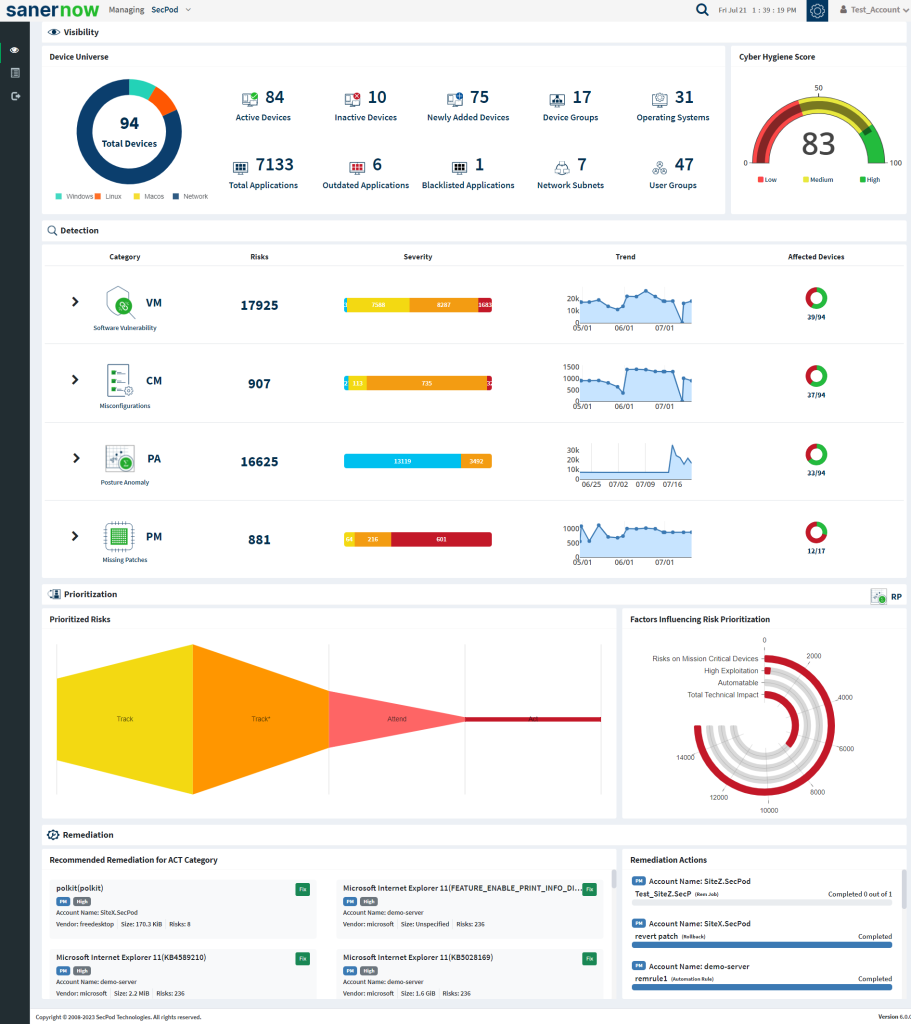
Applying security patches is the primary method for eliminating vulnerabilities in software. Patch management involves deciding what patches should be applied and when they should be applied and applying the patches. Saner PM provides access to the latest vendor patches that experts test. With its capability to identify vulnerabilities and map appropriate patches to remove vulnerabilities, Saner PM automates the process of security patch management and keeps endpoint systems up to date. Saner PM also provides crucial information on the severity of detected vulnerabilities, which helps decide whether to apply patches.
Patch Management automates the end-to-end patching tasks from scanning to deployment to reduce the attack surface and enhance security posture effectively. It supports patching for all major OSs such as Windows, Mac, Linux, firmware, and many third-party applications. Patch Management detects all the missing patches for the vulnerabilities across the network. Patch management help to simplify and automate all the patching needs. With the help of smart patching technology, Saner PM provides an end-to-end automated patch management system.
To access the Patch Management tool:
- Log in to Saner platform using your credentials.
- Suppose an account already exists and the Saner Agent has been deployed on the endpoints; the organization level dashboard is displayed.
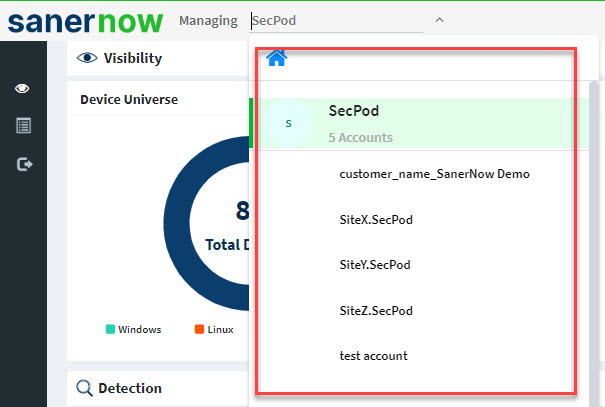
- To select an account, click the drop-down box on the top left corner of the dashboard. The Organizations and the Accounts belonging to the Organization are listed.
- Click the Saner tools icon on the header. It will display all the provision tools, as shown below.
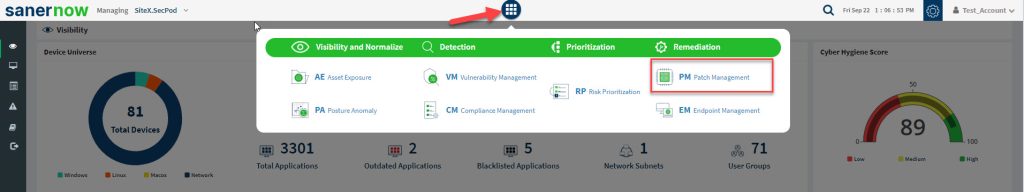
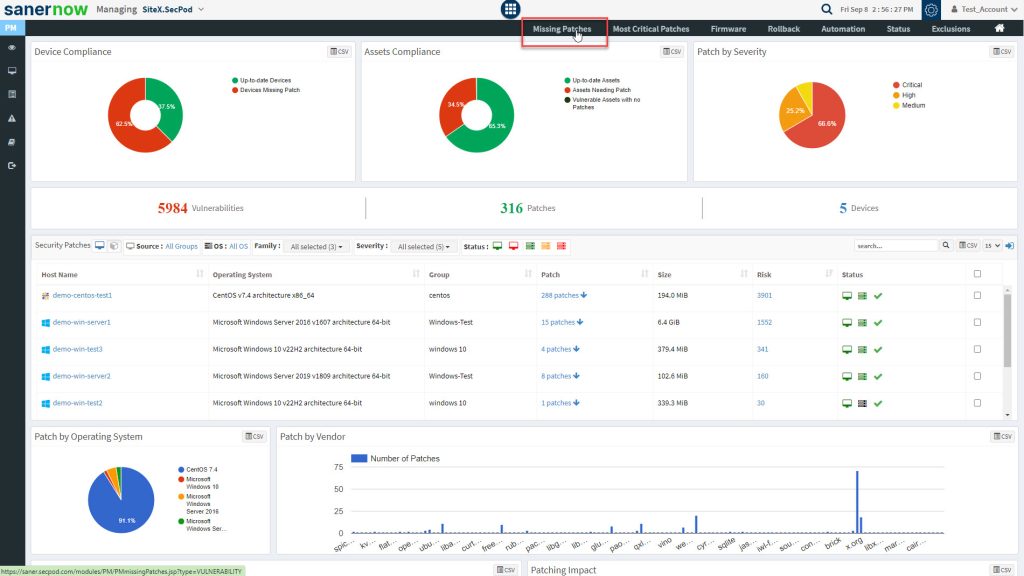
- Click the Patch Management icon. The Patch Management dashboard is displayed, which provides an overview of all devices and patching activities. And it helps you take action to install patches to remediate vulnerabilities.
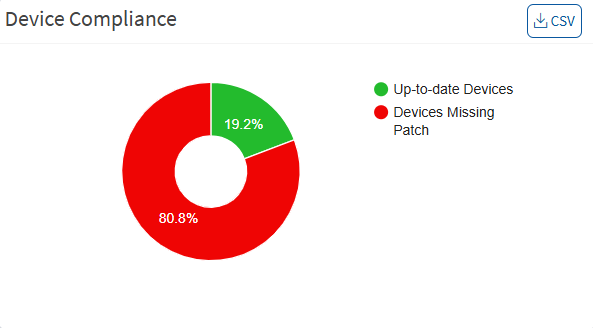
Device Compliance
This pane shows the device’s compliance posture and highlights the percentage of up-to-date devices and devices that need to apply patches. You can download an excel sheet of non-patched and up-to-date devices by clicking the CSV icon.
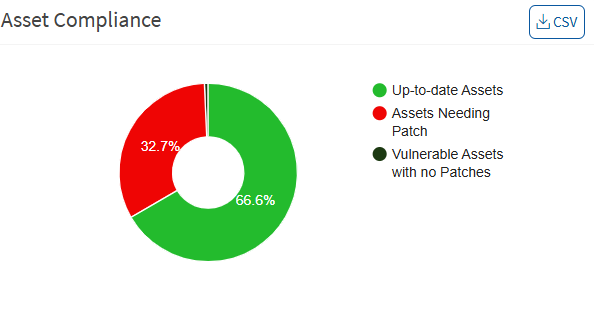
Asset Compliance
This pane shows the asset’s compliance posture. It highlights the percentage of up-to-date software applications, how many assets need patching activity, and the percentage of vulnerable assets with no patches. You can download an excel sheet of asset compliance details by clicking the CSV icon.
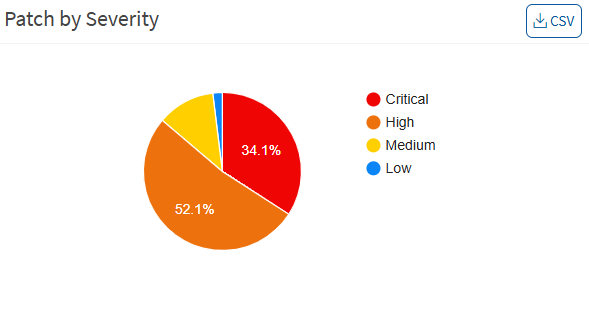
Patch by Severity
This page shows the patches based on the severity: critical, high, medium, and low. You can download an excel sheet of patch details with severity by clicking the CSV icon.
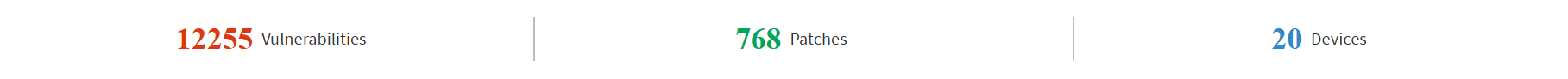
The patch management dashboard also lists the total number of vulnerabilities, the number of patches, and a total number of devices.
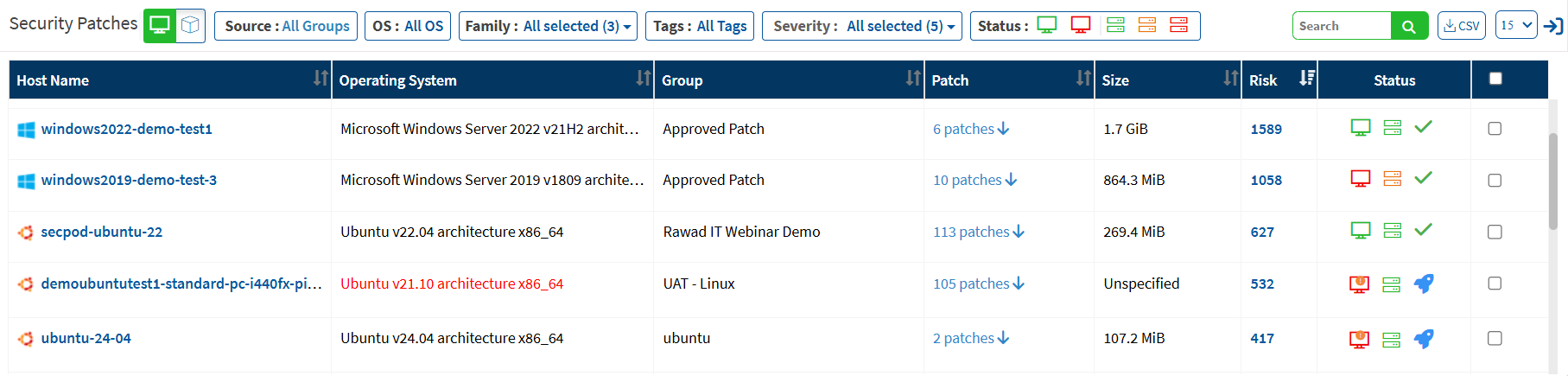
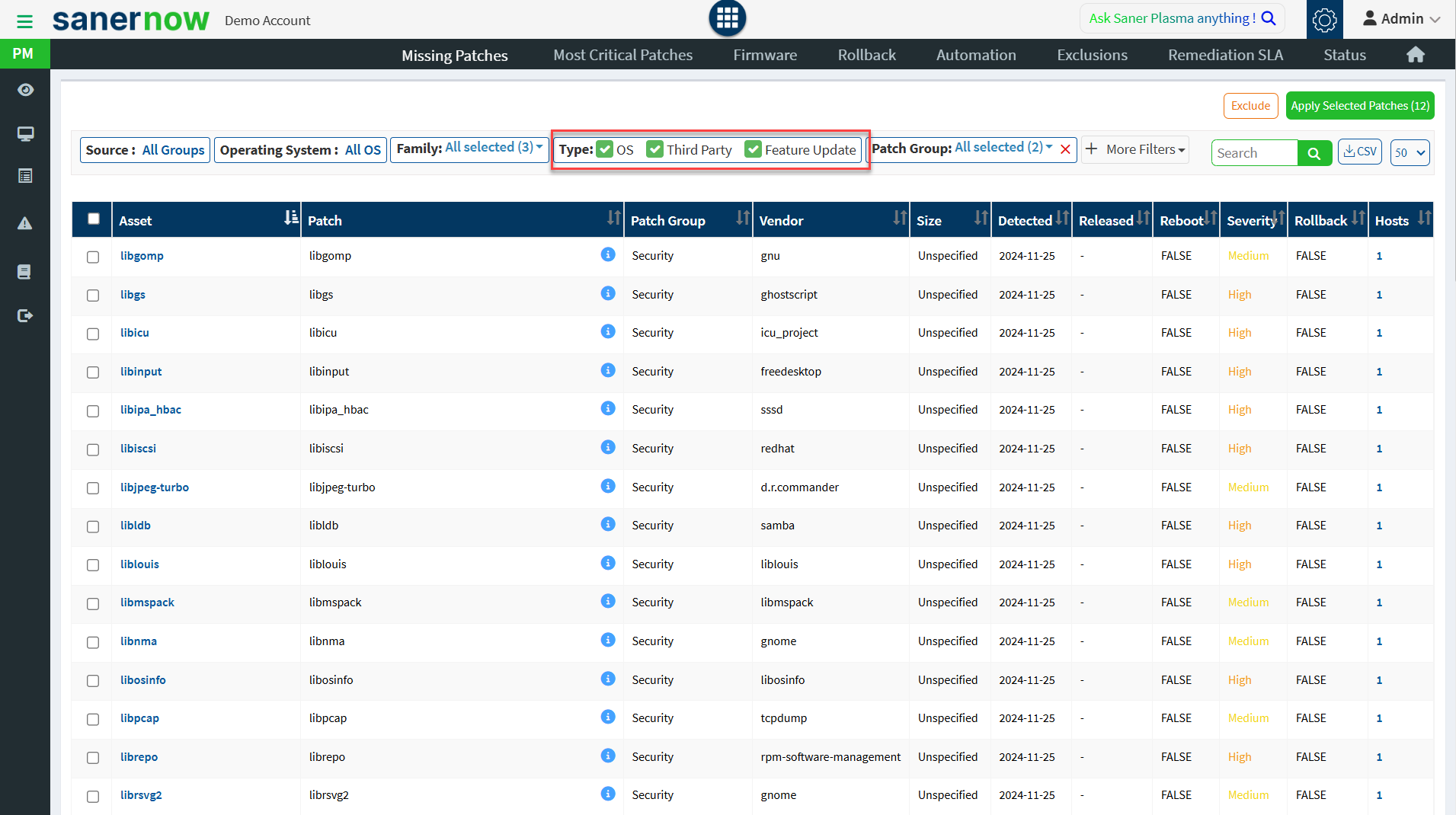
Security Patches
This pane shows the number of missing patches for devices. Click on the down arrow to expand the missing patches list. Each device’s information, such as operating system, group, size, risk, and device status, is listed on the table. This information will be helpful for a user to deploy the patches. You can apply filters to view the devices based on groups, operating systems, family, severity, the device status. The search option is provided to search the devices with missing patch information with multiple search options.
