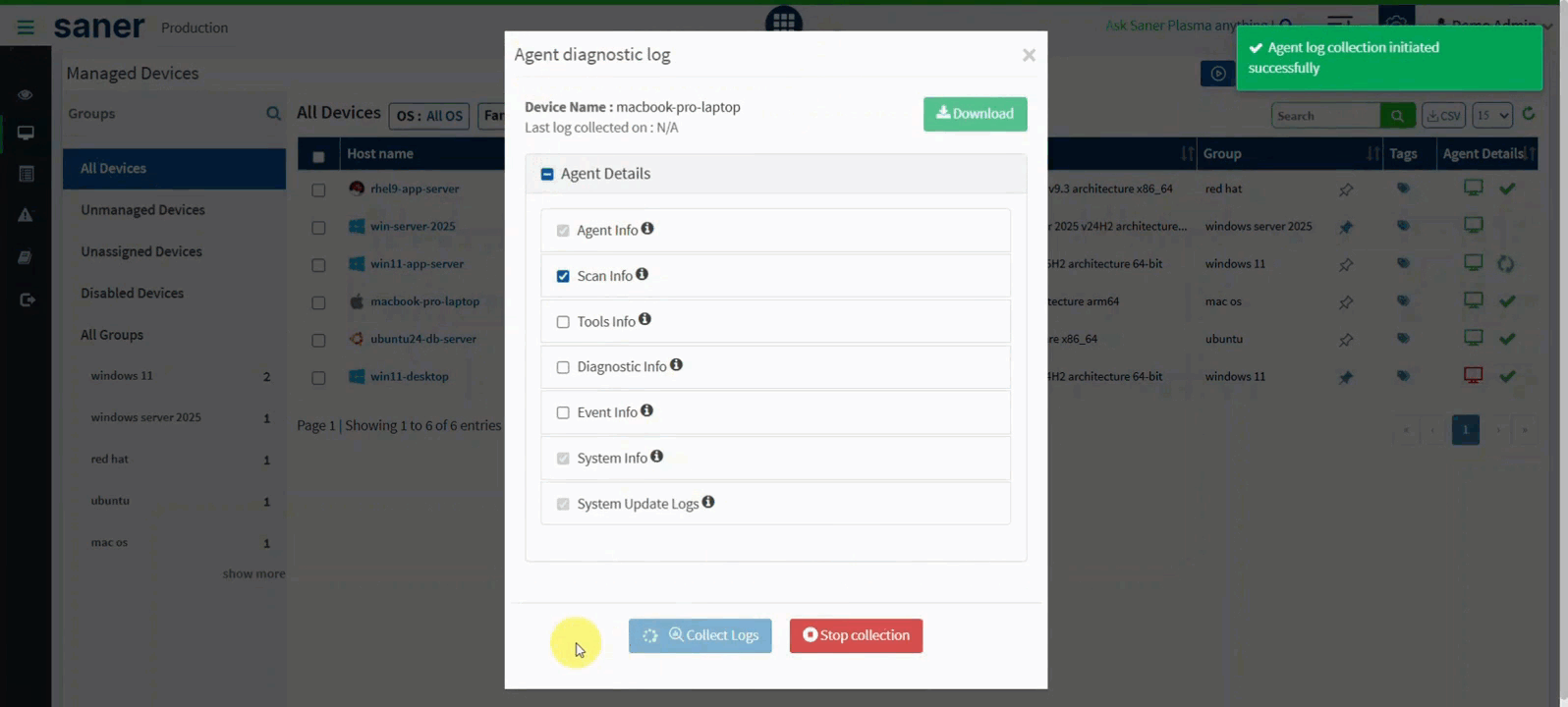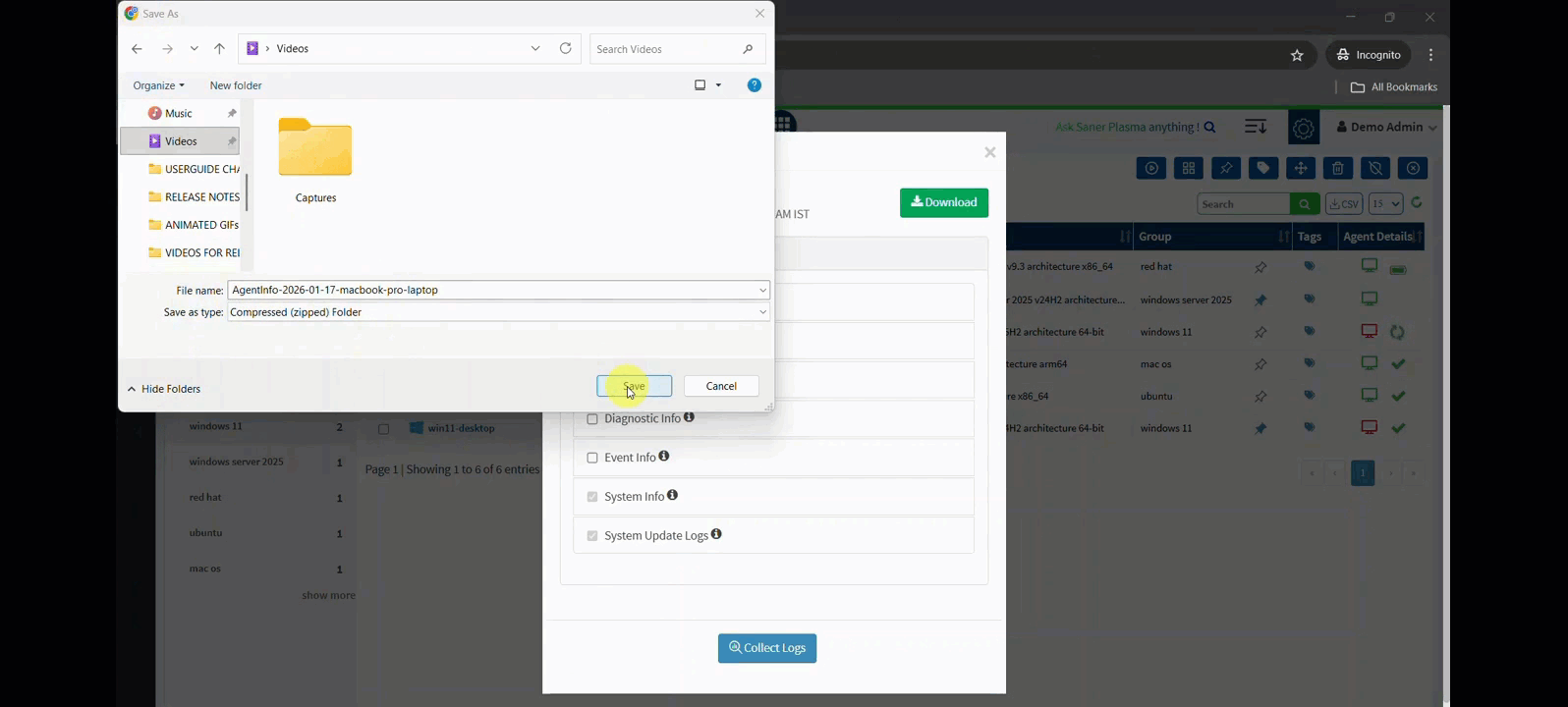
12. Enhanced Device Information
Device visibility has been significantly improved with enriched metadata.
Newly added details include:
- Last logged-in user
- Login time
- Last scan time
- System uptime
- Device location
Benefit: Better identity-to-device correlation for informed administrative decisions.
13. Zero-Day Vulnerability Visibility and Alerting
Zero-day vulnerabilities are now first-class citizens in Vulnerability Management.
- VM dashboard provides visibility into zero-day vulnerabilities.
- Enables faster awareness and initiation of remediation actions.
Benefit: Improved readiness and response to emerging threats.
14. Remote Diagnostic Log Collection for Saner Agents (Linux & macOS)
Remote diagnostic capabilities are expanded beyond Windows.
- Detailed diagnostic logs can now be collected from Linux and macOS systems.
- Previously available only for Windows agents.
Benefit: Faster troubleshooting and consistent support across platforms.
New Platform Support
Starting with Saner Agent version 6.6, support has been added for the following platforms:
- ARM 64bit support for all flavors of Linux
- ARM 64bit support for Mac systems
End of Support
Support for the following operating systems has been discontinued starting with Saner Agent version 6.6, as these operating systems have reached end of life (EOL).
- Linux RPM: RHEL 7.x, Oracle Linux 7.x, Amazon Linux 2.x, SUSE Linux Enterprise Server 12 SP5
- Linux Debian: Ubuntu 16.04, 18.04, Debian 8, 9
- macOS: 10.x, 11.x, 12.x
- Windows (32-bit)
- AIX: 7.1
Older Saner Agents (6.5.0.x and below) will continue to support the above operating systems.
REST and Report API Changes
This section outlines the REST and Report API enhancements included in this release.
Newly Added APIs
- Pin and Unpin Device:
ThepinandunpindeviceAPI allows administrators to pin a device to a specific group, ensuring it remains associated with that group irrespective of the configured group criteria (such as hostname, IP address, operating system, family, device type, or tags). When the device is unpinned, the grouping criteria are reapplied and the device is automatically reassigned based on the configured group rules.
- Move Device:
ThemovedeviceAPI allows administrators to move one or more devices to a different group, account, or organization. Devices can be moved within the same organization or across organizations and accounts. Optionally, devices can be pinned to the target group after the move, ensuring they remain associated with the selected group irrespective of the configured grouping criteria.
- Exclude Vulnerability:
TheexcludevulnerabilityAPI allows administrators to exclude vulnerabilities, patches, or assets from remediation and visibility based on the specified scope. Exclusions can be applied at the account, group, or device level when remediation or visibility is not required, risk is accepted, or remediation is temporarily deferred. Exclusions are enforced for the configured duration and are automatically removed once the exclusion period expires.
