Saner Cloud is a comprehensive solution designed to help organizations effectively manage their cloud operations. Its key modules include asset exposure, posture management, posture anomaly detection, identity and entitlement management, and remediation management.
With meaningful dashboards that provide insights into each security domain, Saner Cloud aggregates critical information from all products, offering a unified view of the security posture across cloud assets.
Major Features and Functionalities:
1. Unified Dashboard
The Saner Cloud Unified Dashboard provides a single platform that consolidates data and insights from multiple sources into one cohesive view. It offers users a comprehensive overview of important data points following the completion of each scan.
This unified dashboard enhances the user experience by eliminating the need to switch between tools to access various data sources. Instead, all information is displayed in one location(at the organization level), enabling better decision-making, quicker responses, and increased efficiency. Users also have the option to click on relevant sections of the dashboard for additional details.
Key features of the unified dashboard include:
- Centralized Data: It aggregates data from various tools into a single interface
- Real-time Updates: After each scan, real-time information is displayed, providing users with up-to-date insights.
- Visualization Tools: Charts, graphs, tables, and other visual elements make the data easier to understand and interpret.
2. Cloud Security Asset Exposure (CSAE): Identifies and analyzes cloud assets to determine exposure risks
Creating Custom Watchlists for Critical Resources
You can define Watchlists to monitor critical cloud assets. Adding resources to the Watchlist enables proactive monitoring and ensures that any changes or risks associated with these critical resources are addressed promptly.
Identifying and Securing Publicly Accessible Resources
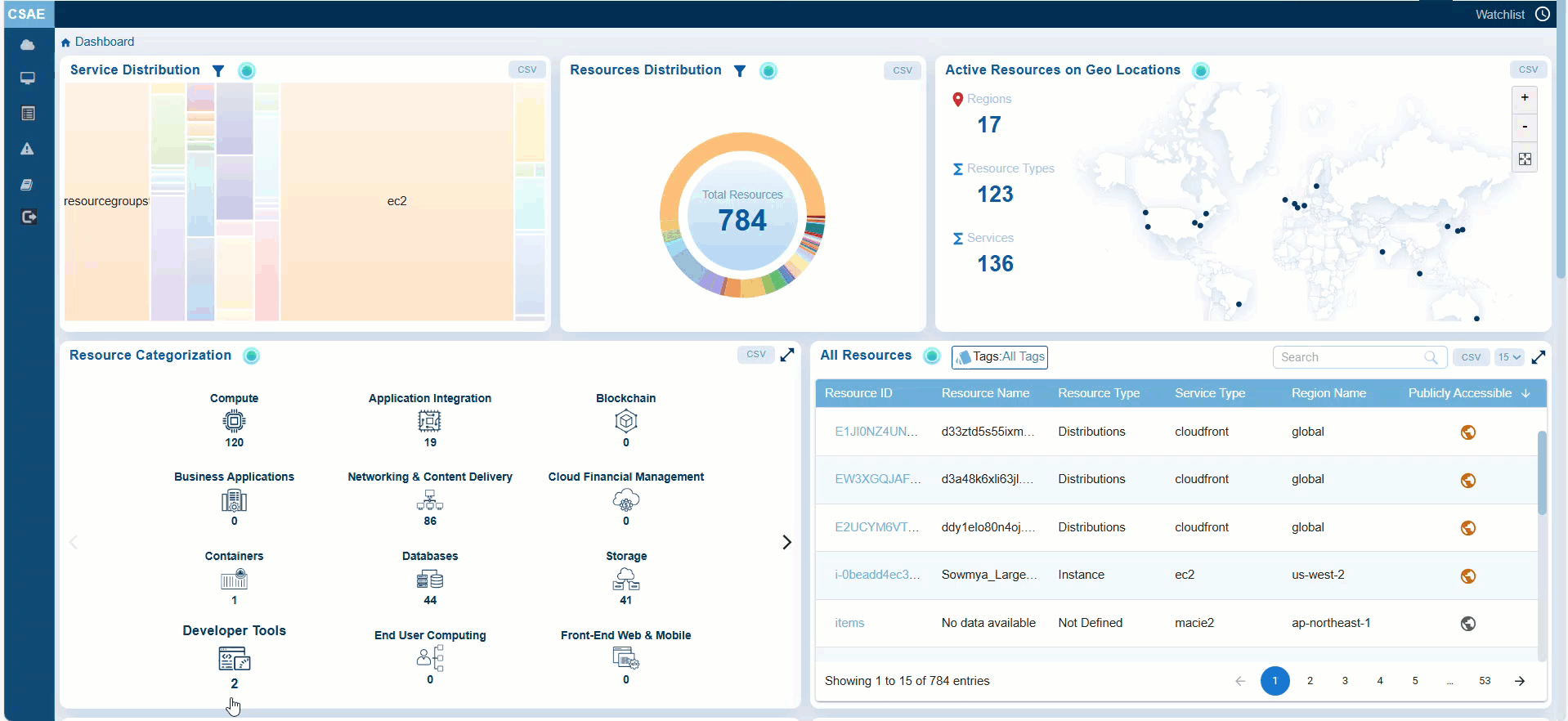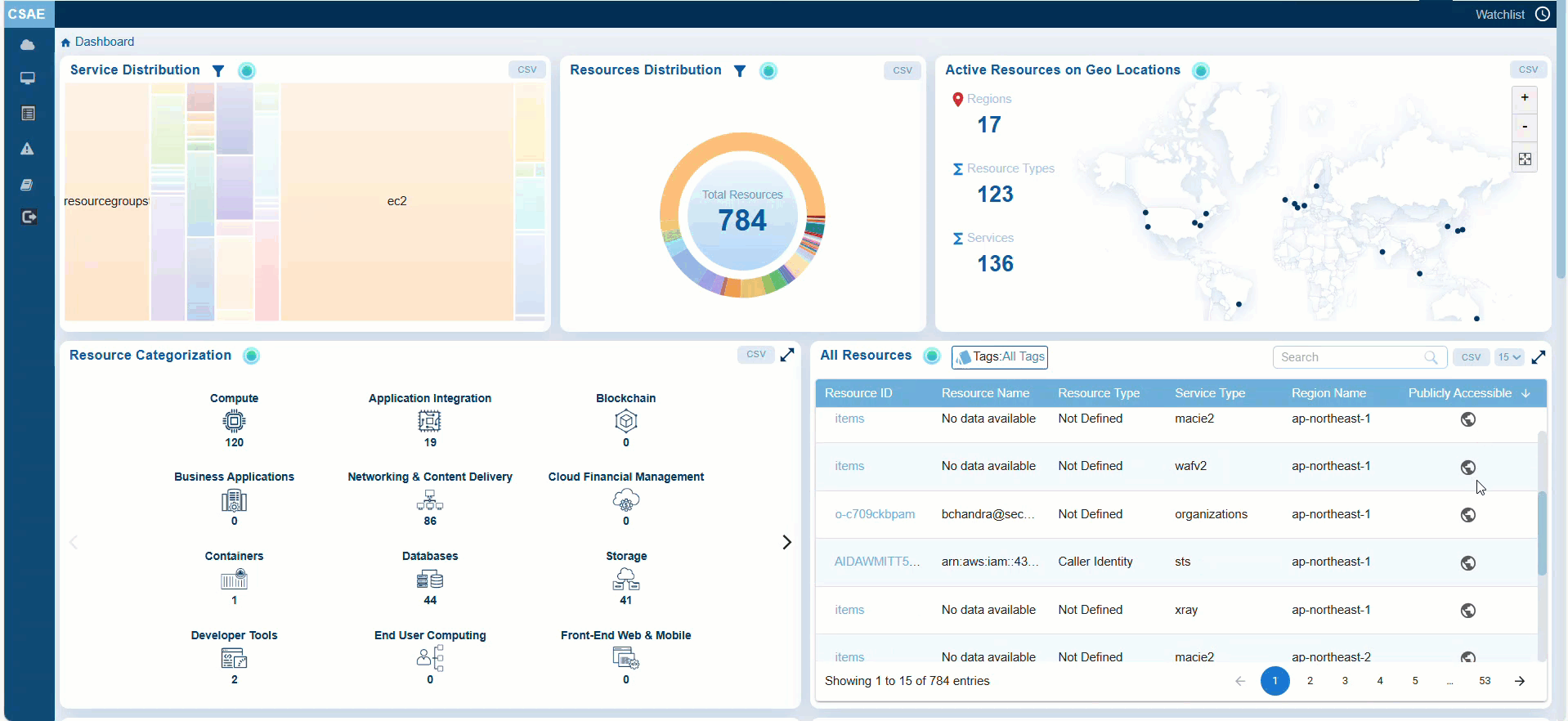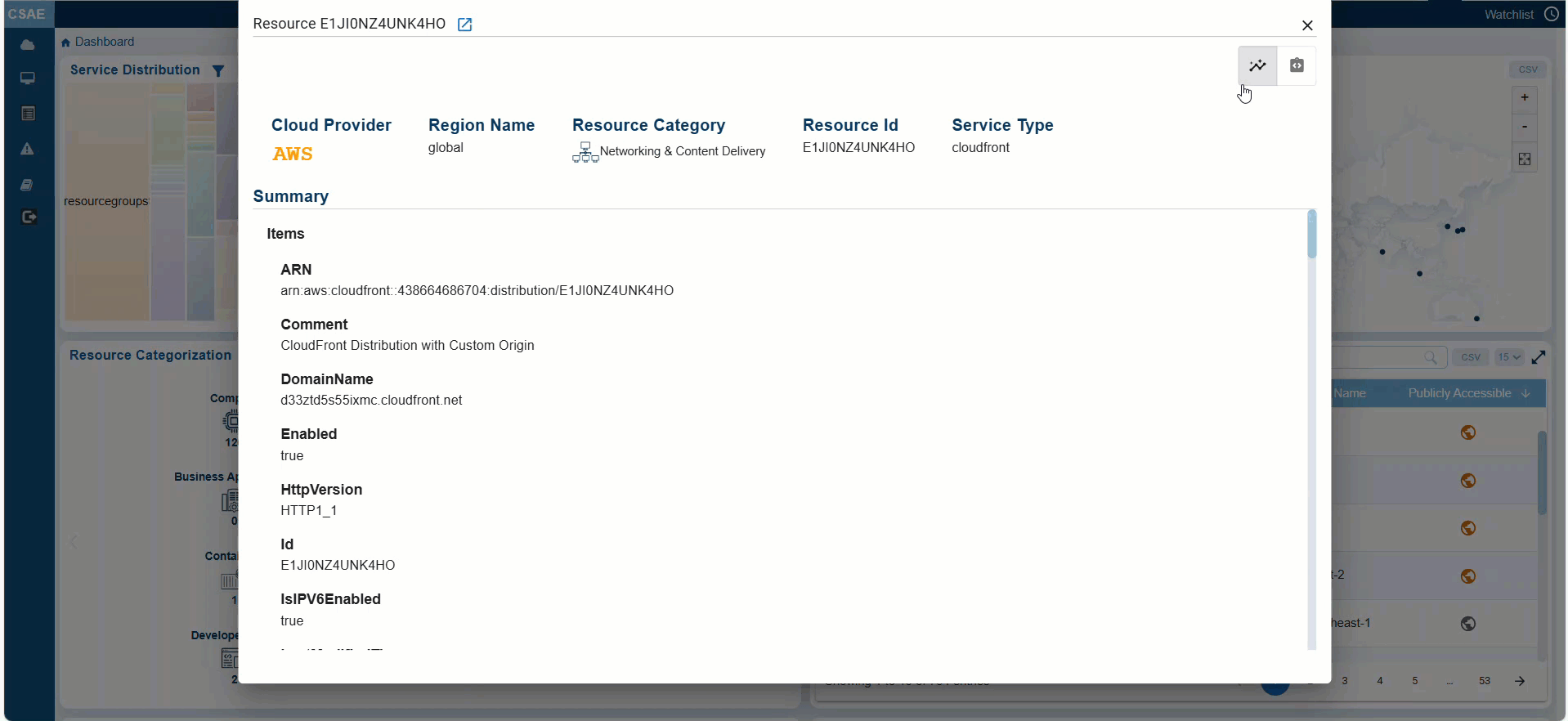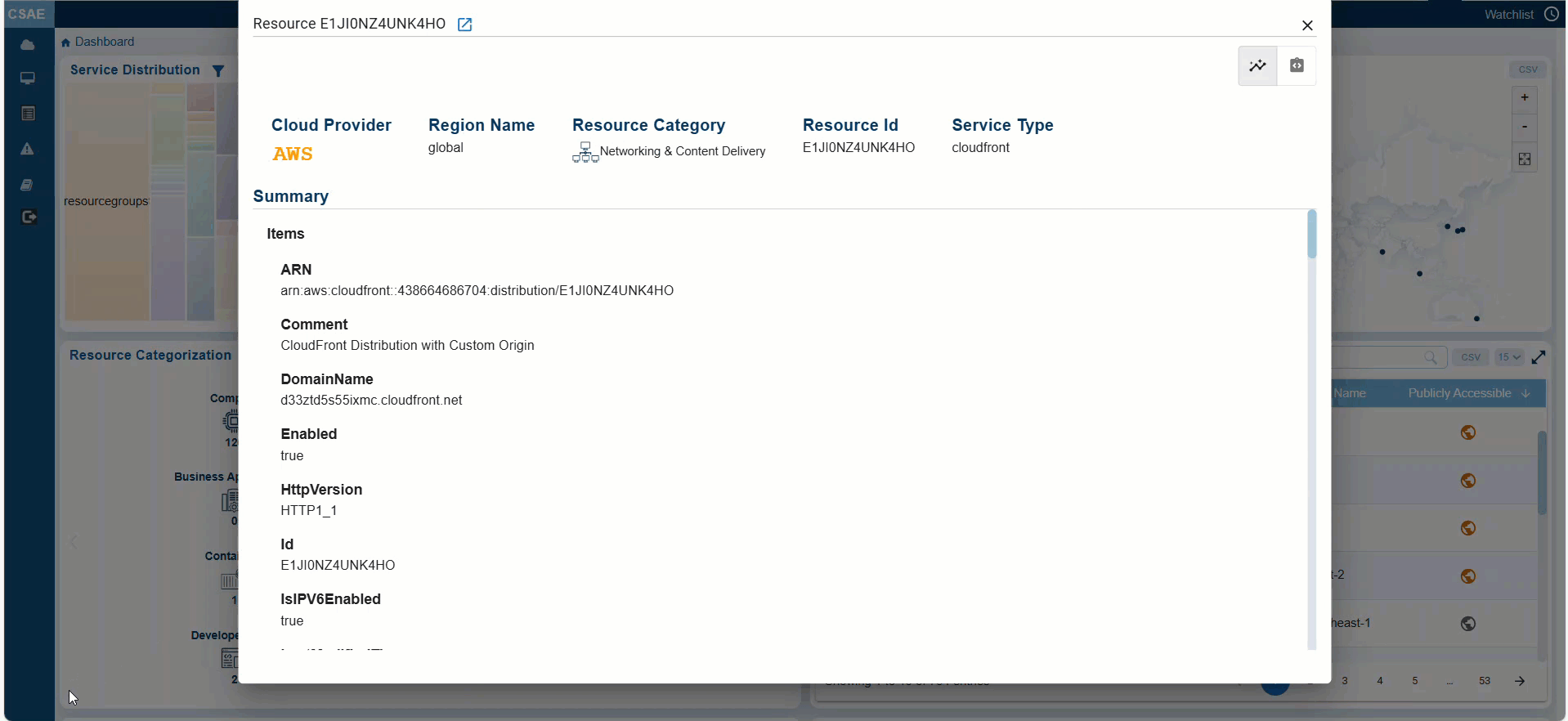
You can quickly identify which resources actively utilize the public network interfaces, and which ones do not, aiding in security and resource management decisions. These resources can include databases, storage buckets, or compute instances.