Security patches based on the devices and assets are displayed on this page. Click on the asset icon to see the missing patches for the assets. This pane shows the level of risk due to the missing patch, the size, date, vendor who publishes the patch, and whether a reboot will be required to apply the patch. It also shows the number of affected hosts. Search and filter options are available to view specific assets. You can download an excel sheet of patch details based on the devices and assets by clicking the CSV icon.
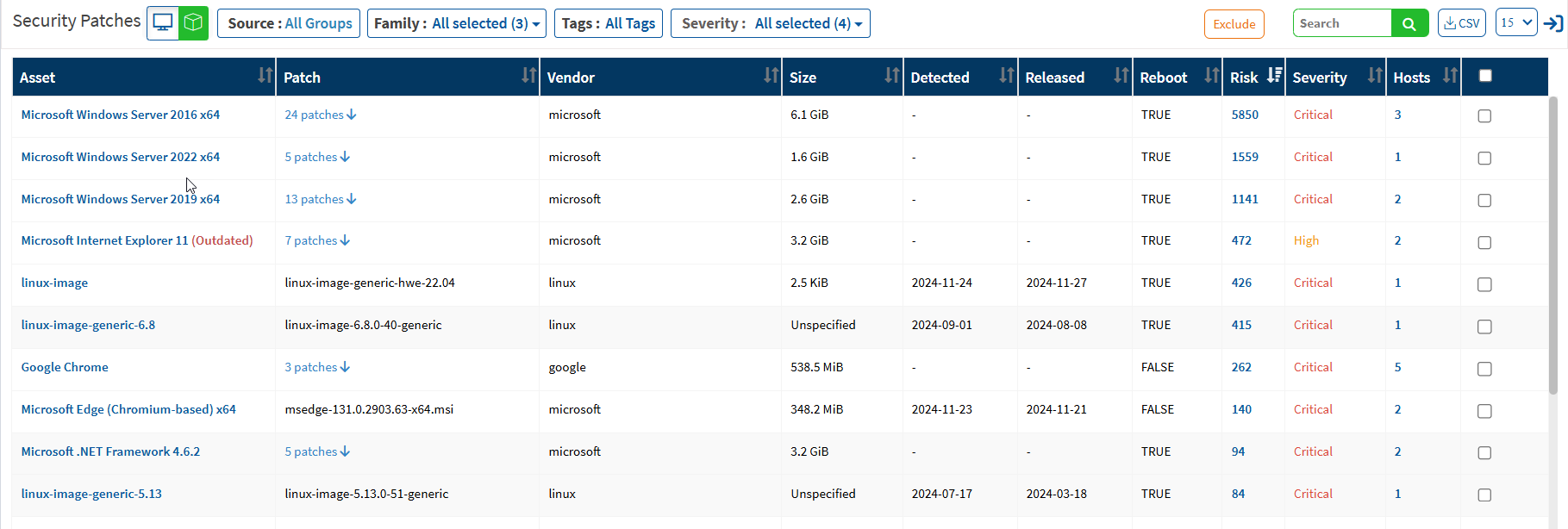
Patch by Operating System
This pane shows the distribution of missing patches based on the operating system; it lets you see which operating systems in your organization have the most significant number of missing patches. You can download an excel sheet of missing patches segregated based on the operating system by clicking the CSV icon.
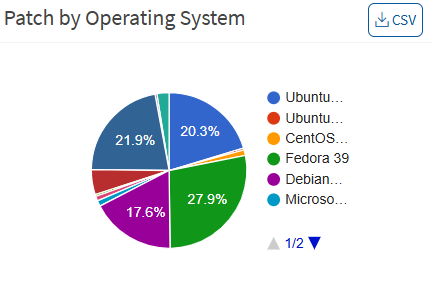
Patch by Vendor
This pane shows the patches categorized by the vendor, allowing you to understand which assets or vendors have the most updates. You can download an excel sheet of patch details based on the publisher by clicking the CSV icon.
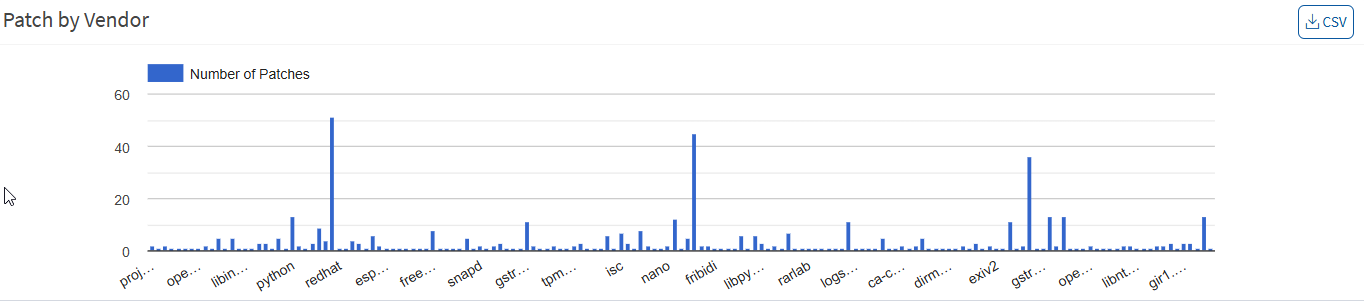
Patch Aging
This pane shows the number of days since a patch has been available but not applied. You can download an excel sheet of patch details based on age by clicking the CSV icon.
Patching Impact
This pane highlights the number of vulnerabilities that are removed by applying patches. This helps prioritize patching based on the acceptable vulnerability count, security audits, safety, the criticality of the unpatched systems, etc. You can download an excel sheet of patching impact by clicking the CSV icon.
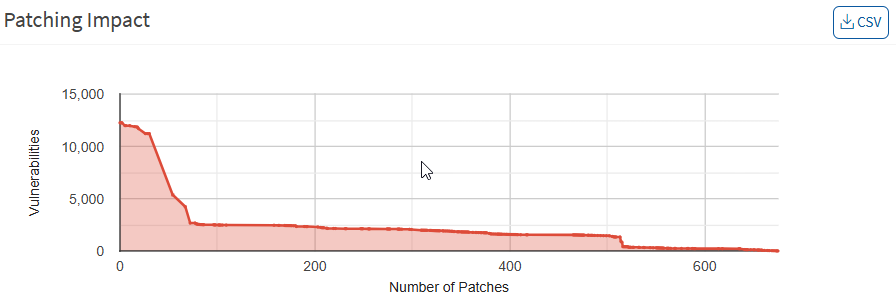
Missing Patches
You can create remediation jobs for security and non-security patches using Saner PM. Saner PM lists all the security, non-security, and feature upgrade patches on a single page, allowing you to create remediation jobs that include security and non-security patches.
You can further categorize the patches into the following categories:
- Operating System
- Third-Party
- Feature Update
Additionally, you can filter patches using filters available under More Filters.
- Tags
- Patch Group
- Severity
- Detected Date
- Release Date
The Tags filter allows you to specify tags to filter the patches per your requirements.
The Patch Group filter allows you to choose between Security and Non-Security patches.
The Severity filter allows you to filter patches depending on the severity levelofeach patch. You can choose from the following severity values.
- Critical
- High
- Medium
- Low
- None
The Detection Date filter allows you to filter patches based on the date Saner PM detected the patches. The Released Date filter allows you to filter patches based on the date the vendor released the patches.
It also shows the number of affected hosts. You will get detailed asset information with patching details by clicking on the asset below.
You can apply filter options to view the list of missing patches by groups, operating systems, family, severity, and type, and you can search for the required device or group. You create multiple remediation jobs and automation rules for a single device or a group of devices.
You can remediate missing patches in two ways:
- As a one-time task to apply patches on a device or devices: You can create a Job every time you need to apply missing patches.
- As an automated task scheduled to apply any missing patches discovered by the last scan executed by the Saner Agent: You can create a scheduled task that will run according to defined parameters. Refer to the Automation section for more details.
Non-Security Patching for third-party applications.
Saner PM tool supports updating non-security feature updates. for 400+ third-party applications. Follow the below steps to apply non-security feature updates for third-party applications.
Step 1: Click the Missing Patches button on the Saner PM dashboard to navigate to Missing Patches screen.
Step 2: On the Missing Patches screen, select Non-security option on the left-side of the screen.
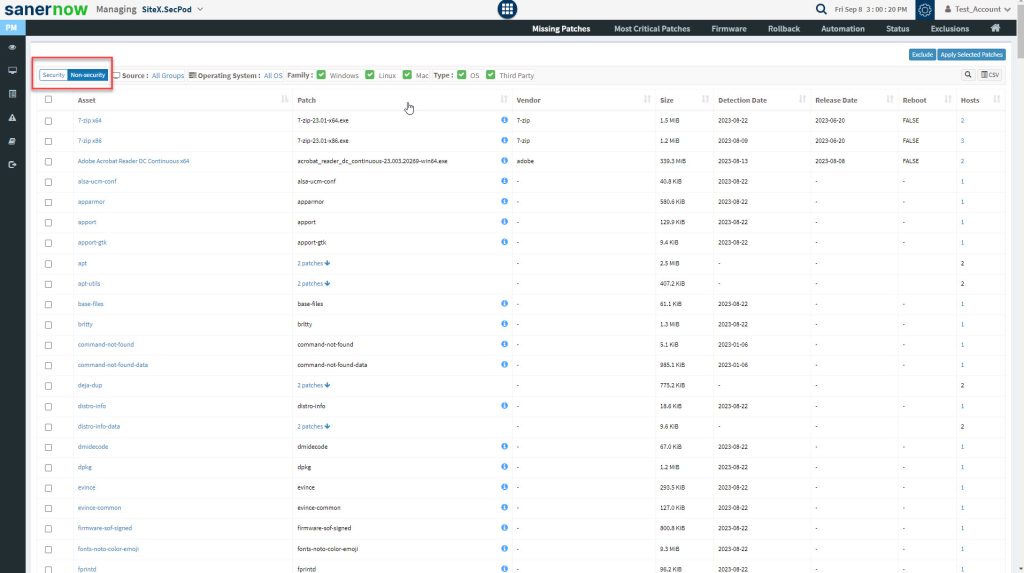
Step 3: Uncheck the OS checkbox to display non-security patches available for third-party applications present in the Account.
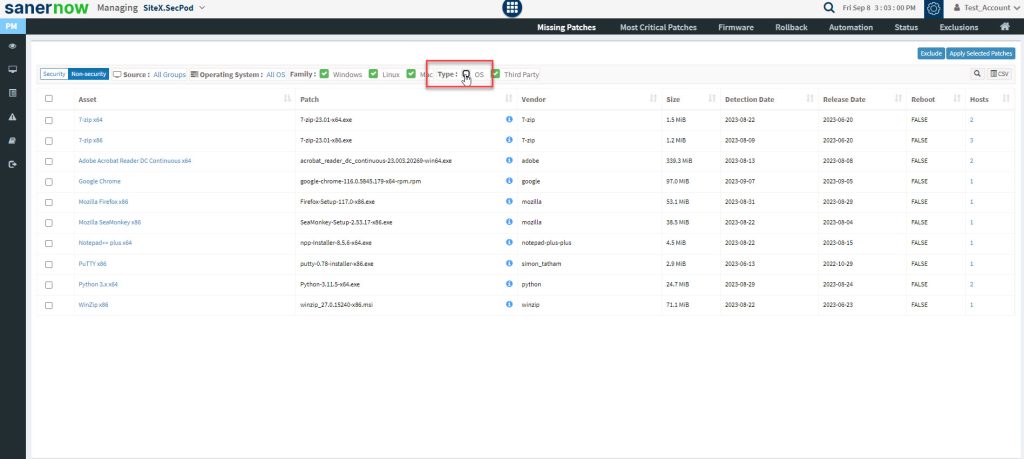
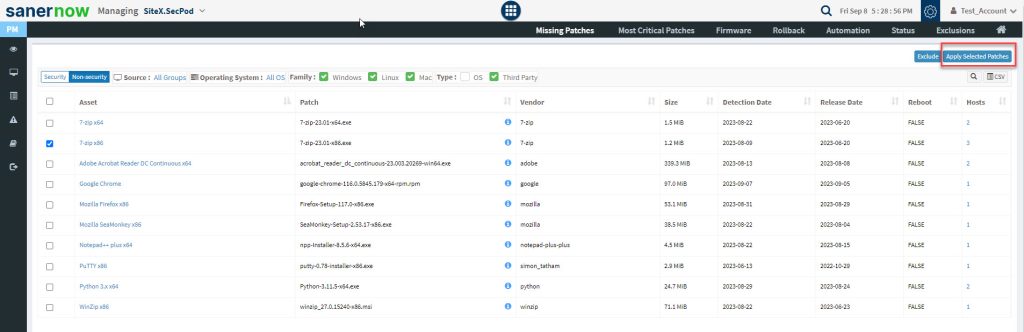
Step 4: Select the application and click the Apply Selected Patches button.
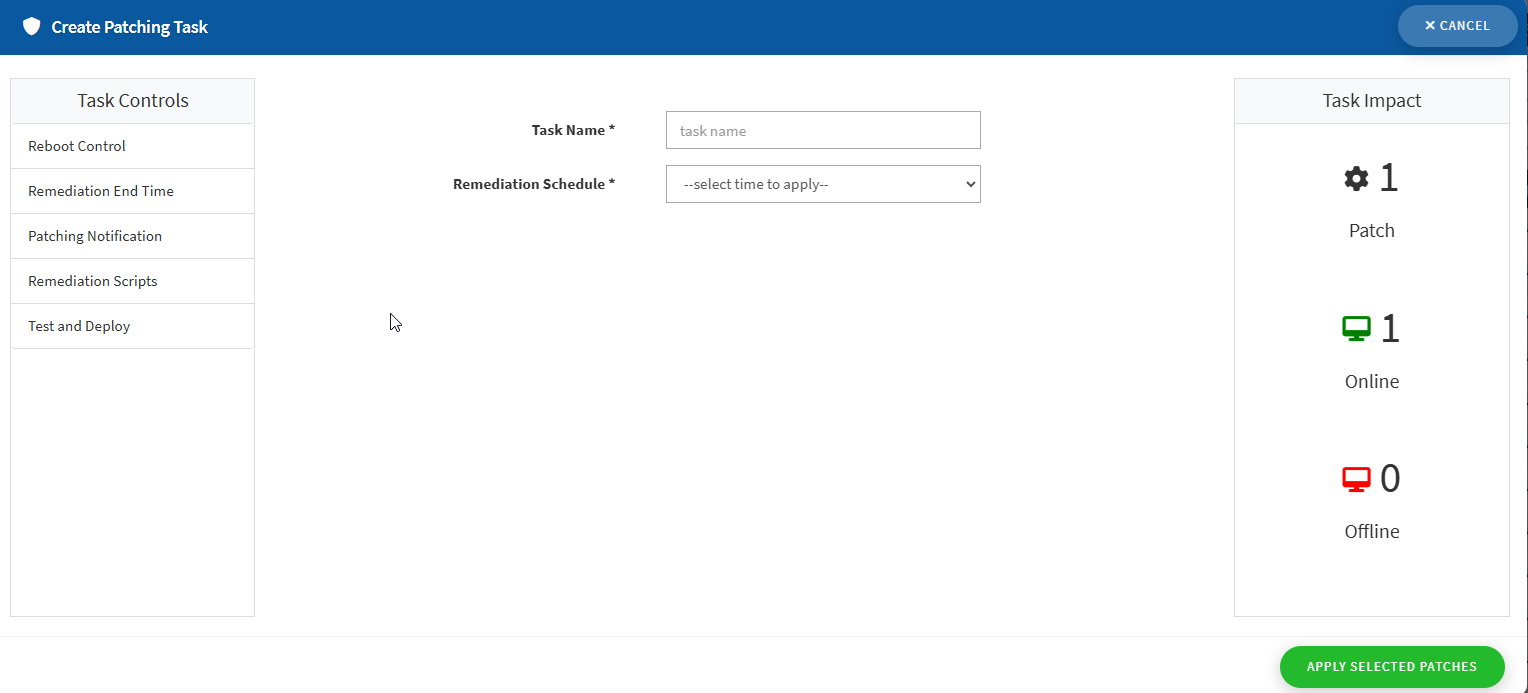
Step 5: You will be directed to Create Patching Task screen. Here, on this screen, you need to specify the Task Name and Remediation Schedule – the timeframe during which you want the patches to be applied. You can choose between the following remediation schedules:
- Immediate — When the remediation schedule is selected as Immediate, the Saner PM tool will immediately perform the patching task.
