Release Date: 3rd Feb 2026
This release provides significant upgrades to Azure and AWS Cloud Identities and Entitlement Management (CIEM) modules in Saner Cloud, providing an intuitive view of excessive and dormant IAM role assignments. A scope-based perspective, a redesigned UI, and improved visualizations are introduced to enable faster analysis of excessive permissions, permissive actions, and evidence. Saner CIEM clearly categorizes roles into Entra and RBAC, alongside refined filters for smoother navigation and streamlined workflows. In addition, extended misconfiguration coverage in remediation flow suggestions helps teams identify and address security gaps more effectively. The CIEM module in Azure and AWS has been enhanced with new charts and tables for improved visibility.
Azure CIEM Enhancements
Visibility into Custom and Built-in Role Distribution for Entra and RBAC Roles
Grasp the balance between built-in roles (defined by Microsoft Azure) and custom roles (tailored to the organization) in the context of Entra or RBAC assigned to an entity.
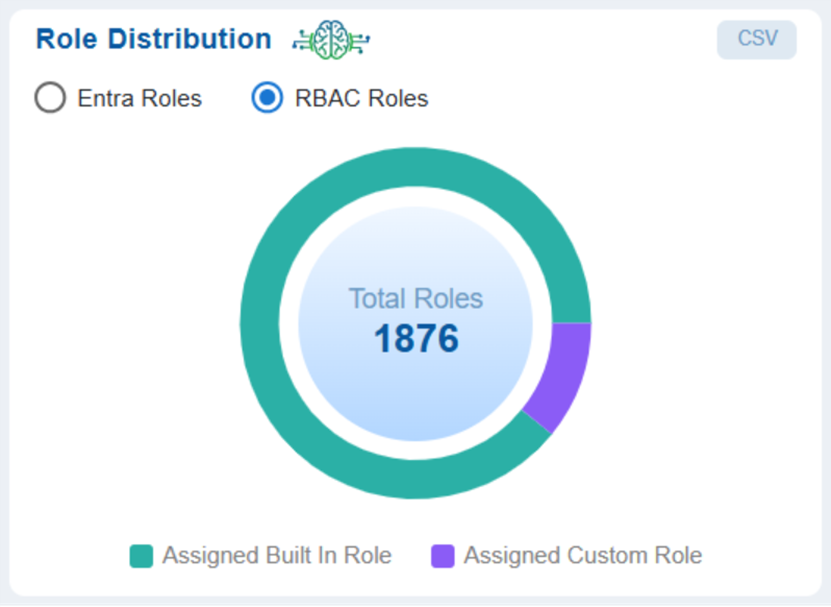
Understanding the Role Distribution helps determine if your organization relies heavily on custom roles that could pose complexity or risks if not properly audited, or utilize built-in roles whenever possible.
Actionable Insight into Azure Role Assignments
Limited visibility into role assignments across various scope levels, such as tenant, subscription, and resource group, makes it challenging for organizations to enforce least-privilege access and identify excessive permissions.
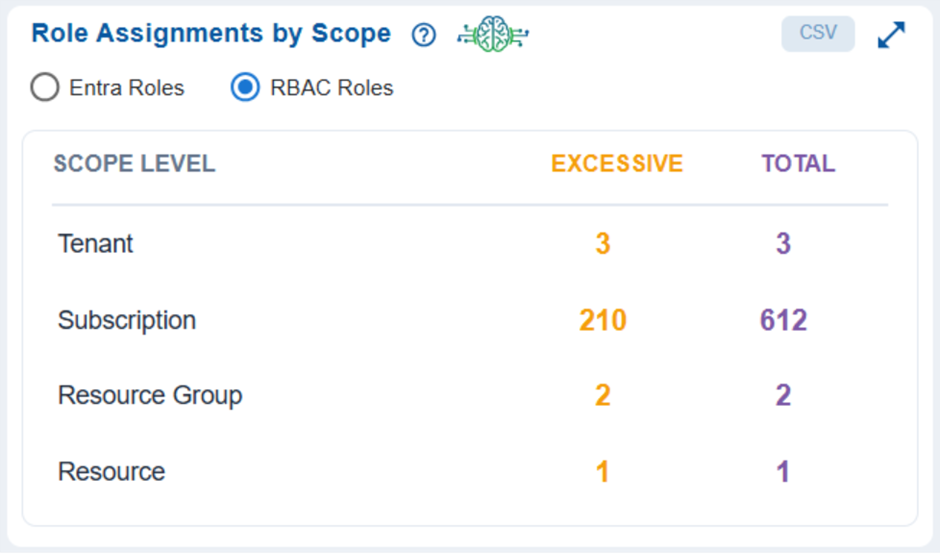
The Role Assignments by Scope in Saner CIEM addresses this issue by providing centralized visibility into Azure RBAC or Entra role assignments across all scope levels. It clearly identifies areas where excessive permissions exist, enabling organizations to effectively enforce least-privilege access and accelerate their remediation efforts.