Understanding the Resource Print Globally Across Various Regions
Gain an overview of resource distribution across AWS or Azure to monitor cloud assets and services in various geographic regions. This facilitates the identification of resource concentration and allows assessment of their security posture based on location.
Switching between Standard and JSON views for Detailed Information on Resource
CSAE provides a detailed view of each resource, including configurations, permissions, usage, and security posture. Additionally, you have an option to toggle between the Standard and JSON views by clicking the appropriate buttons within the individual resource details view.
Detecting Deprecated and Outdated Services
CSAE automatically flags deprecated services that may pose security or functionality risks, allowing teams to migrate to newer alternatives before support is discontinued.
By executing automated scans and displaying outdated resources on a user-friendly dashboard, users can:
a) Identify deprecated or unsupported resources
b) Review and prioritize resources that are no longer in use or are vulnerable
c) Remove unnecessary resources
Making Informed Decisions on Your Expenditure based on Resource Usage
Gain insights into cloud expenditure from the dedicated cost and usage dashboard view, which breaks down costs at both the service and resource levels. This allows organizations to identify high-cost areas and make informed budgeting decisions.
3. Cloud Security Posture Management (CSPM): Ensures compliance by continuously monitoring cloud configurations and security policies
Creating Tailored Benchmarks
The SecPod Default Benchmark provides a pre-configured, regulatory-compliant assessment framework aimed at streamlining risk identification and mitigation across cloud environments. The benchmark system scans resources and services against selected compliance standards on a scheduled or on-demand basis.