- After Scheduled Scan —- When the remediation schedule is selected as After scheduled Scan, the Saner PM tool will perform the patching task once the Saner Agent completes the scheduled scan.
- Custom date —- When the remediation schedule is selected as Custom Date, you need to specify the Task Execution Date – the date on which you want the Saner PM tool to perform the patching task. At the same time, you need to provide values for Task Start Window (Task start window is a time period during which a task is allowed to start running. For example, a task might have a start window of 09:00 PM to 11:00 PM, which means that the task is allowed to start anytime within that time range. If the device is offline during the start time window, Task will not be taken up and will be reported as Scheduled missed.)
Step 6: Click the Apply Selected Patches button and the patching task is created.
Enable/Disable, Edit and Delete an existing Exclude Policy in PM tool
Follow the below steps on how to enable/disable, edit and delete an existing Exclude policy in Saner PM tool.
Step 1: On the PM Dashboard, click on Exclusions located at the top right corner of the page.
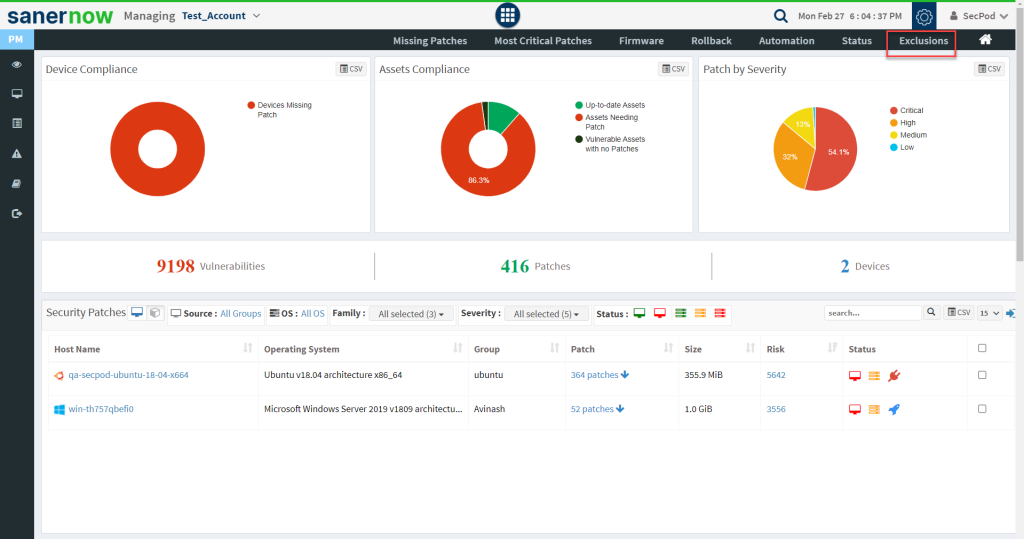
Step 2: You will be presented with a new screen. You can see all the Exclude Policies that exist in the account.
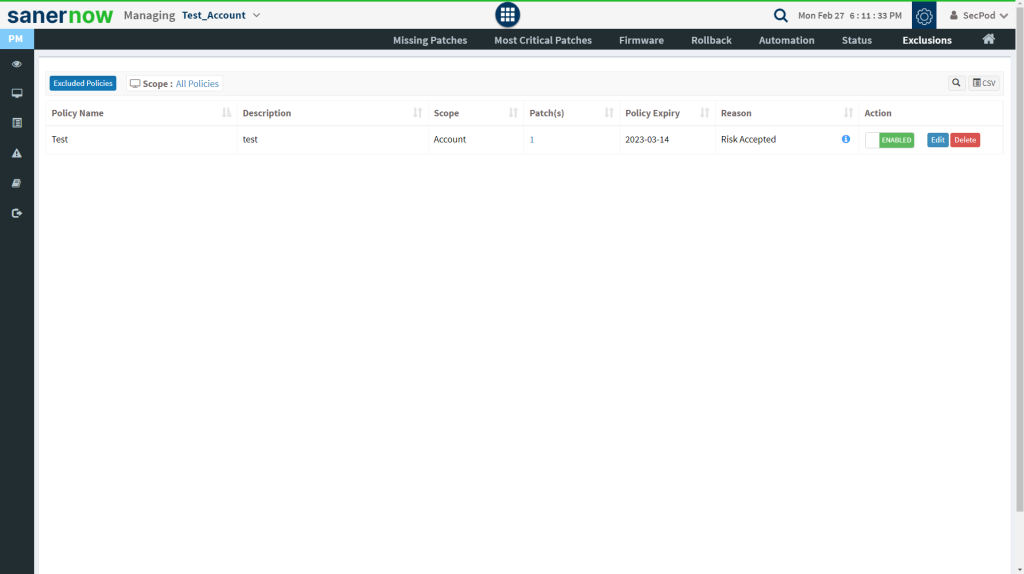
The last column on this page – Action presents you with three buttons namely – a toggle button -Enable /Disable, Edit, and Delete buttons that can be used to control Exclude policies.
To create a task for apply missing patches:
- Select the patches you want to install. Click on the Apply Selected Patches button at the top right corner of the missing patches page. The Create Patching Task dialog is displayed as shown in the below image.
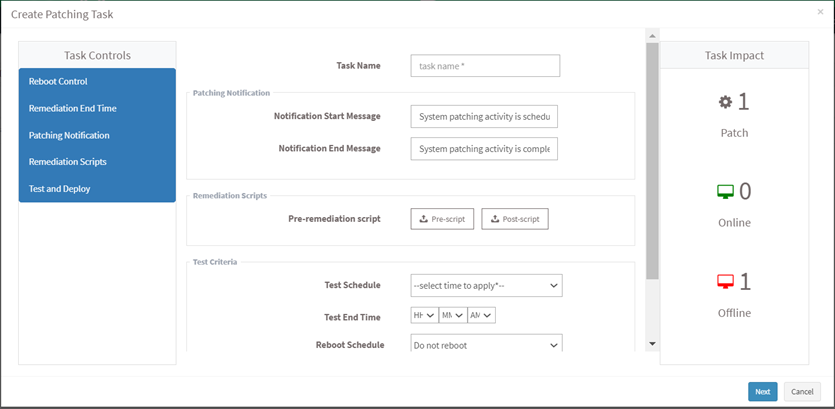
- Specify a task name, provide patching notification messages, and select remediation scripts.
- Select test criteria as shown in the below image.
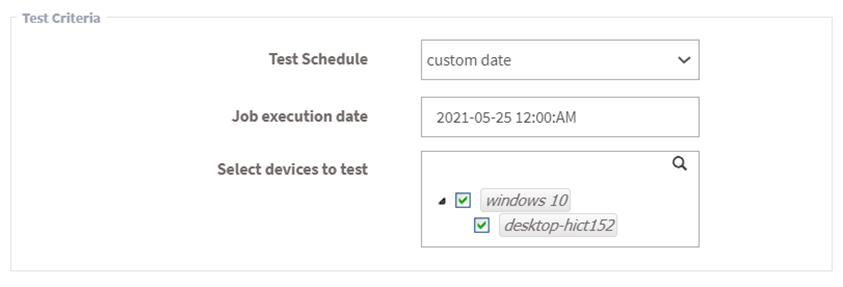
- Schedule the job immediately or after a scan and set the time counter accordingly in the test schedule fields. You can also choose to set the job to execute on a different date.
- Click on the Next button. Specify the details in the Deployment Criteria section. Click on the Test and Deploy Selected Patches button.
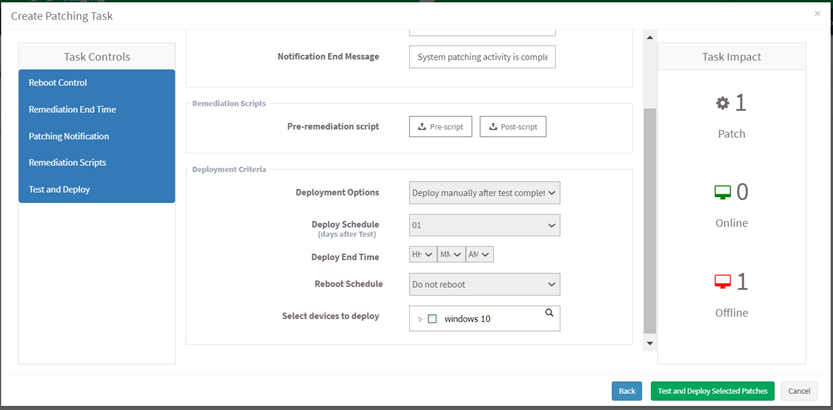
You will get a confirmation message that you created the job successfully.
Saner PM supports patch management for Windows, Linux, Mac operating systems, and third-party applications.
Operating System Patches
- Microsoft Updates
Patch Management for Microsoft updates works in two ways:
WSUS Server
If a Windows update is configured to contact the WSUS Server, the Saner agent directly contacts the WSUS Server to get the latest available patches. Otherwise, it will contact the Microsoft Update Server.
Default Microsoft Update Server
If a Windows update is configured to contact the Microsoft Update Server, the Saner agent directly contacts the Microsoft Update Server to get the latest available patches.
- Linux Machines
For RPM Machines
The Saner solution uses the YUM repository to install RPM package updates, which contacts the respective server to get the latest patches.
For DPKG Machines
Saner PM uses the apt-get package, a default package present in dpkg machines. The agent contacts the respective update server to get the latest patches.
- Mac OS X Packages
Saner PM uses the software update command to update OS X packages. The agent contacts the MAC OS X Update Server.
Third-party Application Patches
Please refer this link to learn more about the third-party applications Saner PM supports.
Performing Custom Remediation for applications needing paid patches
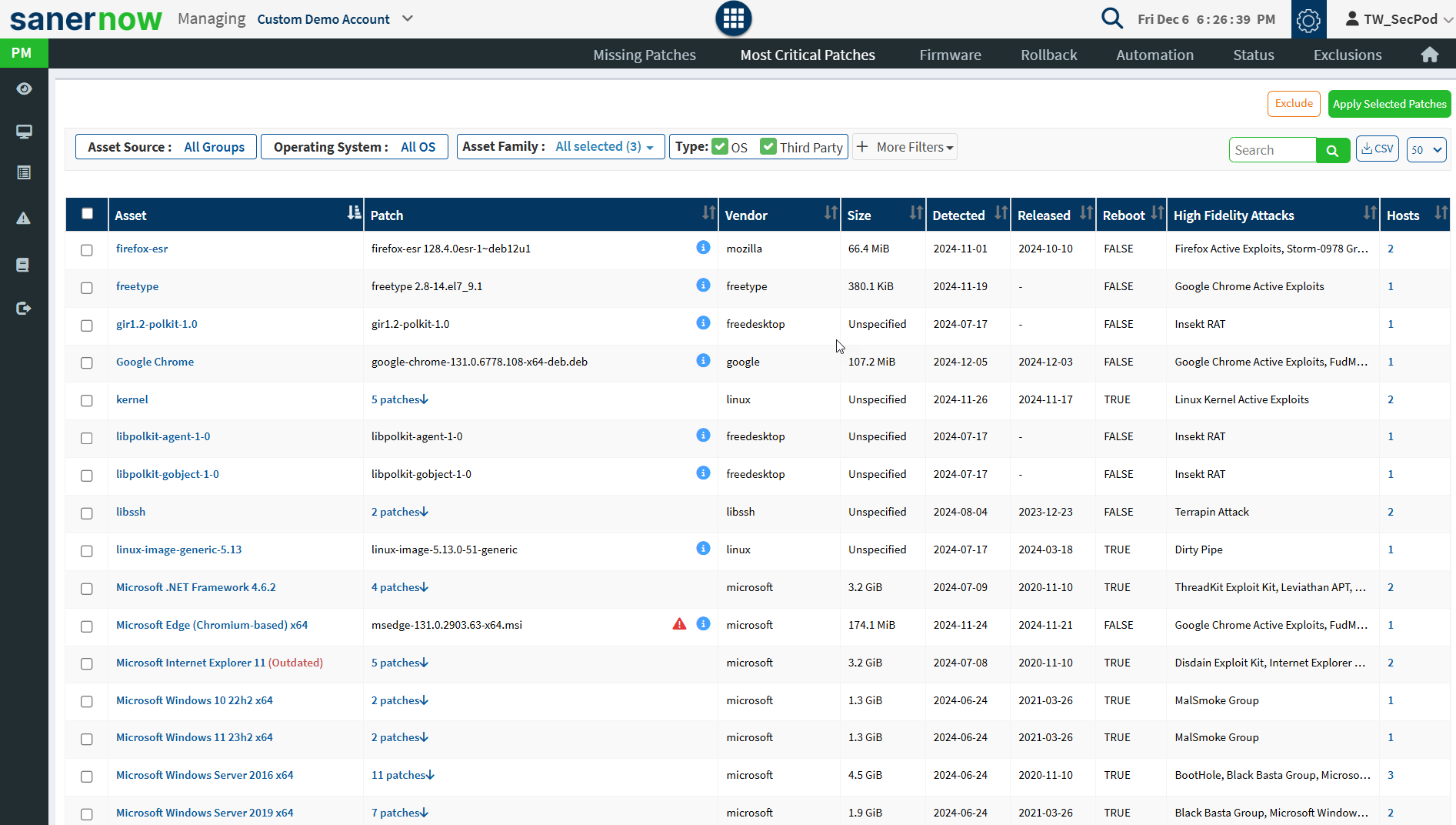
Most Critical Patches
This page lists the most critical patches to the security of the system and organization so that you can prioritize patching. It highlights the size, date, vendor who publishes the patch, and whether a reboot will be required to apply the patch.
To apply critical patches
- Select the patches you want to install. Click on the Apply Selected Patches button at the top right corner of the missing patches page. The Create Patching Task dialog is displayed as shown in the below image.
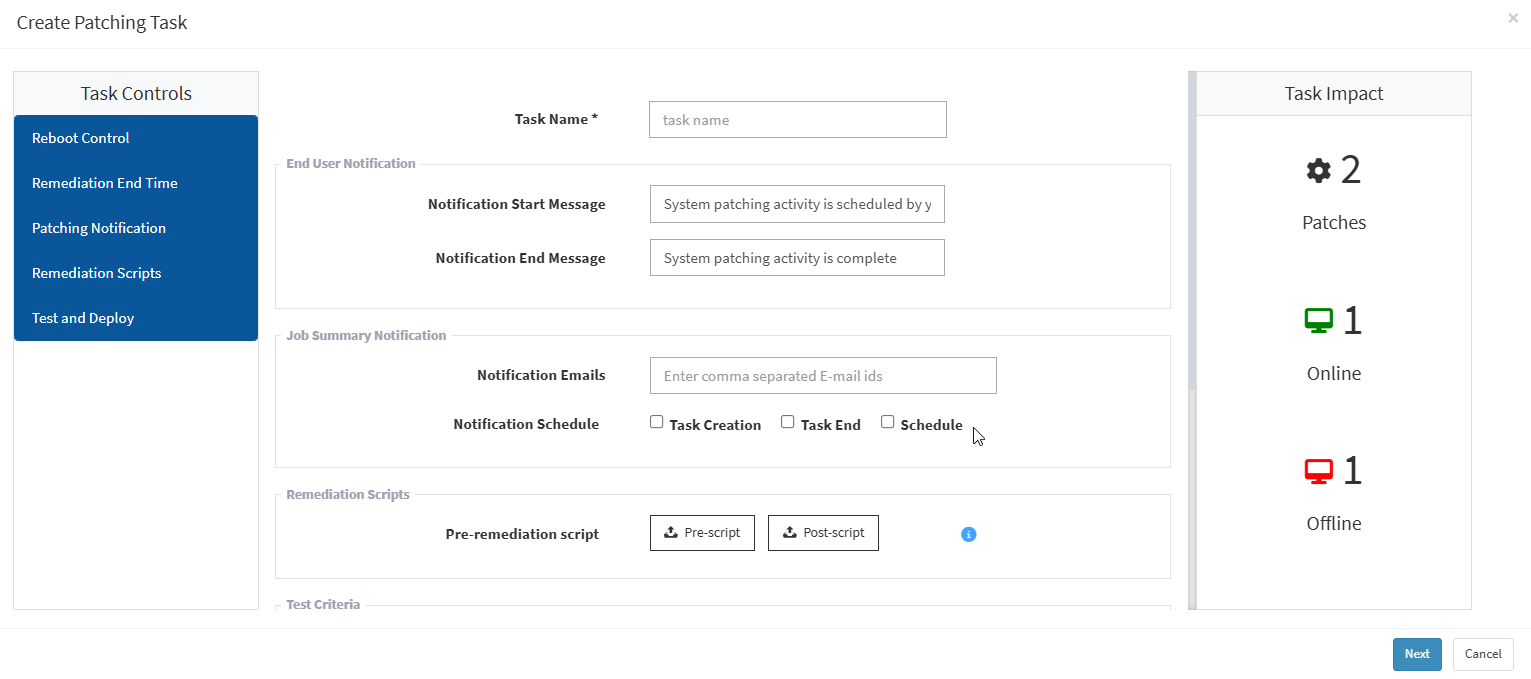
- Specify a task name, provide patching notification messages, and select remediation scripts.