Spot Excessive Permissions Posing High Risk for Entra and RBAC Roles
The Entra or RBAC Roles with Excessive Permissions view highlights important risk indicators that include Wide Access Policies that show roles that have broad or unrestricted access, Administrative Privileges that indicate roles that possess high-level administrative capabilities, Privileged Access Roles that identify roles classified as privileged within Azure Entra, and Elevated Actions that represent roles that can perform powerful or sensitive operations.
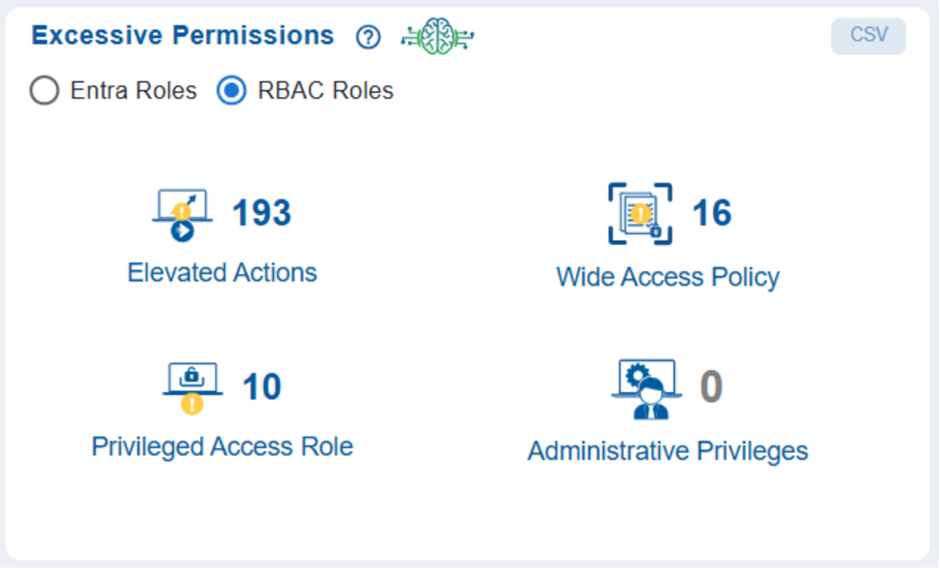
With the high-risk access patterns revealed, security teams can quickly prioritize investigations, assess their impact, and take swift action to mitigate exposure and strengthen access governance.
Top Privileged Roles at a Glance
A quick overview of roles with elevated permissions and their underlying assignments allows administrators to monitor potential risks.
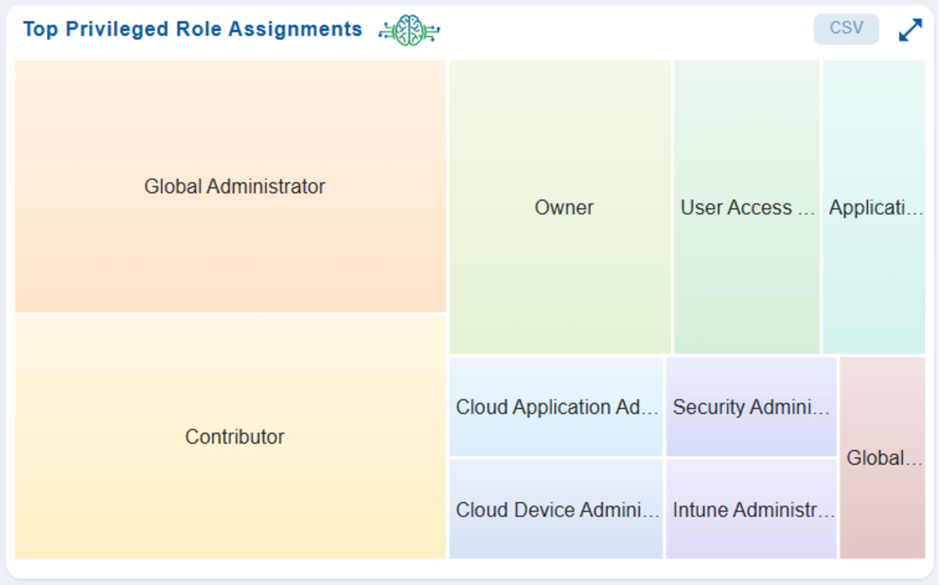
The interactive heat map offers a visual representation of role distribution, while clicking on any assignment in the pie chart leads to a detailed view with an in-depth breakdown of role assignment information.