Identifying and Resolving Configuration Issues with Quick Evaluation Benchmarks
Saner CSPM offers fast and efficient evaluations of benchmarks, allowing organizations to quickly identify and resolve configuration issues during routine audits. This feature helps save time and ensures continuous compliance with security standards.
Detecting Patterns over a Period with Resource-Trends
The Date-Wise Affected Resources Line Trend graph tracks the status of affected resources over time, helping you monitor their progress and avoid sudden spikes in non-compliance in the future.
Assessing System Compliance and Security Posture
Saner CSPM offers a comprehensive overview of primary benchmarks, showing their severity distribution and compliance status. You can track whether resources have passed, failed, or remain unchecked due to disabled checks or unavailable data, providing a clear understanding of your compliance posture.
4. Cloud Security Posture Anomalies (CSPA): Detects deviations and anomalies in cloud security posture
Prioritizing Remediation or Fixes based on Confidence Level
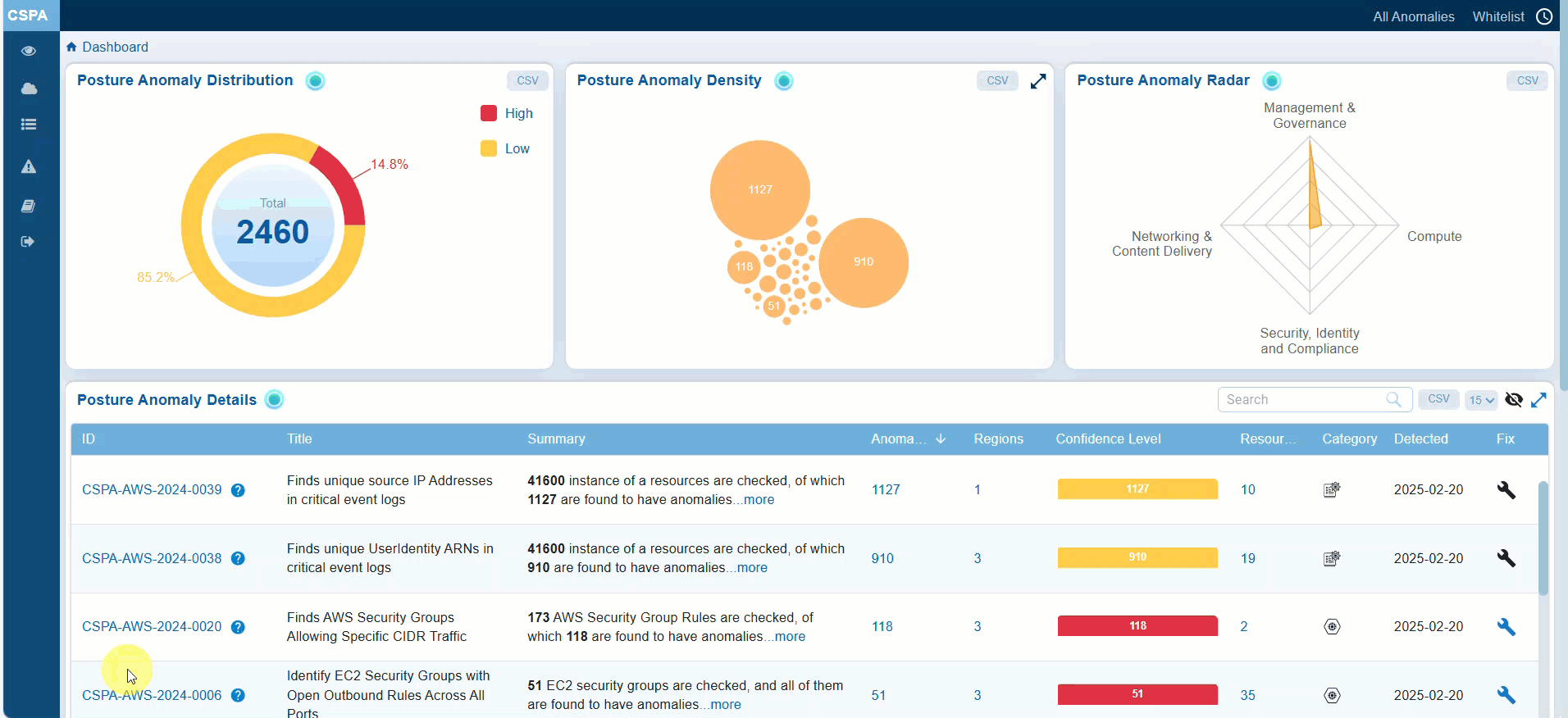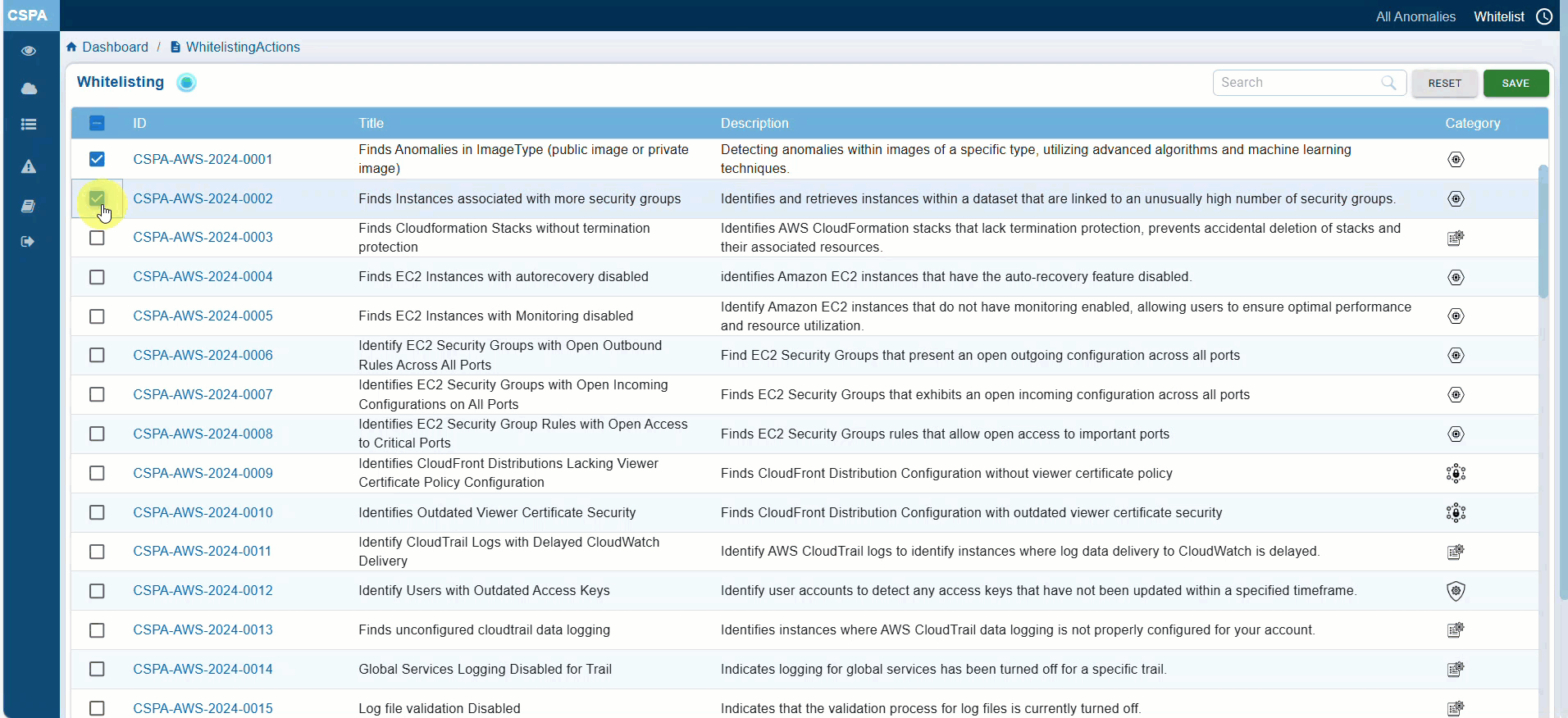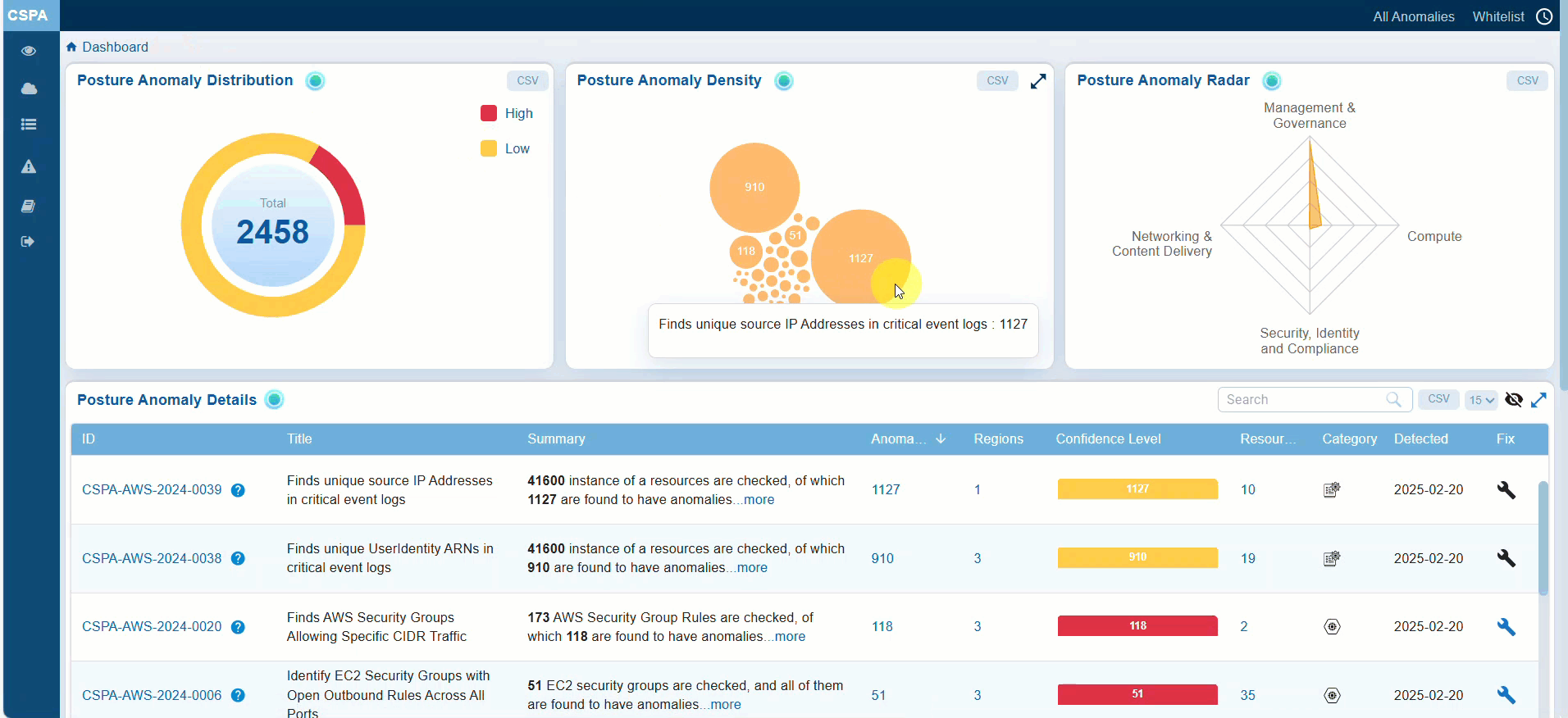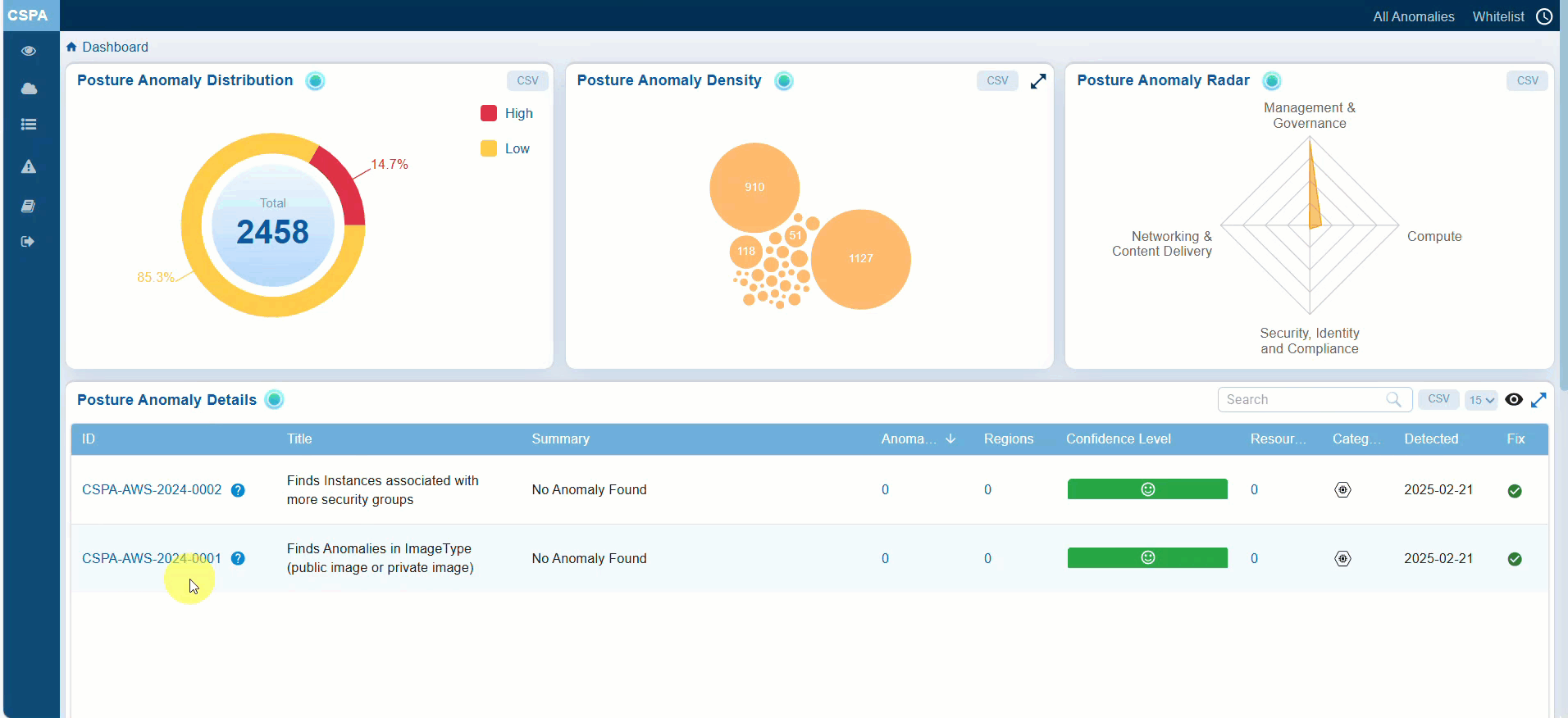
Confidence Level indicates if the system is certain in determining if a detected issue or misconfiguration poses a risk. Anomalies in Saner CSPA are categorized based on a machine learning algorithm threshold or through pre-assigned severity levels. This breakdown helps prioritize actions, ensuring that critical issues are addressed first while allocating appropriate resources to less critical ones.
You have an option to look into the Confidence Level to make informed decisions from the:
— Posture Anomaly Details view within the CSPA dashboard
— Posture Anomaly Distribution(High, Medium, and Low) on the CSPA dashboard
Identifying the Detected and Remediated Anomalies for an Account
The “All Anomalies” in Saner CSPA offers a visual representation of all the anomalies detected in the Saner Cloud account as well as the anomalies that are normalized(remediated).
Anomaly data is indicated in 2 different sections indicated by distinct color codes:
— Red: highlights critical issues that require immediate attention
— Green: provides assurance about resource categories that are not problematic and remediated
Whitelisting Rules or Resources
When certain anomalies for rules or resources no longer applicable, Saner CSPA provides you with the facility to whitelist or exclude these from the cloud security scans. Whitelisted anomalies are excluded from patching recommendations, allowing organizations to focus only on actionable security gaps.
Remediating Anomalies with a Single Click
Using the Remediation functionality within Saner CSRM, you can choose to remediate anomalies based on individual resources or apply fixes to all identified security gaps collectively. This reduces the manual effort required to secure cloud resources.
Prioritizing and Addressing Older or High-Risk Anomalies with Patch Aging
The “Patch Aging” dashboard view in Saner CSRM displays a time-based line plot that shows the correlation between the number of pending patches and their age in days, helping teams address older, high-risk vulnerabilities first.
Getting a Clear Understanding on the Patch Remediation Effort
The “Patching Impact” dashboard view in Saner CSRM plots the number of security rules fixed against the number of patches applied, offering a clear understanding of the effectiveness of remediation efforts.