- Select test criteria as shown in the below image.
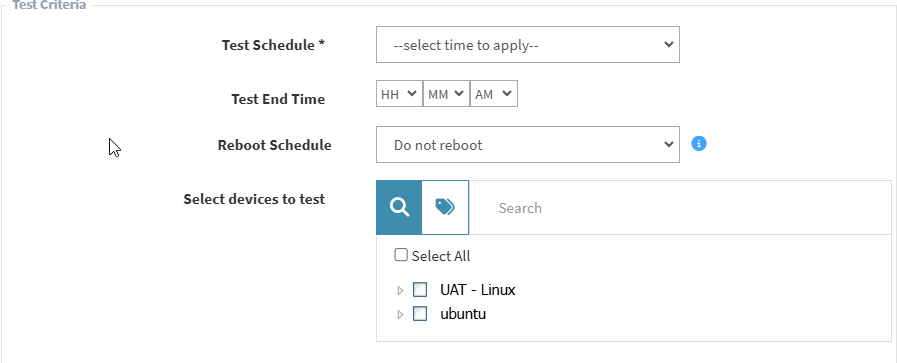
- Schedule the job immediately or after a scan and set the time counter accordingly in the test schedule fields. You can also choose to set the job to execute on a different date.
- Click on the Next button. Specify the details in the Deployment Criteria section. Click on the Test and Deploy Selected Patches button.
You will get a confirmation message that you created the job successfully.
Firmware
A comprehensive set of patches that cover software and firmware across all nodes to reduce vulnerabilities and security risks to the organization. This page lists assets with the patching details, a vendor who publishes the patch, date, and affected hosts. The filter and search options are provided to view the specific assets. Click on the Apply Selected Patches to create a new patching task. You can download the excel sheet of assets with patching details by clicking on the CSV icon.
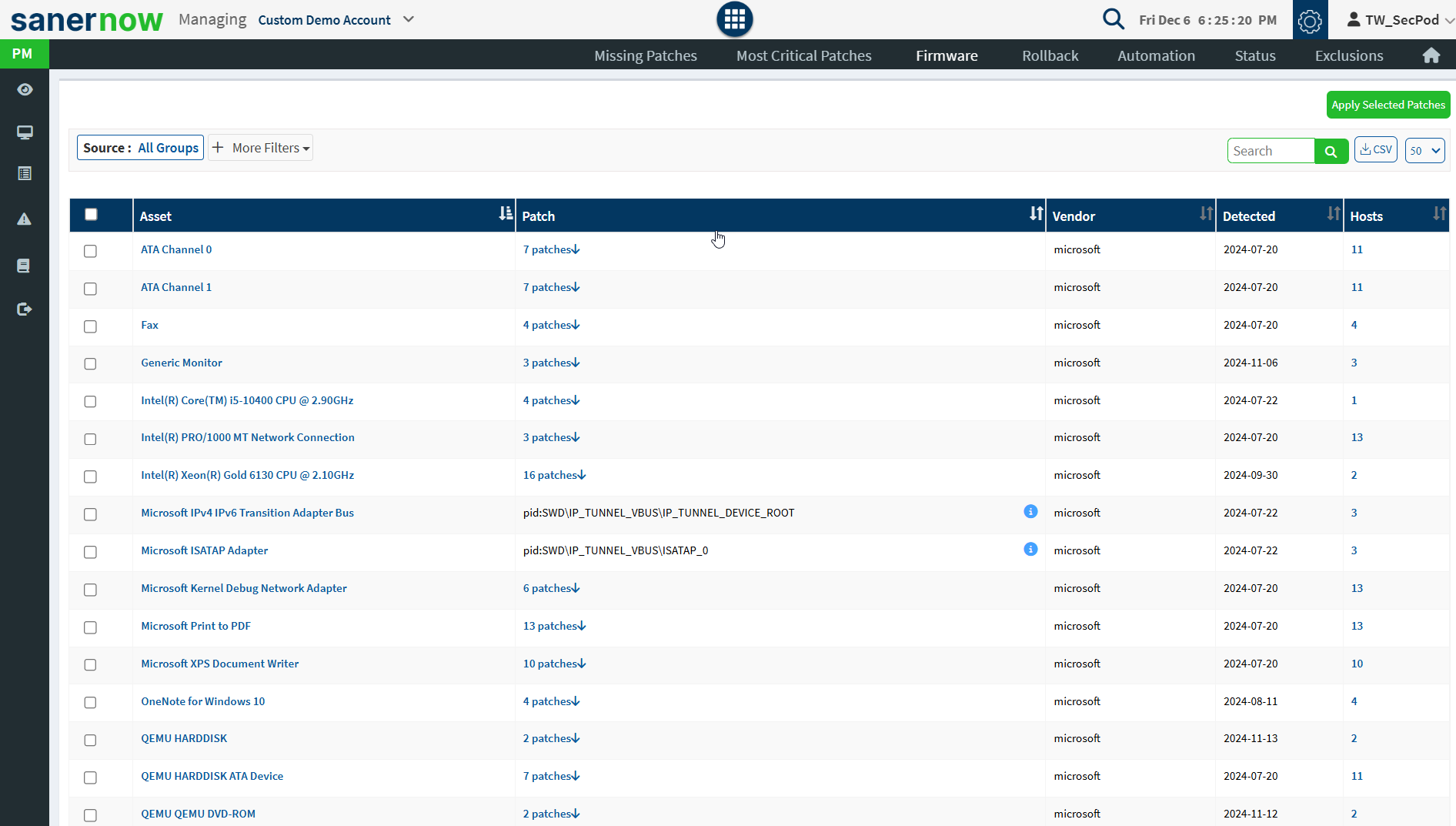
Patches Installed Over Time
This pane shows the number of vulnerable patches that have been installed over time so that the organization has a patch history. The history will help to understand its security health and plan its actions. You can download an excel sheet of patches installed over time by clicking the CSV icon.
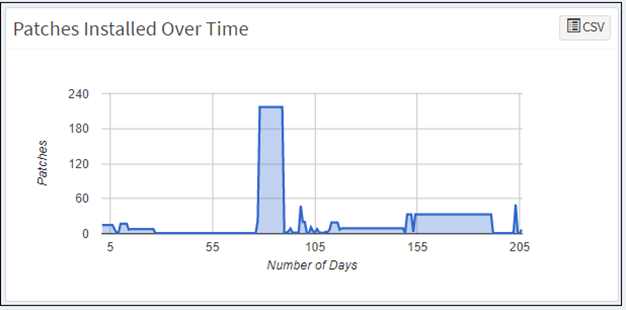
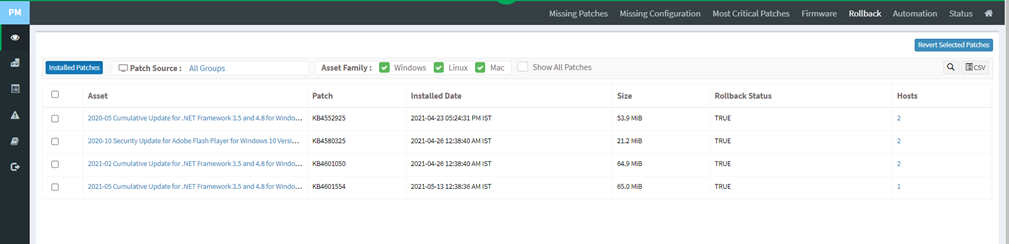
Installed Patches
This page shows a list of patches applied for assets, the installation date, the size of the patch, the rollback status, and the system that has the asset. The asset view shows detailed information on vulnerable patches already installed on assets.
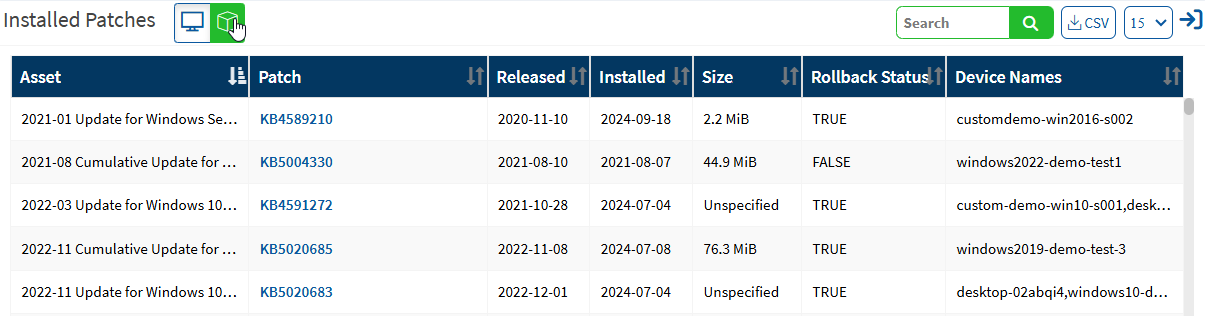
A toggle option is provided in the installed patches pane to switch between Device and Asset view. The device view shows detailed information on vulnerable patches installed on devices, as shown below.
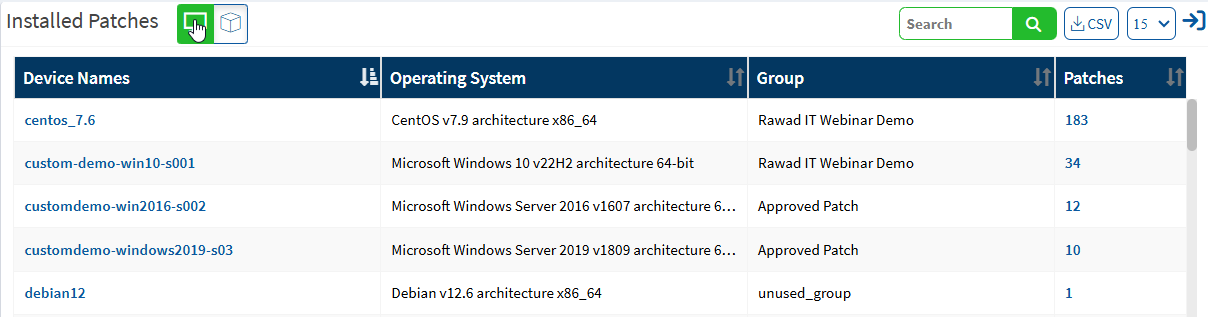
Click the expand icon if you want to rollback any patches. The Installed Patches page is displayed. You can filter the list of installed patches by groups of devices to traverse the list quickly, or you can search for the required device or group.
Rollback
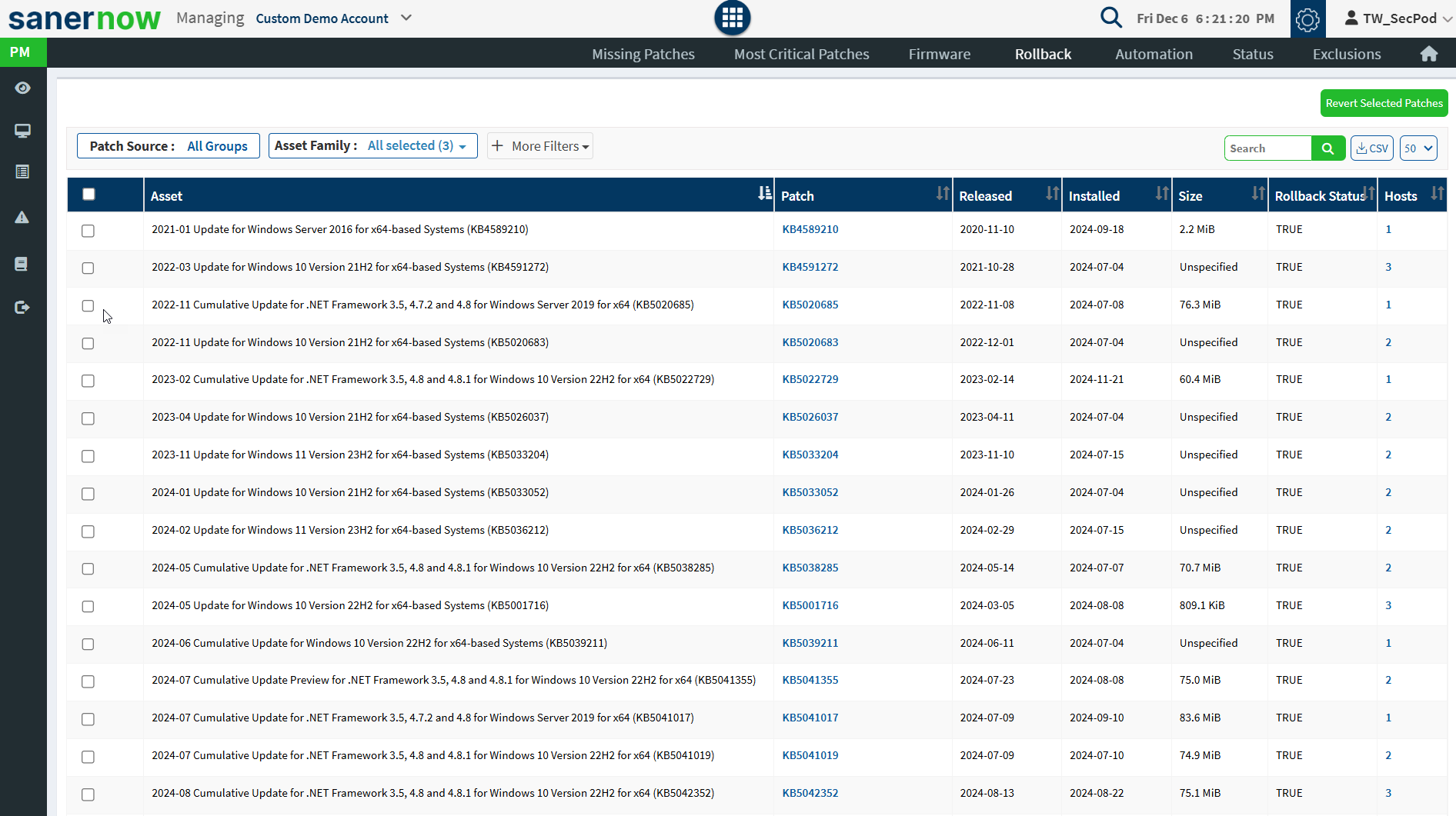
Click on the Rollback option at the top right corner of the PM page. It will list the installed patches for each device and asset.
- Select the assets you want to rollback patching and click on the Revert Selected Patches button.