Azure and AWS CIEM Enhancements
Remediation with Enhanced REM Flow Suggestions
Contextual suggestions are provided at every data point, offering appropriate values to guide remediation actions. For example, when a misconfiguration is detected, recommended values can be automatically pulled from discovered resources via integrated modules such as CSAE.
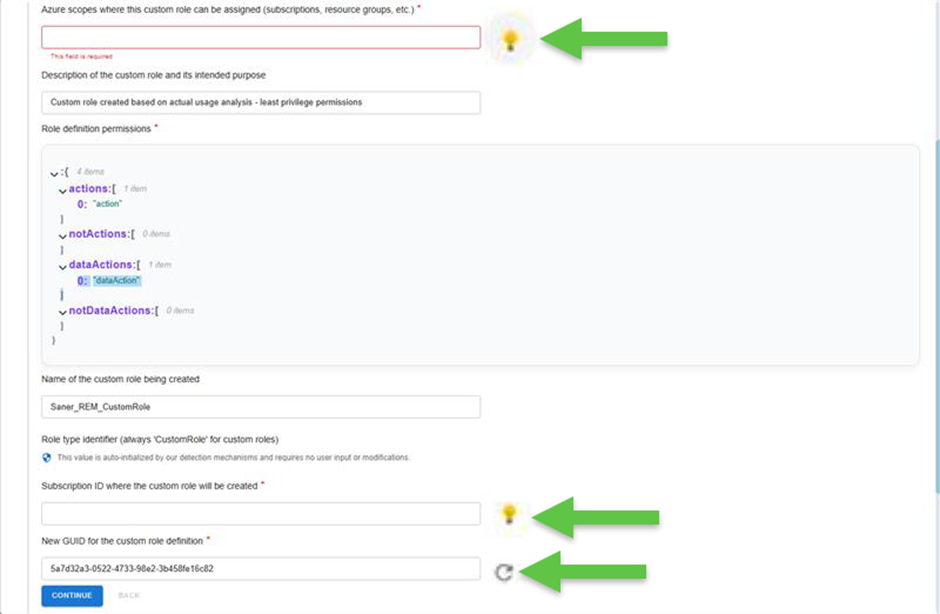
This feature simplifies remediation and helps security teams maintain a robust and compliant environment.
Deeper Insight into Permissions with Detailed Graphs
The detailed graphs with flexible layouts, provides clearer visibility into Excessive Permissions, Permissive Actions, and Evidence. Each node emphasizes a key element in the chain of role, permissions, resource, and evidence, making it easier to identify excessive or risky permissions and understand why they are flagged.
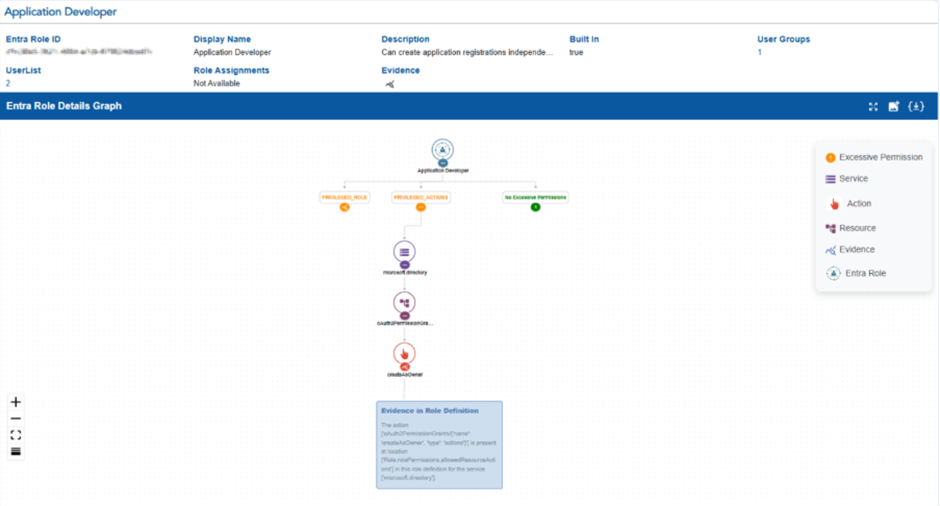
These updates enable users to analyze permission risks more effectively and make quicker informed decisions.