5. Cloud Security Entitlements Management (CIEM): Manages identity and access entitlements to prevent unauthorized access
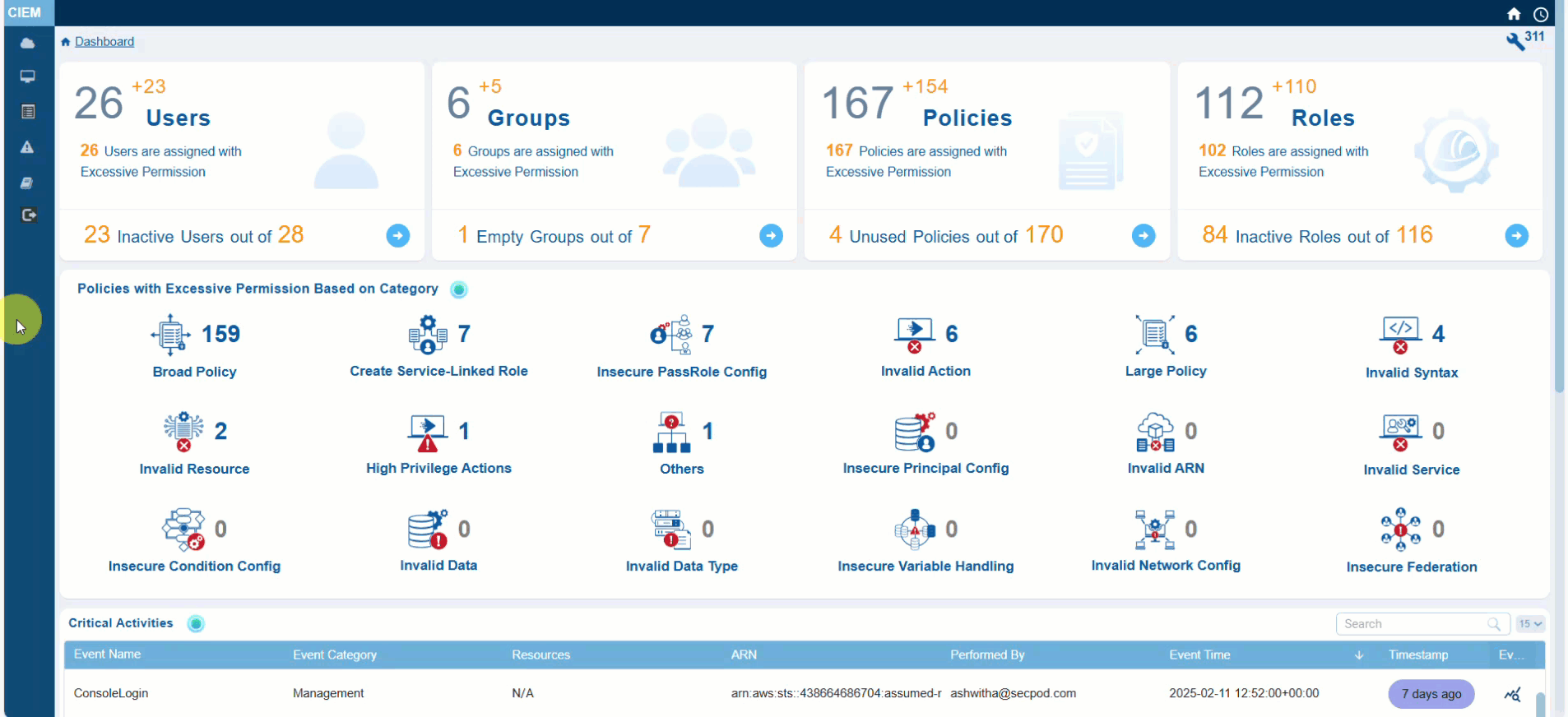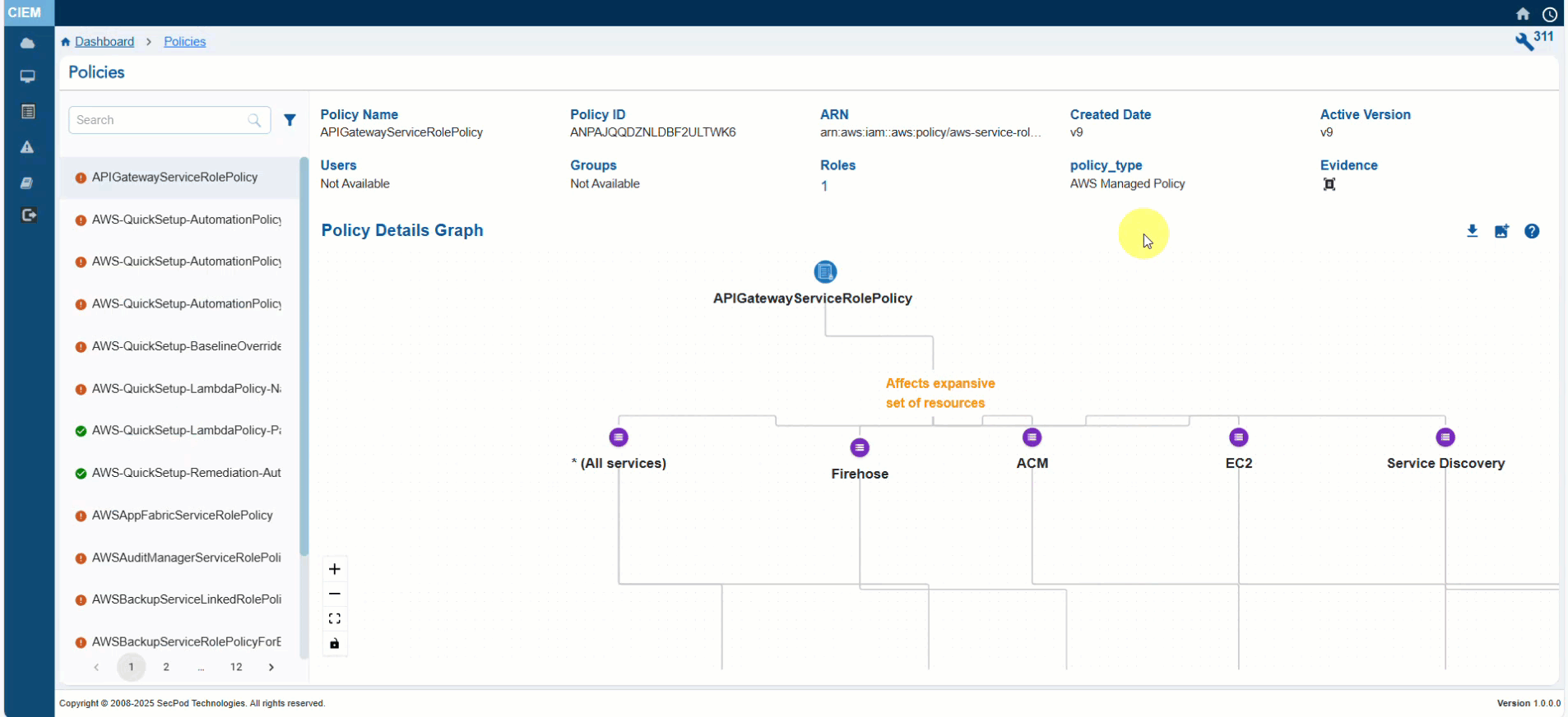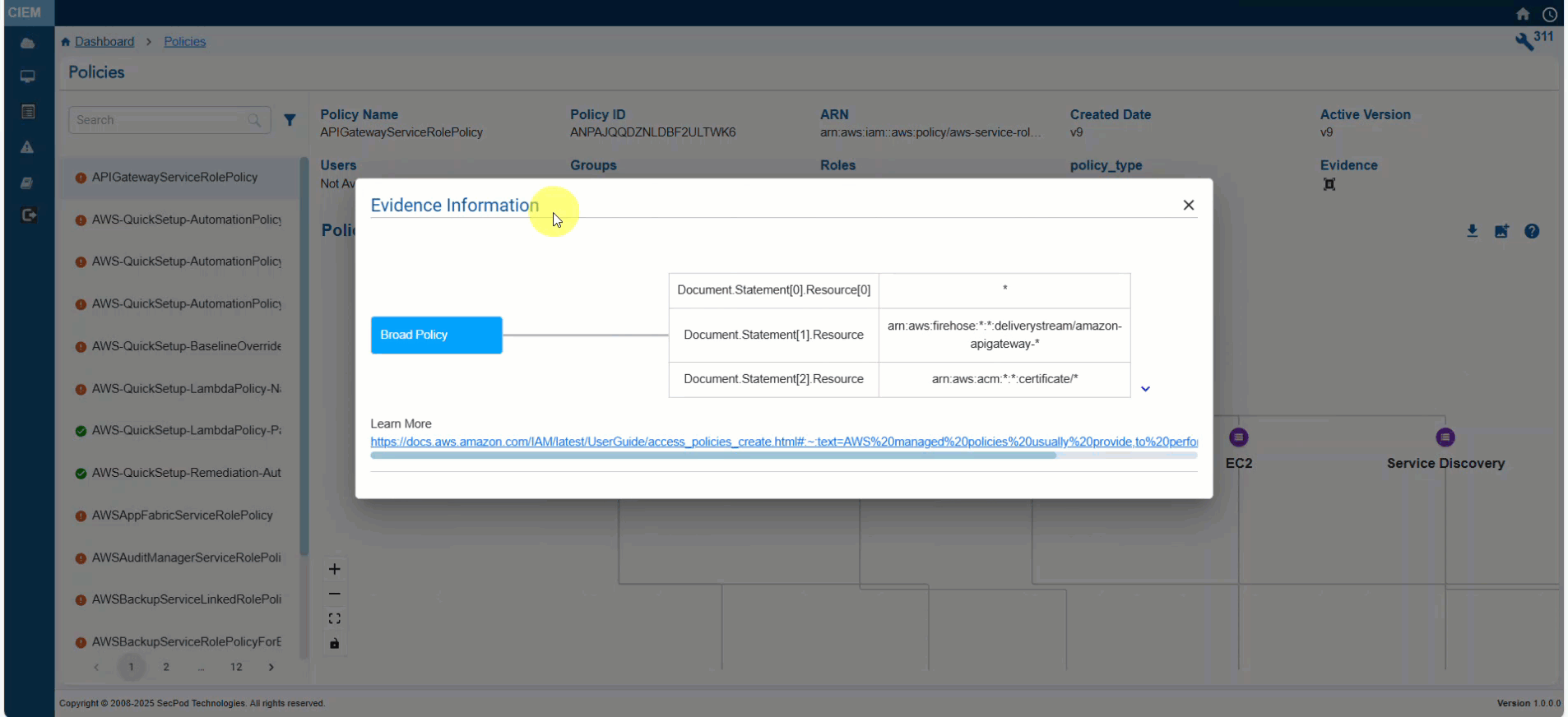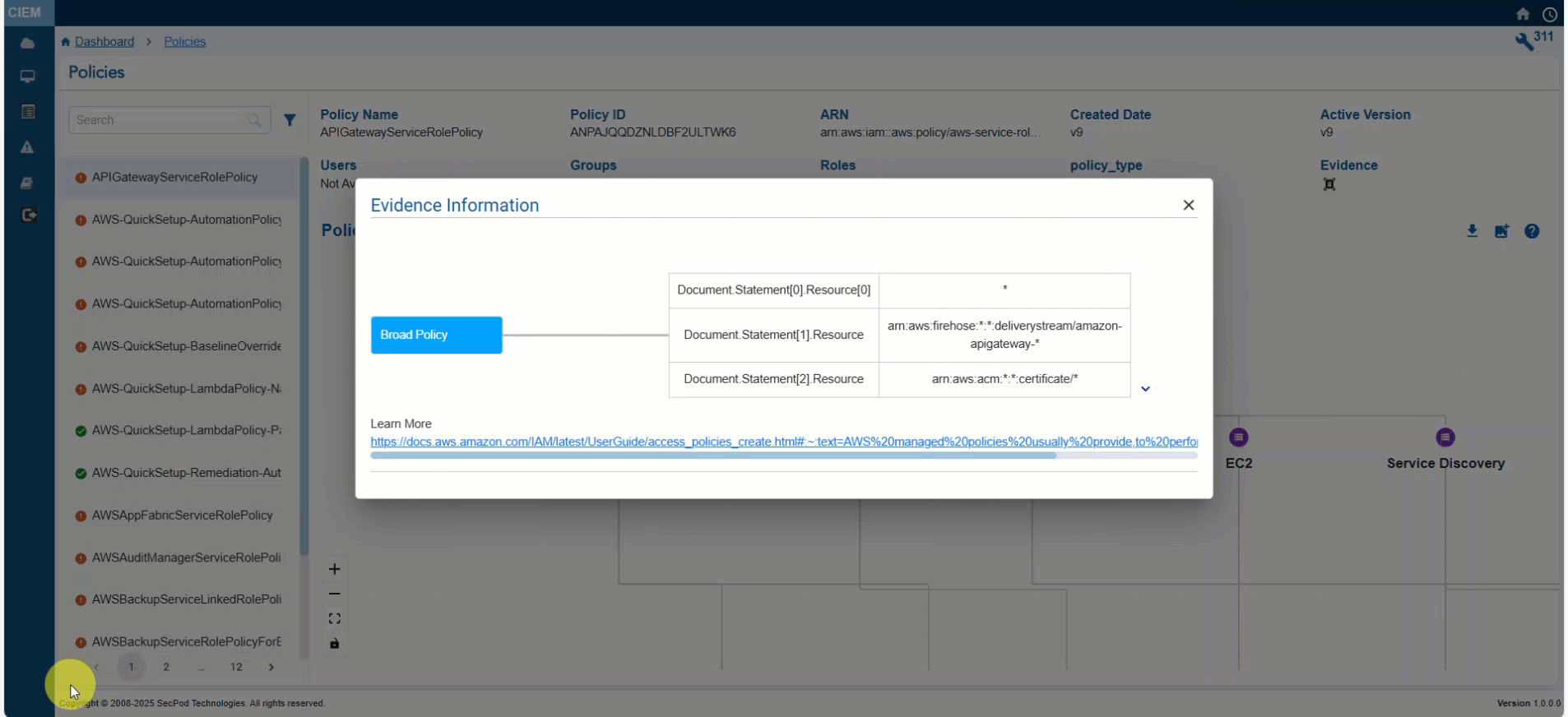
Visually Seeing the Relationship between Identity, Entitlement, Policy, or Permission
Saner CIEM offers a built-in Policy Details Map that provides a visual representation of the relationships between an identity (user, group, role, or service account) and its entitlements, policies, and permissions in a cloud environment. It helps security teams understand how an identity can access resources and identify potential risks or policy misconfigurations.
Using Evidence to Address Policies with Excessive Permission
When reviewing a policy, use the Evidence for Excessive Permission that pinpoints unnecessary permissions in AWS IAM policies and helps you understand and address excessive permissions.
Knowing the Excessive Permissions on a Specific Service
Excessive permissions can lead to unauthorized access, data breaches, or misuse of resources, so identifying them is critical. Saner CIEM helps identify excessive permissions and ensures your resources are only accessible by those who need them, reducing security risks.
Troubleshooting or Analyzing with Critical Activity Logs
Critical activity logs are essential for monitoring, auditing, and securing cloud environments. These logs help organizations track actions, events, detect anomalies, and ensure compliance with security and governance policies.
Saner CIEM captures key security-related actions and events that could indicate a potential threat, policy violation, or operational issue. Every column provides vital piece of context about the logged event, enabling enhanced visibility, quick analysis, incident response, and compliance.
6. Cloud Security Remediation (CSRM) Management: Automates patch distribution for CSPM, CIEM, and CSPA, ensuring vulnerabilities are quickly mitigated
Getting a Focused View of the Patch Details and Status for Each Tool
Saner CSRM allows you to quickly access the necessary tool for remediation and begin patching tasks. You can select the relevant tool: CSPM, CIEM, or CSPA(displayed as links) from the top-right of the dashboard to access the section in CSRM for remediation.
Addressing Missing Patches Via Remediation Tasks
Addressing missing patches by creating remediation tasks is crucial for maintaining the security and stability of IT infrastructure. Saner CSRM provides a wizard-based approach to creating a remediation task for the missing patches.
Prioritizing Patches Across Tools that have the Highest Security Impact
Saner CSRM helps you identify the Top 10 missing patches across CSPM, CIEM, and CSPA that have the highest security impact. Patches are ranked based on a weighted score considering severity and the number of affected resources, ensuring the most critical anomalies are addressed first.