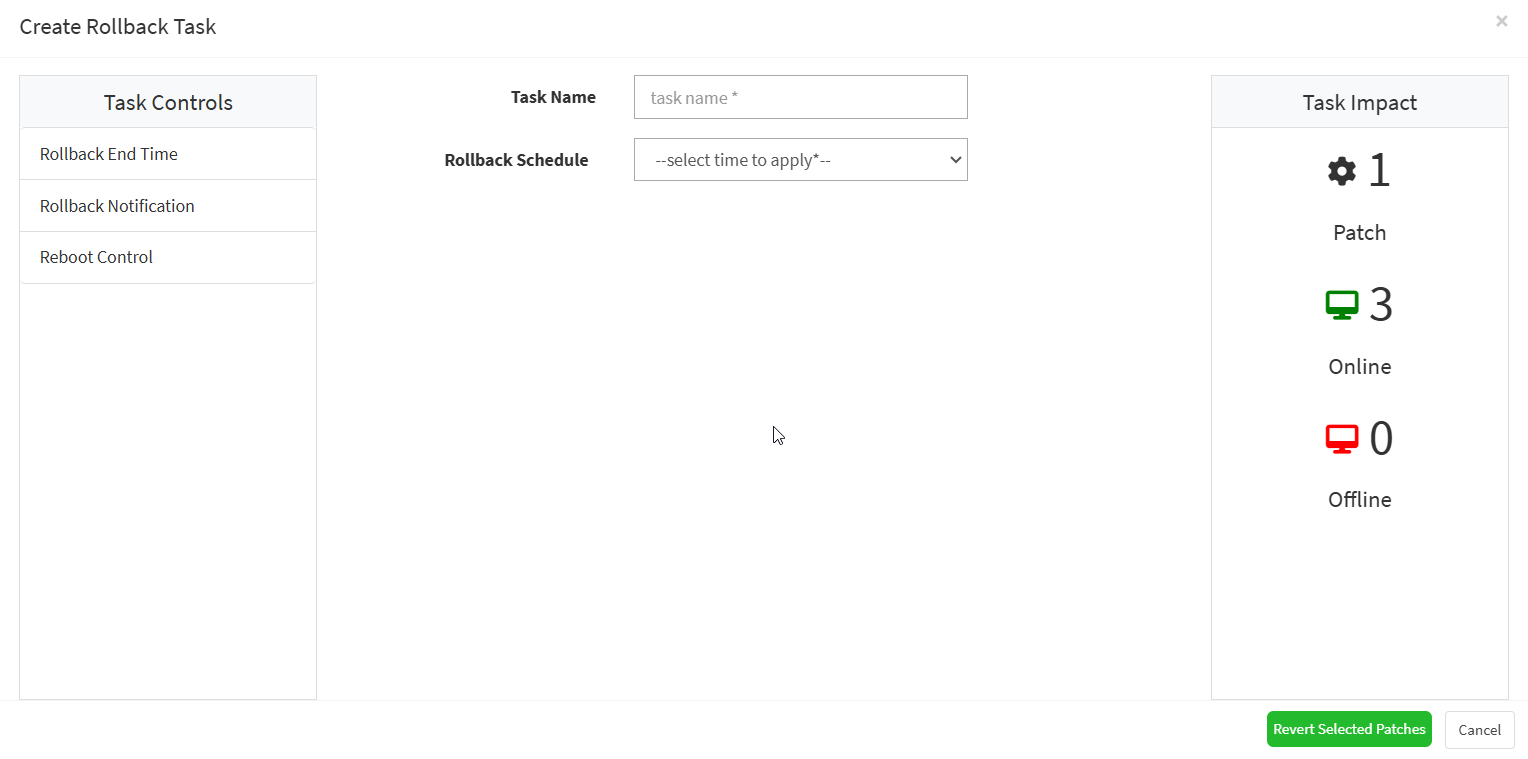
The Create Rollback Task dialog is displayed.
- Specify a job name and select rollback schedule from the drop-down menu.
- Specify whether you want the job done immediately or after a scan and set the time counter accordingly. You can also choose to set the job to execute on a different date.
- Provide the rollback notification message to display when the task is completed.
- Click on the Revert Selected Patches button after specifying the details.
Automation
Saner PM offers a reboot schedule function integrated with its patch automation rules. To run the latest version without delays, you can schedule monthly, weekly, or scheduled reboots according to your requirements. Saner PM supports new patches offered by vendors within 24 hours of release to ensure quick risk mitigation. All patches are pre-tested to check for any compatibility issues and errors. When a vendor releases an important update, SecPod also sends out email alerts to ensure you do not miss them. After the patches are deployed, Saner PM performs a final patch verification on the device to check the patch status. Saner PM also packs additional handy features such as patch rollback to provide further control over patch jobs.
To install missing patches using an automated task, click on the Automation button at the top of the PM page. The Automation page will display the list of vulnerable assets with the publisher’s details.
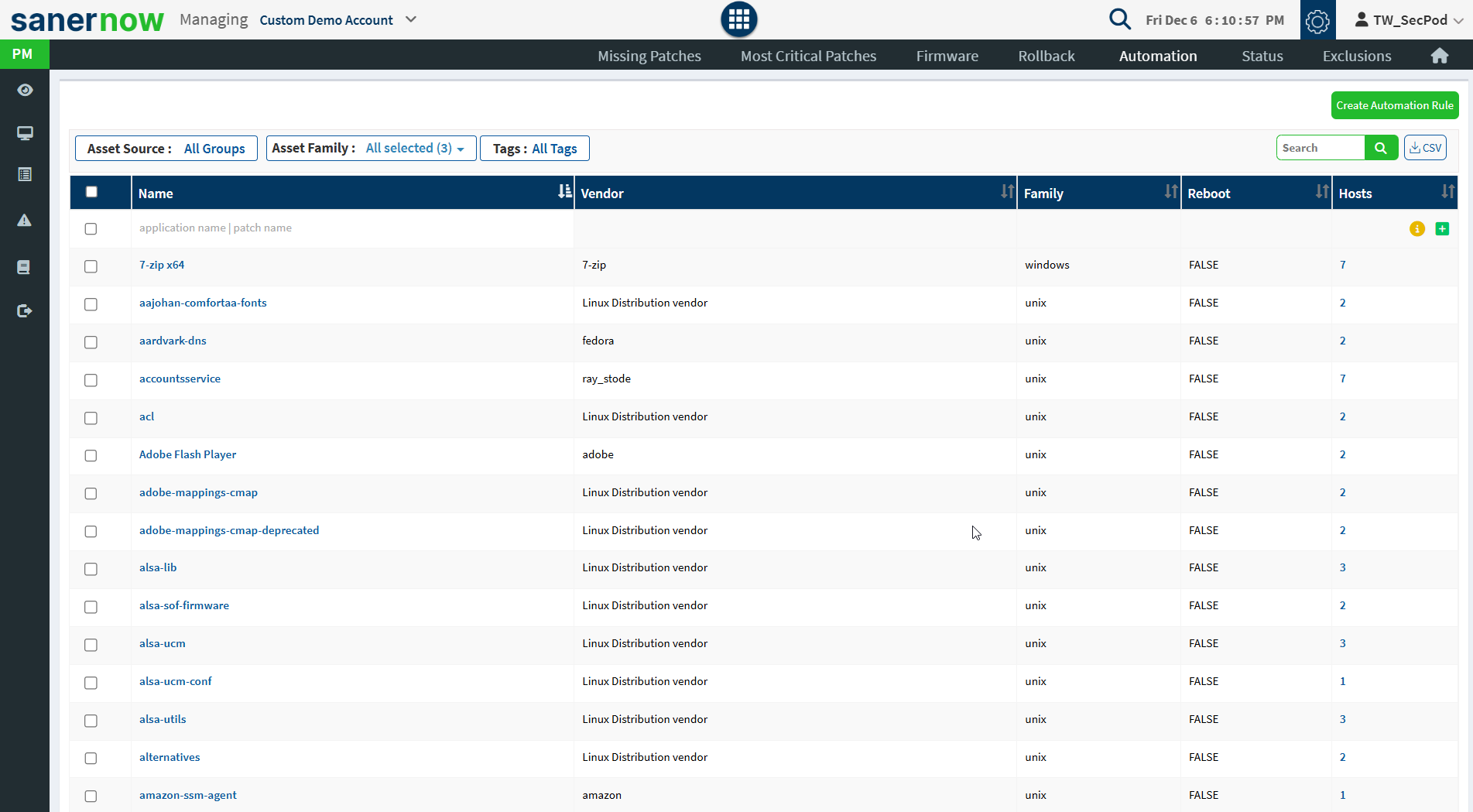
Select an asset that you want to mitigate vulnerabilities automatically and click on the Create Automation Rule button to schedule a task. Schedule a Task dialog is displayed as shown in the below image.
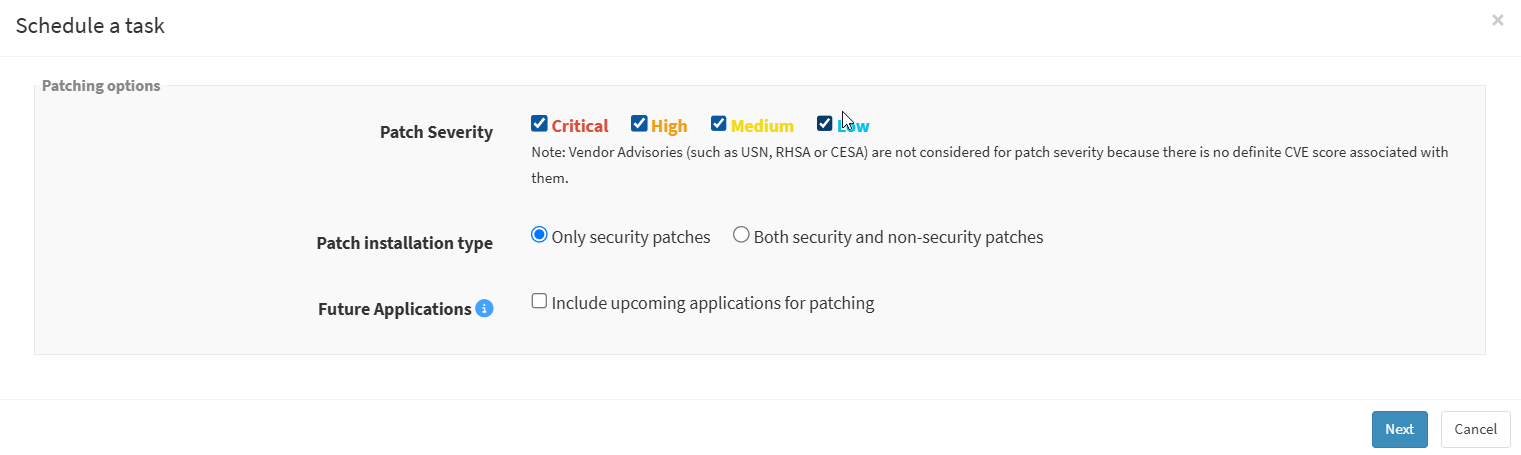
Select patches based on severity and patch installation type, and click on the Future assets check box if you want to remediate future assets. The vulnerabilities will be remediated based on the above options provided by the user. Click on the Next button.
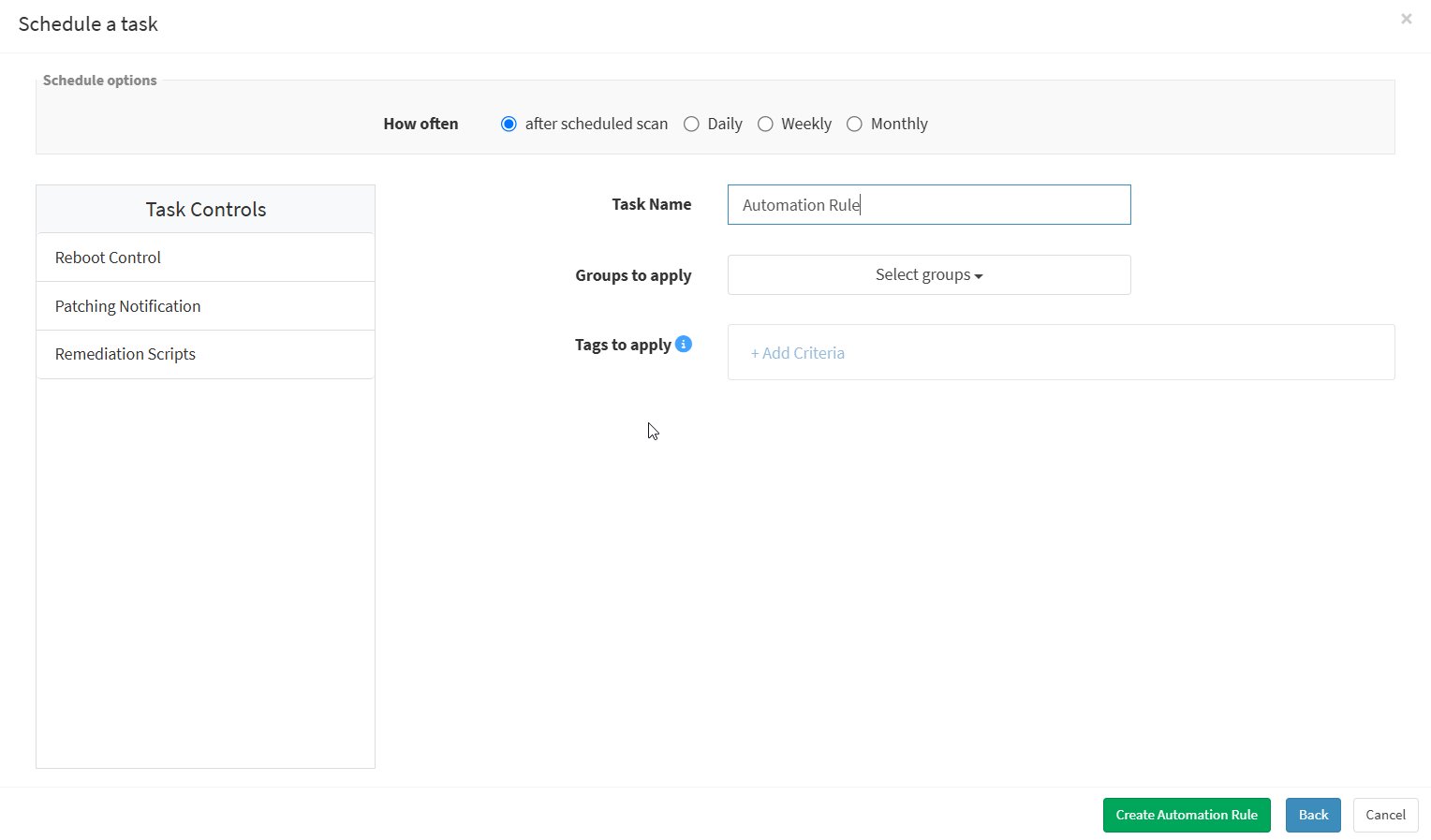
The user can schedule a remediation task based on his timing. Specify how often you need to run a scan and select the option to reboot. Choose to set the task to execute on a different date, weekly, monthly, or daily. If weekly, specify the dates and times. If monthly, specify the dates and times. Select scripts to run while rebooting, specify the task name and provide the patching notification message to display after completing the activity. You can also select groups to apply the rule settings. Click on the Create Automation Rule button, and a remediation task will be created. The remediation task will run automatically based on the scheduled timing.
This report provides detailed information on all the software assets in an account. Details such as software asset’s name and version, the publisher and signing authority of the software asset, the path where the executable file resides on the host, the number of hosts that contain the software asset installed, and the number of instances of each software asset are presented in the report.
Patch Approval
Saner PM lets you create a Patch Approval Workflow to enable tighter control over patch deployment. The Patch Approval capability enables administrators to define who can approve patches before they are applied, ensuring better governance, accountability, and alignment with internal change control policies. By default, patch approval is disabled. You must enable it to approve patches and remediation jobs.
Enabling Patch Approval
You must enable patch approval from the Patch Configurations menu. Follow the steps below to enable patch approval.
1. Click the ![]() icon on the Saner PM dashboard.
icon on the Saner PM dashboard.
The Patch Configurations page appears.
2. [Mandatory]Click the Configuration button to enable patch approval.
3. [Optional] Click the Enable Auto Approval button to activate auto patch approval. Once the Auto Approval is enabled, specify the Patch Group, Patch Severity, and Patch Released Days.
4. [Optional] In the Patch Group drop-down box, you can choose from All, Security, and Non-security. If you choose All, both security and non-security patches will be selected. If you choose Security – only security patches will be considered for patch approval. Similarly, if you choose Non-security – only non-security patches will be considered for patch approval.
5. In the Patch Severity drop-down box, you can choose from All, Critical, High, Medium, Low, and None.
If you choose All– all the patches with patch severity (Critical, High, Medium, Low, and None are selected). If you choose Critical, only patches with critical severity are considered for patch approval. Similarly, if you choose High, only patches with high severity are considered for patch approval. If you choose Medium, only patches with medium severity are considered for patch approval. If you choose Low, only patches with low severity are considered for patch approval.
6. In the Patch Released Days, enter the number of days Saner PM should consider auto-approving the patch once the vendor releases it.
7. In the Patch Cleanup box, enter the number of older patch versions you want Saner PM to maintain backups of.
8. [Optional] Click the Job Approvals checkbox to permit non-approver users to create remediation jobs for approved patches.
Click Update to save the patch approval configurations.
Managing Patch Approval Access
Admin and Org Administrators have patch approval access by default. These users can approve/reject requests to add patches to the approved patches list and approve/reject remediation jobs created by users who don’t have patch approval access.
By default, any newly created user in Saner has patch approval access. Only normal users with read-only access won’t have patch approval access. |
Granting / Revoking Access for Patch Approval
On the Patch Configuration page, the Patch Approval Access table lists all the users and their patch approval access status.
| Field | Description |
| Username | The name of the user is displayed in the Username column. |
| The email address associated with the user is displayed in the Email column. | |
| Role | The role assigned to the user account is shown in the Role column. |
| Approval Access | The user’s patch approval access status is displayed in the Approval Access column. If it is a Yes, it means that the user has patch approval access. If it is a No, it means that the user doesn’t have patch approval access. |
You can search for users by entering the username in the Search box next to the ![]() icon.
icon.
To grant a user patch approval access, click the checkbox next to the username you want to grant patch approval access and click the Grant button located above the Patch Approval table.