- Add Blacklisted Assets:
TheaddBlackListedAssetsAPI allows administrators to mark applications or assets as blacklisted. Blacklisted assets represent applications that are restricted, unauthorized, or pose a security risk within the environment. When a blacklisted asset is detected on any endpoint, it is flagged in the Asset Exposure (AE) dashboard, enabling administrators to identify violations and take appropriate remediation actions.
- Add Whitelisted Assets:
TheaddWhiteListedAssetsAPI allows administrators to mark one or more applications or assets as whitelisted. Whitelisted assets represent approved and trusted applications that are permitted within the environment. Applications added to the whitelist override any existing blacklisted status and are treated as trusted in the Asset Exposure (AE) dashboard.
Modified APIs
Pagination Support
Pagination support has been introduced to improve performance and scalability when retrieving large datasets. The following APIs now support pagination:
- getdevice (Device Management)
- getInstalledApplication (Asset Exposure)
- getReportApiData (Several Reports)
The following pagination parameters are supported:
- limit – Specifies the number of results per page
- currentPage – Indicates the current page number
- pageSize – Number of results returned in the current page
- totalEntries – Total number of results available
- isNextPage – Indicates whether a next page exists
- isPrevPage – Indicates whether a previous page exists
- totalPages – Total number of pages generated based on the specified limit
Report API Changes
New Canned Reports
We have added two new canned reports, ‘Vulnerability SLA Report’ and ‘Compliance SLA Report’, to provide detailed insights into the overall Service Level Agreement (SLA) compliance for vulnerabilities and misconfigurations across devices in an account. These reports help administrators track SLA adherence, identify violations, and monitor remediation progress for vulnerabilities and misconfigurations.
In addition, new custom reports have been introduced under the Vulnerability SLA Report and Compliance SLA Report categories to help monitor overall remediation SLA compliance across devices within an account.
New Custom Reports
Asset Exposure (AE)
- Applications by Devices
Provides a list of software assets installed on each device.
Patch Management (PM)
- Remediation Patch Details by Task Name (Rule)
Provides detailed patch information grouped by automation task (rule) name.
Vulnerability Management (VM)
- Backdoor Detection by Ports
Provides visibility into potential backdoor vulnerabilities identified based on open and listening ports. - Malware Detection by Ports
Provides insights into malware-related detections identified through port based scanning.
Report Enhancements and Modifications
New Columns Added
Asset Exposure (AE) Reports
A new column, ‘Install Date’, has been added to the following reports:
- Software License
- Outdated Applications
- Blacklisted Applications
- Rarely Used Applications
- Application Details
Asset Exposure (AE), Device Management (DM), Patch Management (PM)
New columns, ‘Logged In User’ and ‘Logged In Time’, have been added to the following reports:
- Device Details
- All Devices
- Patch Compliance by Devices
Vulnerability Management (VM)
- A new column, ‘MVE ID’, has been added to the ‘High Fidelity Attacks’ report.
- New columns, ‘Exploitability’, ‘Zero Day’, ‘Asset Family’, and ‘Patch Type’, have been added to the ‘All Vulnerabilities’ report.
The following new columns have been added to the ‘Vulnerabilities by Devices’ report:
- OS Name, Asset Type, Asset Outdated, Zero Day, Vulnerability Aging (in Days), Exploitable, Logged-In User, Logged-In Time
Risk Prioritization
A new column, ‘Predicted Score’ (New risk scoring system), has been added to the following reports:
- Risks Based on Priority (Vulnerability)
- Risks Based on Priority (Misconfiguration)
- Top 10 Prioritized Vulnerabilities
- Top 10 Prioritized Misconfigurations
Patch Management (PM)
- New columns, ‘Hosts’ and ‘MVE ID’, have been added to the ‘Most Critical Patches’ report.
- A new column, ‘InstalledBy’, has been added to the ‘Installed Patches’, ‘Patch Compliance’ and ‘Installed Patches by Devices’ report.
- A new column, ‘Release Date’, has been added to the ‘Non-Security Patches Details’ report.
Compliance Management (CM)
New columns, ‘Risk Count’ and ‘Risks’, have been added to the ‘Top 10 Recommended CCE Remediation’ report.
Endpoint Management (EM)
A new column, ‘Last Update’, has been added to the ‘Software Deployment Jobs’ report.
New SLA Date Range Filter
A new SLA Date Range filter has been introduced for the following reports to enable refined SLA-based analysis:
- Devices with Violations (VM, PM and CM)
- SLA Violating Patches (VM, PM and CM)
- Devices Approaching SLA Deadline (VM, PM and CM)
- Vulnerabilities Requiring Attention (VM)
- Patches Requiring Attention (PM)
- Compliance Requiring Attention (CM)
- SLA-Compliant Devices (VM, PM and CM)
- SLA-Compliant Vulnerabilities (VM)
- SLA-Compliant Patches (PM)
- SLA-Compliant Misconfiguration (CM)
This filter allows administrators to analyze SLA compliance within a specific timeframe, supporting better tracking, reporting, and remediation planning.
We would love to hear from you! If you have any feature suggestions to help improve your experience with Saner CVEM, feel free to contact us at [email protected].