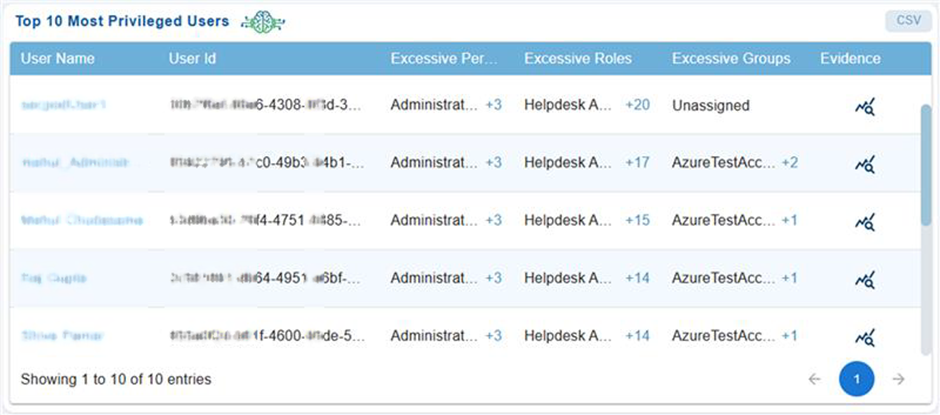
Secure Over-Privileged Users Instantly
Top 10 Privileged Users offers clear visibility into excessive permissions across roles and groups, supported by compelling evidence.
Azure
AWS:
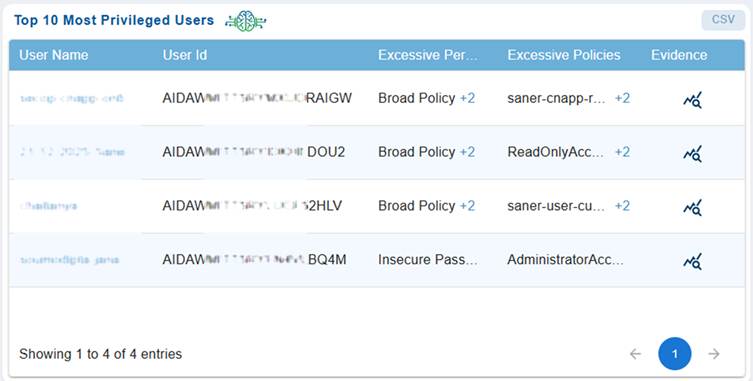
This facilitates quicker risk assessment, enhances least-privilege enforcement, and speeds up the remediation of over-privileged accounts, helping organizations remain secure and compliant effortlessly.
Enhanced Risk Prioritization with CIEM Insights
Cloud Security Risk Prioritization (CSRP) now incorporates CIEM (Cloud Infrastructure Entitlement Management) findings alongside CSPM (Cloud Security Posture Management) insights to deliver more accurate cloud risk prioritization. This enhancement enables users to identify and address the most critical risks first, with improved prioritization accuracy.
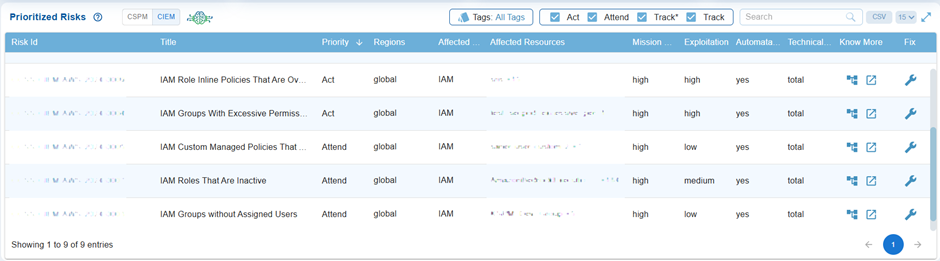
The remediation actions can also now be initiated directly from the CSRP module, with seamless navigation to CSRM (Cloud Security Remediation Management) for efficient risk resolution.
You need to onboard again in-order to leverage the capabilities of the newly added CIEM detection rules and their remediation. Existing data will be preserved even after you onboard.