To revoke a user’s patch approval access, click the checkbox next to the username you want to revoke patch approval access and click the Revoke button located above the Patch Approval table.
Adding Patches to the Approved Patches List
Once you enable Patch Approval, users without Patch Approval access cannot create remediation jobs until the patch(s) is part of the Approved Patches list.
To add patch(s) to the Approved Patches list, users should select the patches and request that the patch(s) be added to the Approved Patches list.
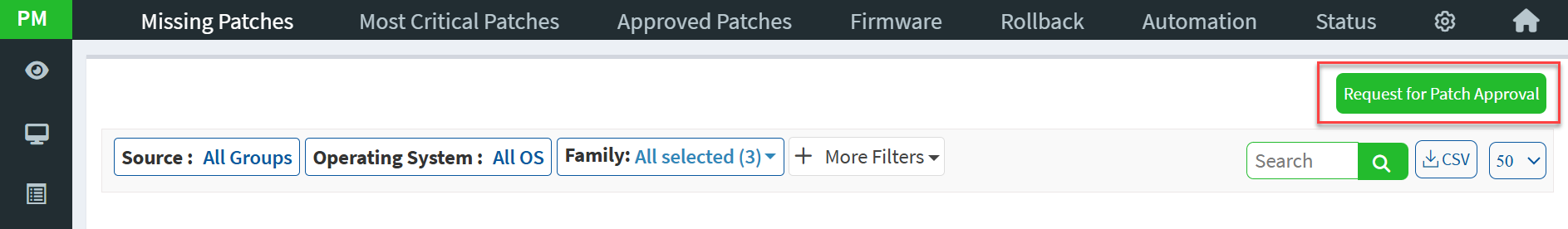
Once the patch approval request is placed, the Approval Status for those patches gets updated to Pending for Approval.
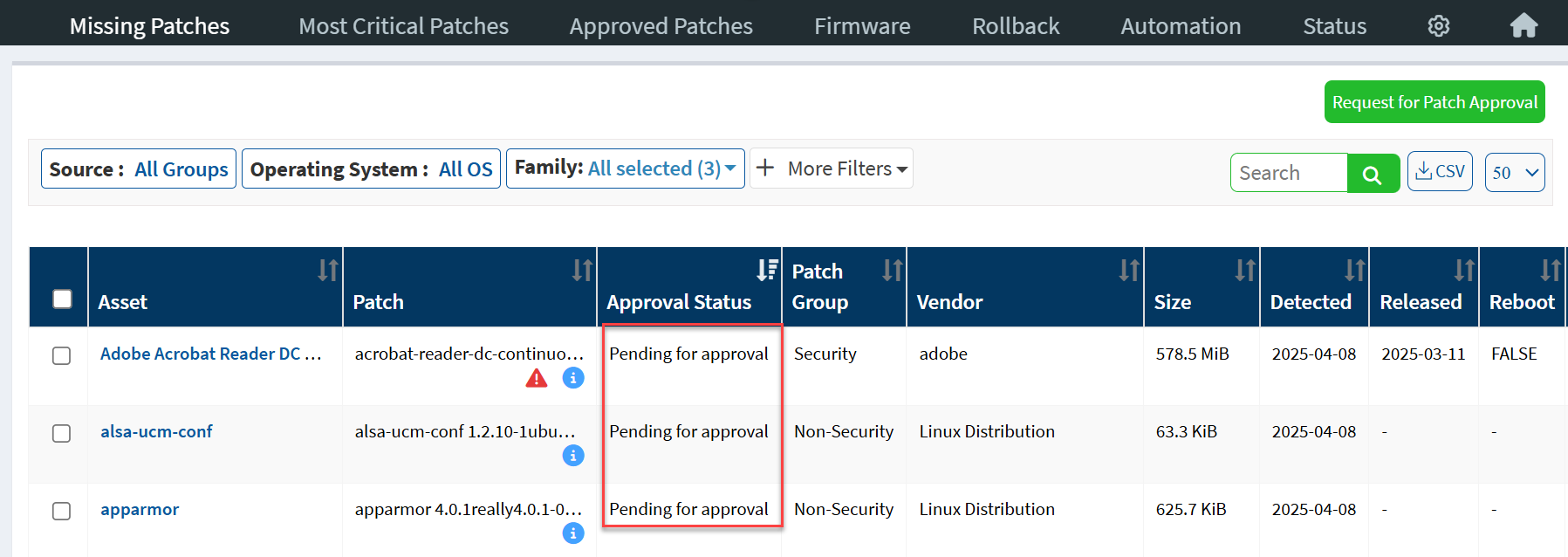
Depending on the patch type, users with Patch Approval access can approve /reject the patches from the Missing Patches page or the Most Critical Patches page. The Patch Approval button allows users to approve/reject patch(s).
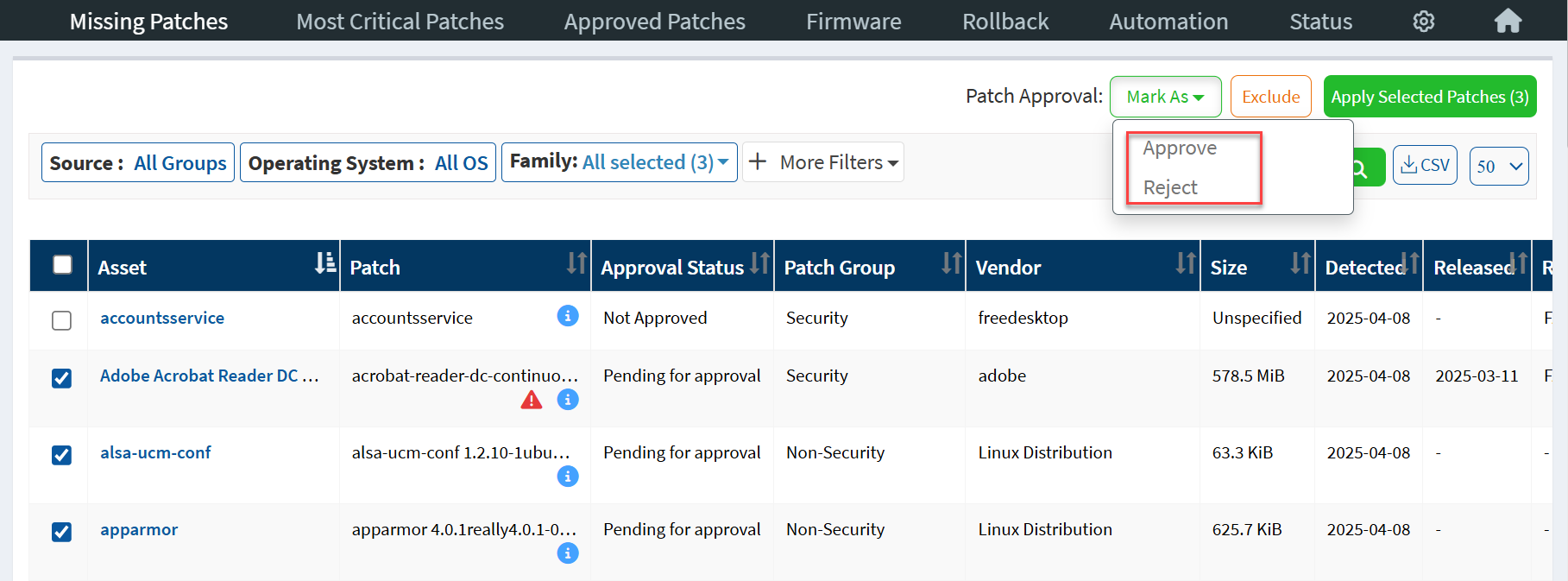
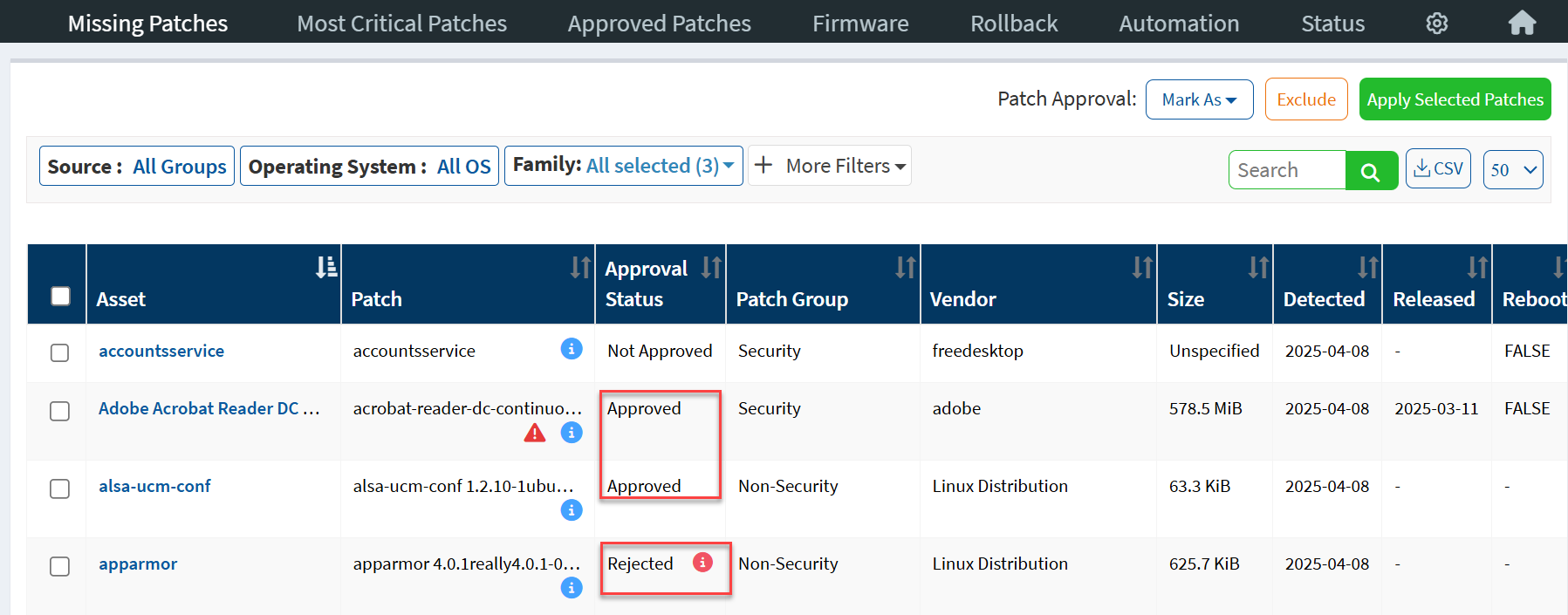
If the patch is approved, it is shown as Approved under the Approval Status column. Similarly, if the patch is rejected, it is shown as Rejected under the Approval Status column.
You can click the ![]() icon to view the patch rejection reason.
icon to view the patch rejection reason.
Once the patches are approved, they are listed under Approved Patches.
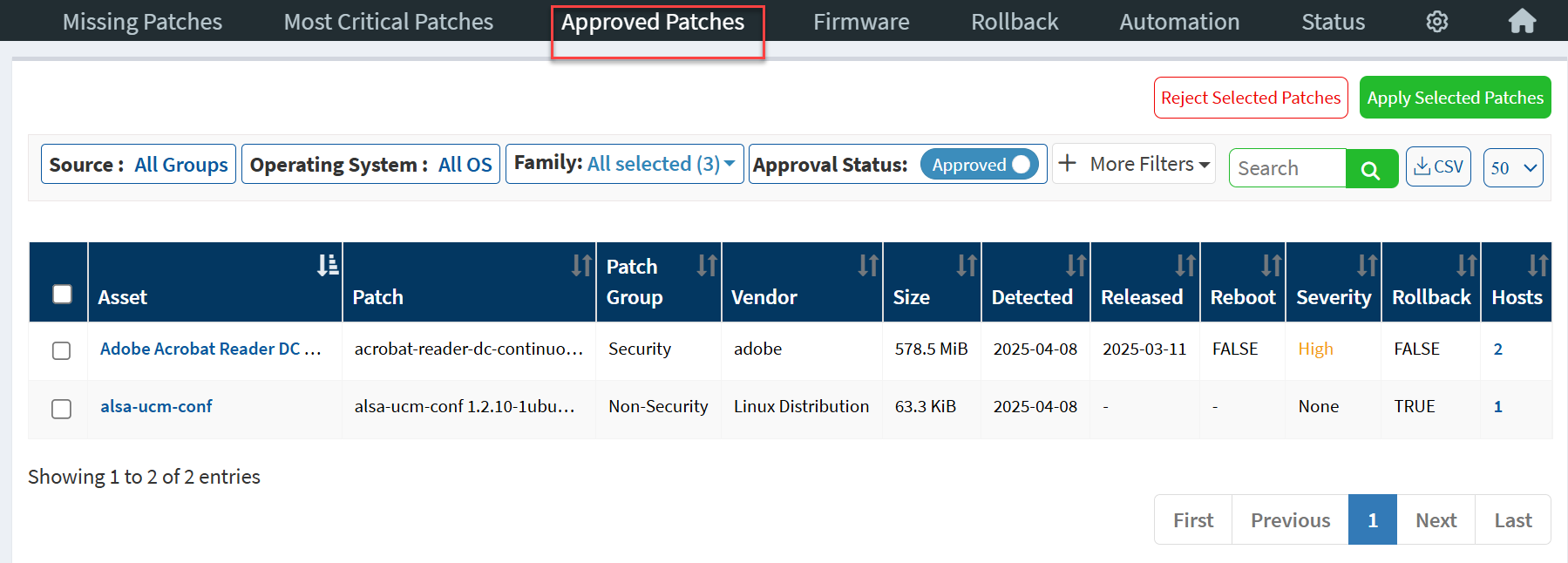
Viewing Approved Patches
The Approved Patches page displays all the approved patches. Users without Patch Approval access can select the patches from the list and create remediation jobs. Users can use the Approval Status filter to display Approved and Rejected patches.
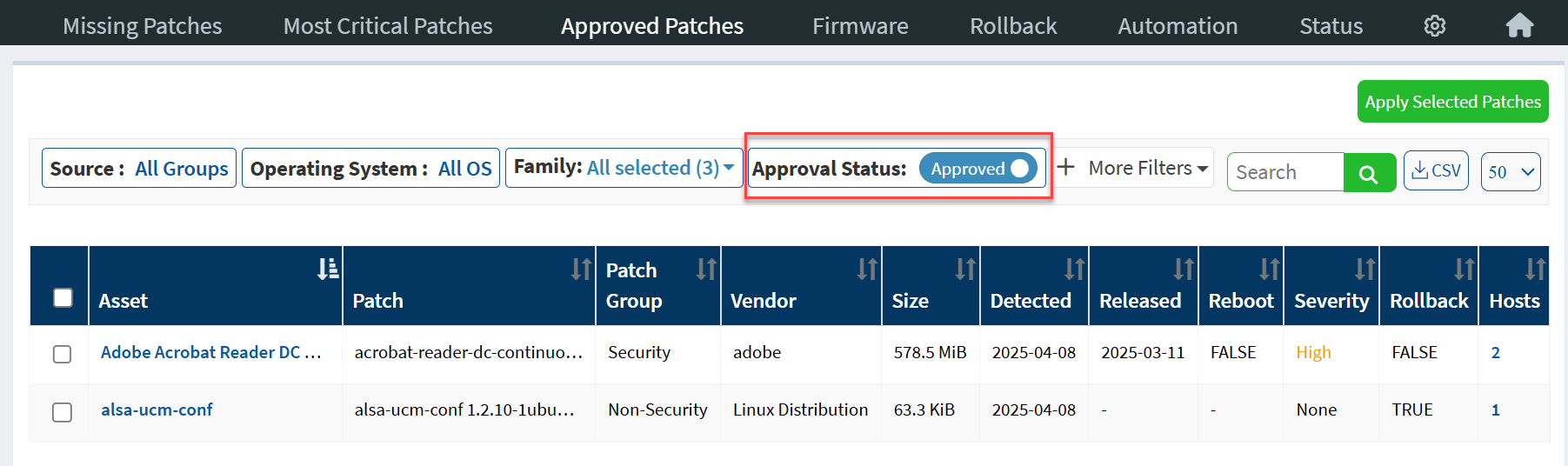
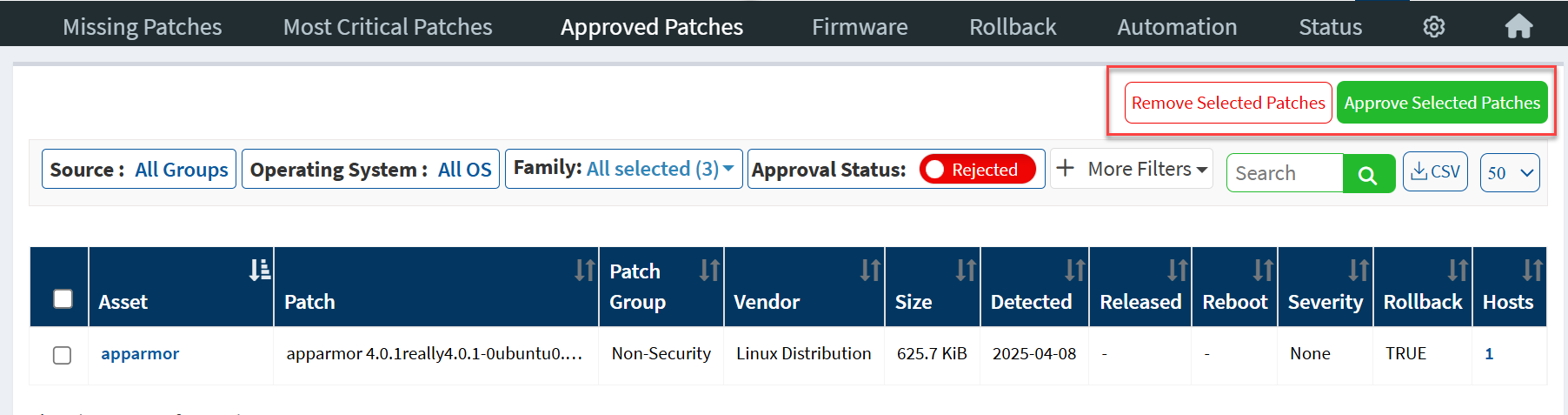
Users with Patch Approval access can reject approved patches using the Reject Selected Patches button.