Prioritizing and Addressing Older and High-Risk Anomalies
A time-based line plot shows the correlation between the number of pending patches and their age in days, helping teams address older, high-risk vulnerabilities first. The Patch Aging chart in Saner CSPA dashboard visually represents the duration during which patches remain unapplied in an IT environment. It illustrates the relationship between the number of pending patches and the number of days they have been outstanding.
This chart assists organizations in tracking and managing their patch deployment timelines. An upward trend indicates delays in patch deployment, which increases the organization’s exposure to vulnerabilities over an extended period. The creative visual employs characters or icons along the timeline to depict different stages of patch aging, including growth, decline, and subsequent resurgence.
Developing a Clear Understanding to Evaluate the Remediation Efforts
The Patching Impact Chart in Saner CSRM plots the number of security rules fixed against the number of patches applied, offering a clear understanding on the effectiveness of remediation efforts.
Initiating the Patch Remediation Process
You can begin the patch remediation process by following these steps in order: Finalize the job creation, Select the affected resources, Review the summary and adjust your selections as needed (this may involve skipping unnecessary patches), Enter the scheduling details, Assign a unique job name, Configure any additional options, if applicable, and Review the summary again.
At the final step of patching tasks creation, users with approval permissions can either approve the execution immediately or create a task for approval. Only approved tasks proceed to execution.
7. AI
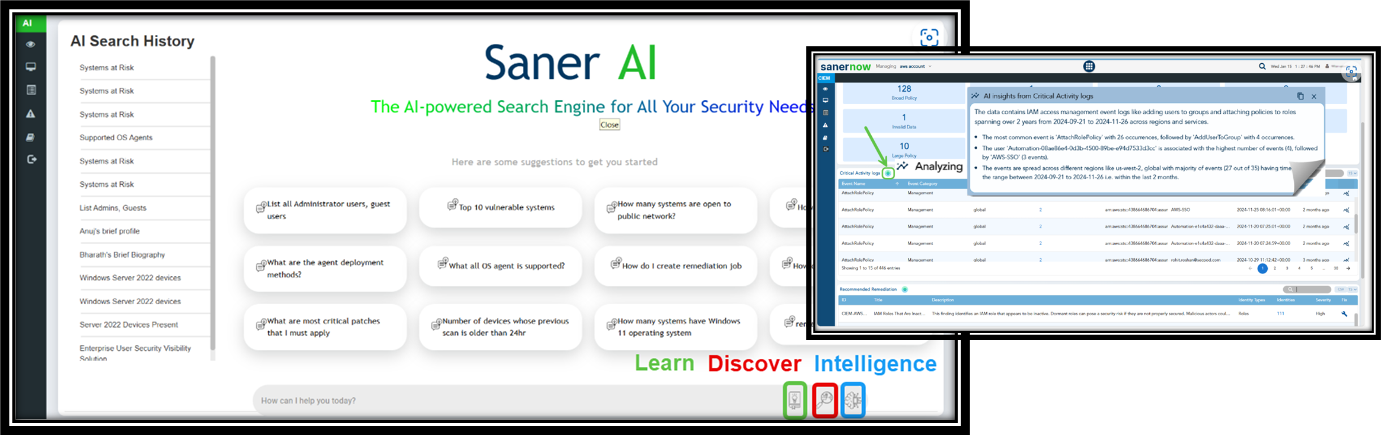
Saner Cloud features a powerful AI assistant designed to help you quickly access information across various dashboards and categories. This functionality saves time, increases efficiency, and enhances the overall user experience by providing instant, relevant information on demand.
The AI assistant is activated by clicking the green icon within any dashboard block. This action allows the assistant to understand the context of the displayed data and summarize crucial information in a tooltip format.
Users can also pose queries across three main categories: Learn, Discover, and Saner Intelligence. It serves as a versatile tool for various use cases, whether you’re searching for general learning resources, in-depth discoveries, or advanced intelligence insights. This function acts as a central hub for interacting with the AI.
8. Alerts
Saner Cloud provides pre-built conditions for each alert that’s based on standard compliance specifications and overall security posture. Response configuration also helps you to perform patch remediation tasks as needed. Different types include:
- Asset Exposure Alerts
- Posture Anomaly Alerts
- Identity Entitlement Management Alerts
- Remediation Management Alerts
9. Reports
Saner Cloud provides the flexibility to use multiple predefined report views, known as Canned Reports, as well as the option to create Custom Report views. These report views allow you to set a specific time range or backup schedule, which is helpful for analyzing data over a designated period. Additionally, you can share these report views with others and perform various operations to enhance collaboration and analysis.
10. Tags to Search and Filter
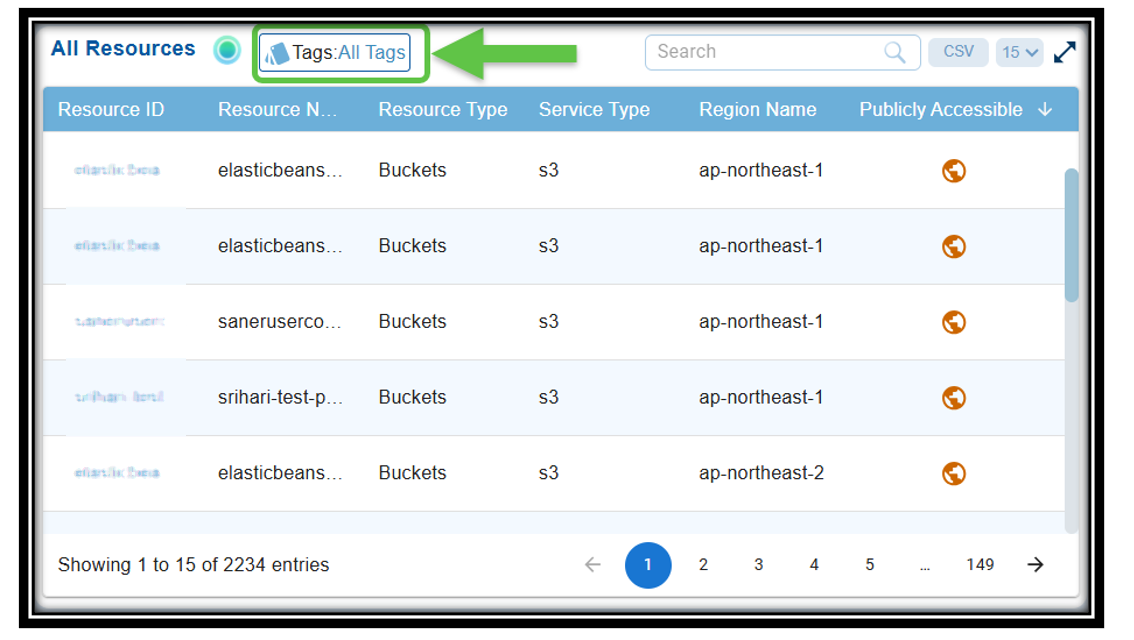
Saner Cloud simplifies the searching and filtering of resources using tags. Instead of manually browsing through hundreds or thousands of resources, you can quickly filter relevant ones by using tags. With tags available across different tools, users can efficiently filter and retrieve specific resources in large environments.
11. Audit Logs
Each tool within Saner Cloud has its own set of unique job codes, ensuring that events occurring within a particular tool are distinctly categorized and easily traceable. This structured approach to capturing and categorizing events ensures detailed visibility into application usage, supporting effective auditing and troubleshooting.