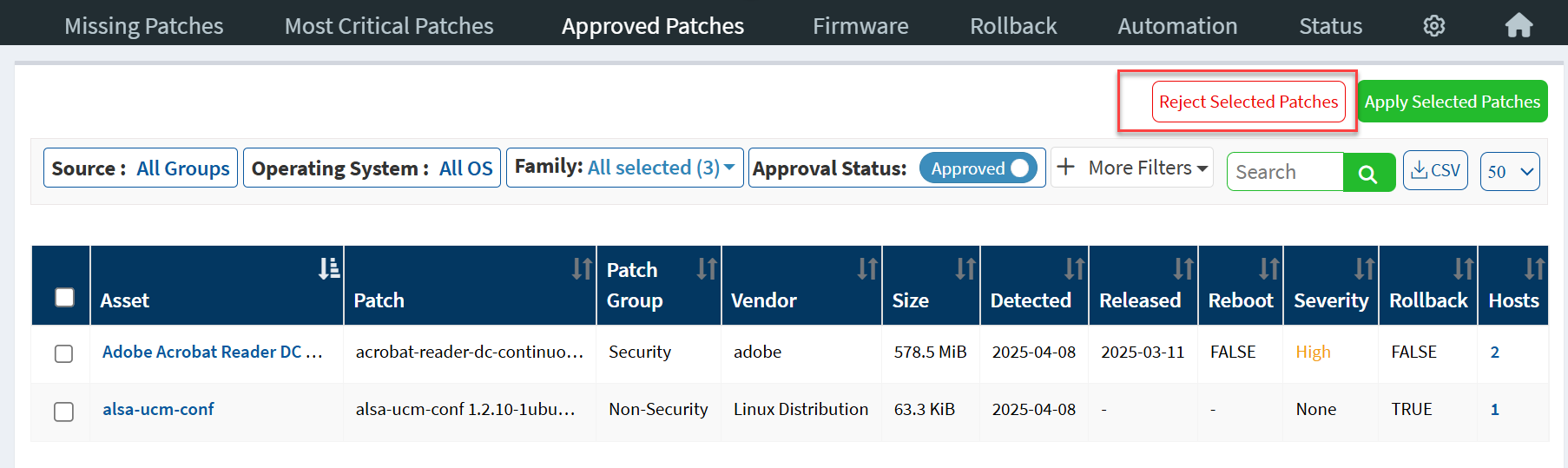
Similarly, they can approve rejected patches using the Approve Selected Patches button, or they can choose to remove the rejected patches from the Approved Patches page using the Remove Selected Patches button.
Approving Remediation Jobs
Users without Patch Approval access can create remediation jobs using approved patches. The remediation job gets created but is not sent to the Saner Agent unless a user with Patch Approval access approves it.
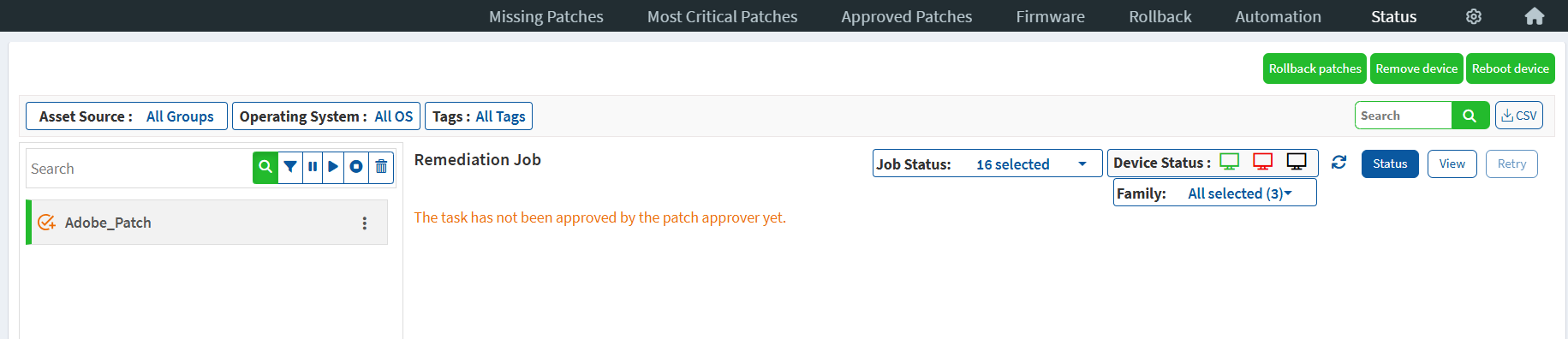
To approve/reject a remediation job, users with Patch Approval access should go to the Status page. Select the remediation job listed on the left side of the page. Click the three dots next to the remediation job to approve/reject a remediation job.
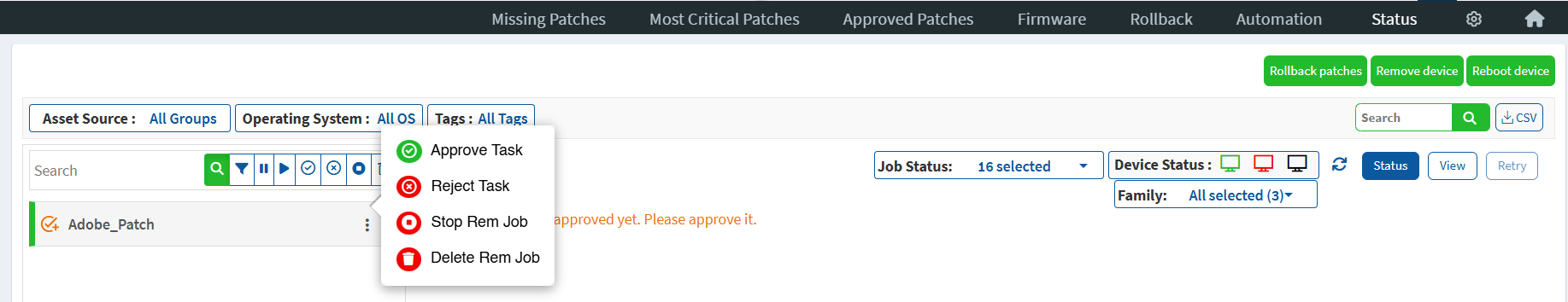
If the user clicks Approve Task , the remediation job is sent to the Saner Agent wherein the agent performs the remediation activity specified in the task.
If the user clicks Reject Task, the remediation job is cancelled and no action is performed.
Remediation SLA
Security teams deal with a plentitude of vulnerabilities; however, they often assign the same Service Level Agreement(SLA) to all the vulnerabilities regardless of severity. However, the one-size-fits-all approach is not ideal when it comes to vulnerabilities. Vulnerabilities fall into different categories; some are critical, while others may be less severe. It is pivotal to patch the critical vulnerabilities on the highest priority to stop any impending threats it may cause to the organization if left unpatched.
Each patch should be assigned a unique SLA depending on its severity. Saner PM allows you to specify Service Level Agreements (SLA) for different patches detected in your environment. The Remediation SLA in Saner PM allows you to specify different SLAs for different patches. You can specify SLAs for the following patch categories.
- Most critical patches
- Critical severity patches
- High severity patches
- Low severity patches
- Feature patches
- Third-party patches
- Microsoft vendor security patches
- Unix vendor security patches
- MAC vendor security patches
- All patches
You can use Groups or Tags to define the scope of devices to which the SLA Configuration should be applied. The SLA Configuration gets applied to the devices that are part of the selected Group or Tag.
Creating a new SLA Configuration
| User access level: Only Organization Admin, Account Admin, and Normal Users with full access can create, edit, and delete SLA Configurations. Normal Users with read-only access can only view SLA Configurations. |
You can create a new SLA Configuration that meets your organization’s requirements. Follow the steps below to create a new SLA configuration.
- Click Create SLA Remediation. The New SLA Configuration screen appears.
- [Mandatory] In the Name box, enter a unique name for the SLA configuration. The name should be more than four characters and not exceed 35 characters.
- In the Description box, describe the SLA configuration. The description should be more than four characters and not exceed 35 characters.
- [Mandatory] In the Based on section, choose between Release Date and Detected Date. If you choose Release Date – Saner PM considers the date the software vendor released the patch during SLA compliance computation. If you choose Detected Date – Saner PM considers the date on which the Saner PM detected the missing patch during SLA compliance computation.
- [Mandatory] In the Rule criteria box, check the box next to the rule to select the rule you want to be part of the newly created SLA configuration. You can modify these values to align with your organization’s SLA.
- [Mandatory] In the Scope section, choose between Group or Tags. If you select the Group option, you can select the groups from the Groups drop-down box. Similarly, if you choose the Tags option, you must specify the tag criteria using the Add Criteria button. Once you have specified the tag criteria, click Apply.
- Click Create to create the new SLA Configuration. Saner PM creates the SLA Configuration based on the name, description, and rule criteria you selected.
| Note You can also use the Default SLA Configuration. However, by default, it is inactive. You must assign a Group or a Tag to the Default SLA Configuration to activate and use it. |
Viewing existing SLA Configurations
The Remediation SLA page displays all the SLA Configurations in the account. Every SLA Configuration present in the account is listed with the below details.
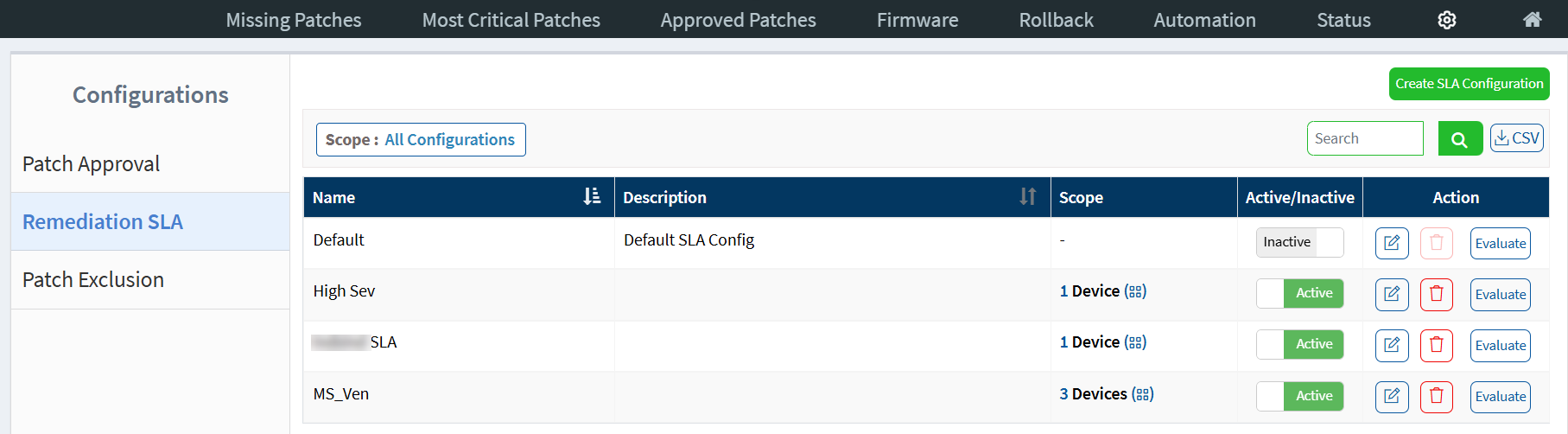
You can find the below details about SLA Configurations on the Remediation SLA page.
Name — The name of the SLA configuration.
Description — A brief description about the SLA configuration.
Scope — The scope assigned to the SLA Configuration and the number of devices part of the selected scope. A SLA Configuration can be assigned to a Group ![]() or a Tag
or a Tag ![]() .
.
Active/Inactive — The SLA Configuration can be active or inactive.
Action — You can ![]() Edit,
Edit, ![]() Delete, or Evaluate an SLA Configuration.
Delete, or Evaluate an SLA Configuration.
Searching and Filtering SLA Configurations
You can search for existing SLA Configurations. Enter the name of the SLA Configuration you want to search for in the search box located on the right of the page and hit Enter. Saner PM displays all the SLA configurations that match the search criteria.
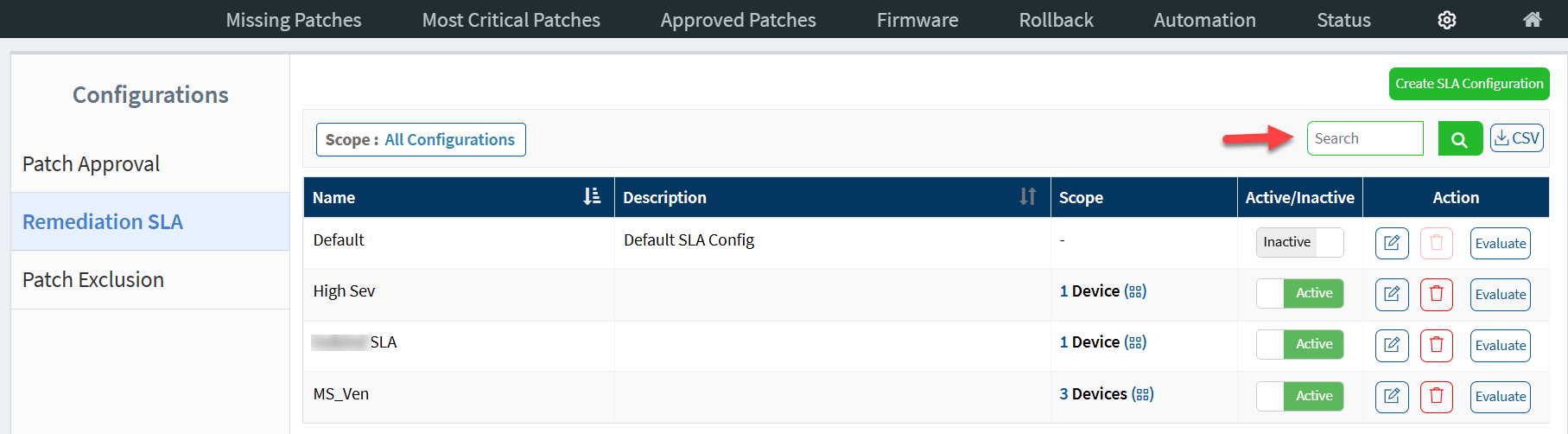
By default, the Remediation SLA page shows all the SLA Configurations. However, you can filter the SLA Configurations using the Scope filter. You can use the Scope filter to filter SLA Configurations assigned to a Group or a Device.
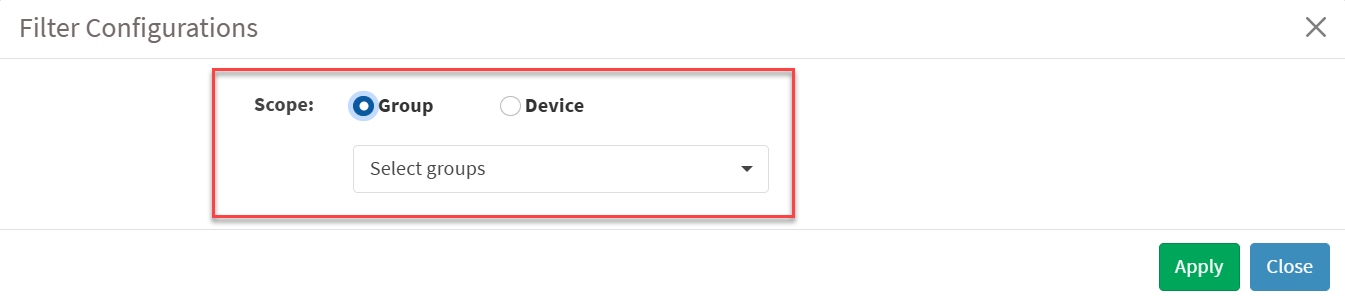
Follow the steps below to filter SLA Configurations assigned to a group.
1. Click the Scope filter. The Filter Configurations section appears.
2. In the Scope section, choose Group. From the groups drop-down box, choose the groups from the list. You can select one or more groups.
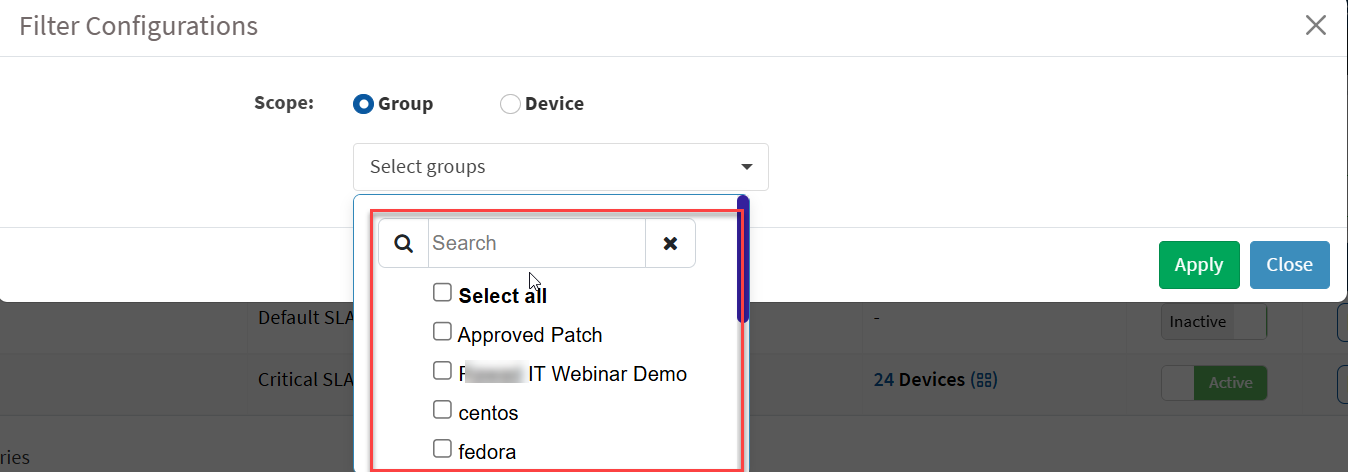
3. Click Apply. Saner PM displays the SLA Configurations assigned to the selected groups.
Follow the steps below to filter SLA Configurations assigned to a device.
1. Click the Scope filter. The Filter Configurations section appears.
2. In the Scope section, choose Device. From the Device list, click the checkboxes following the device name you want to select. You can select one or more devices.
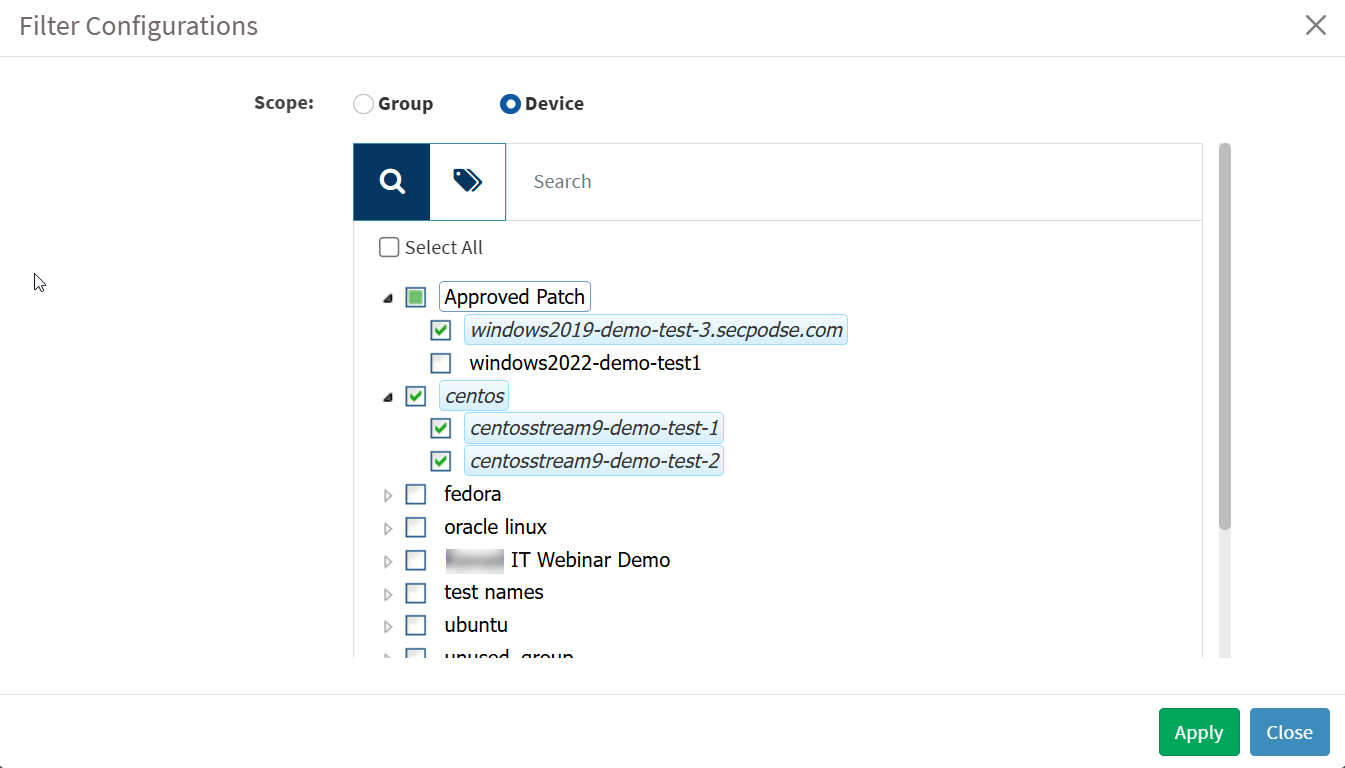
3. From the Device list, click the checkboxes following the device name you want to select. You can select one or more devices.
4. Click Apply.
Saner PM displays the SLA Configurations assigned to selected devices.
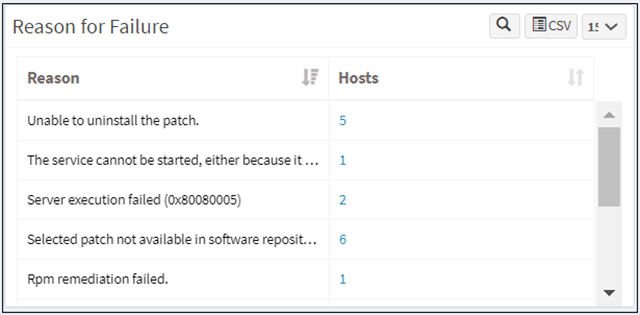
Reason for Failure
Sometimes, patches may not be successfully installed during patch management. This pane shows the number of hosts on which the patch has failed and categorizes the failed patches under remediation errors, application errors, device errors, download errors, etc. Click the host number or name to see more detail, such as which job failed or which patch was not installed.
Job Status Summary
This page shows the status of all the remediation tasks and patch installation or rollback jobs that were scheduled.
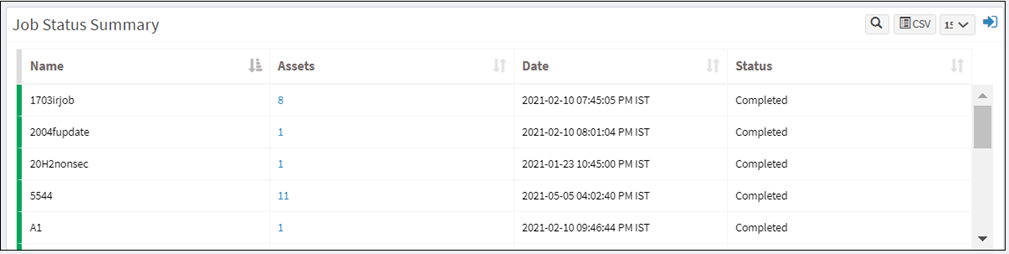
Click the Expand icon to see a list of all scheduled patch and rollback jobs. Click on any job to view the completion status of the job or the job creation information.
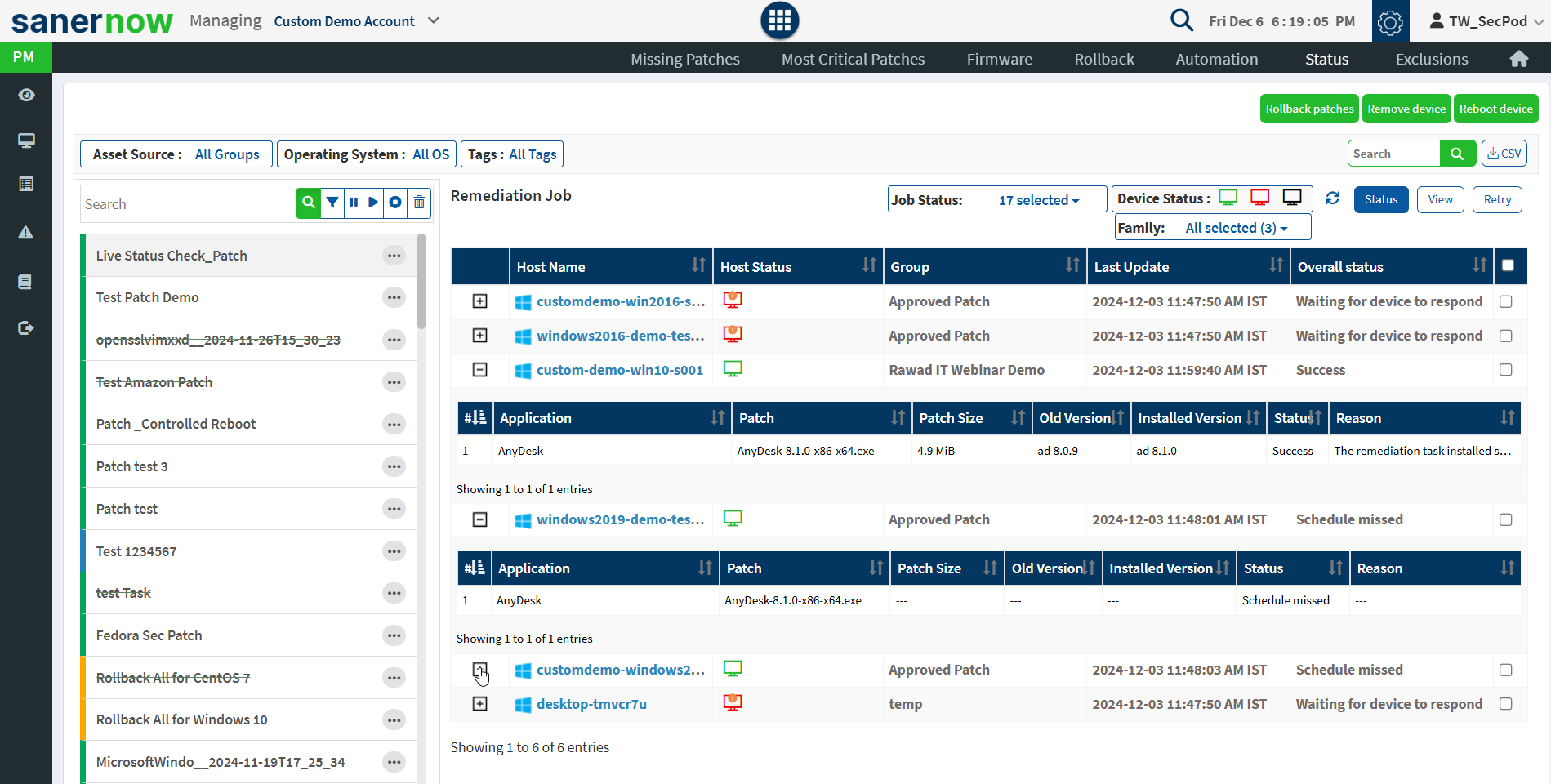
Status
Since patching is not a one-person and one-time task, they need to be executed and tracked continuously as a process. Saner PM accelerates each stage of the patching process with automation and additional features to quicken the process with minimal supervision. You can create specific patch jobs for a group of devices and track them to finish.
You can automate patching for specific operating systems (Windows, Mac, Linux), third-party applications, and firmware. Create jobs according to OSs, single/groups of applications, and department (device groups and Active Directory hierarchy). It can automate the entire patching cycle according to pre-set rules and conditions.
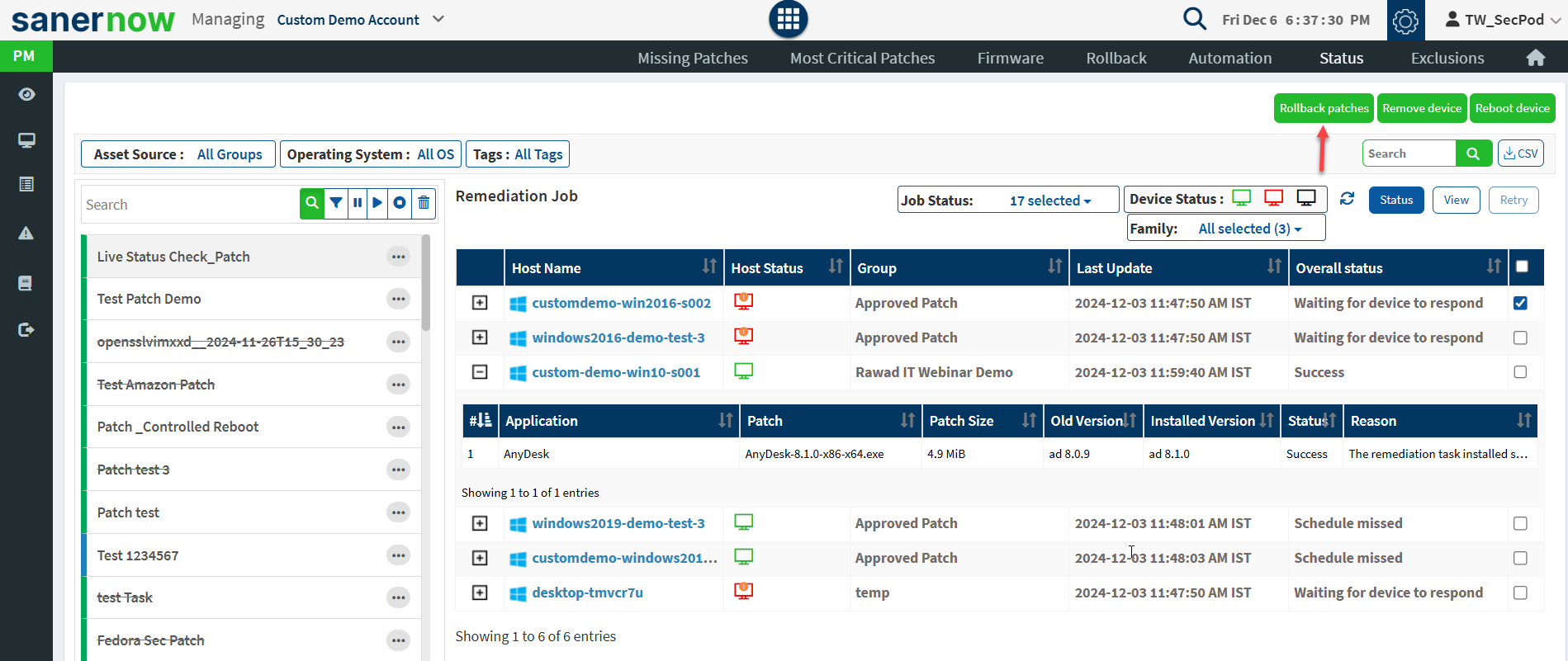
Users can rollback patches, remove devices, and reboot devices from the Status page. To remove a job applied for the device, select a device, and click on the Remove Device button.
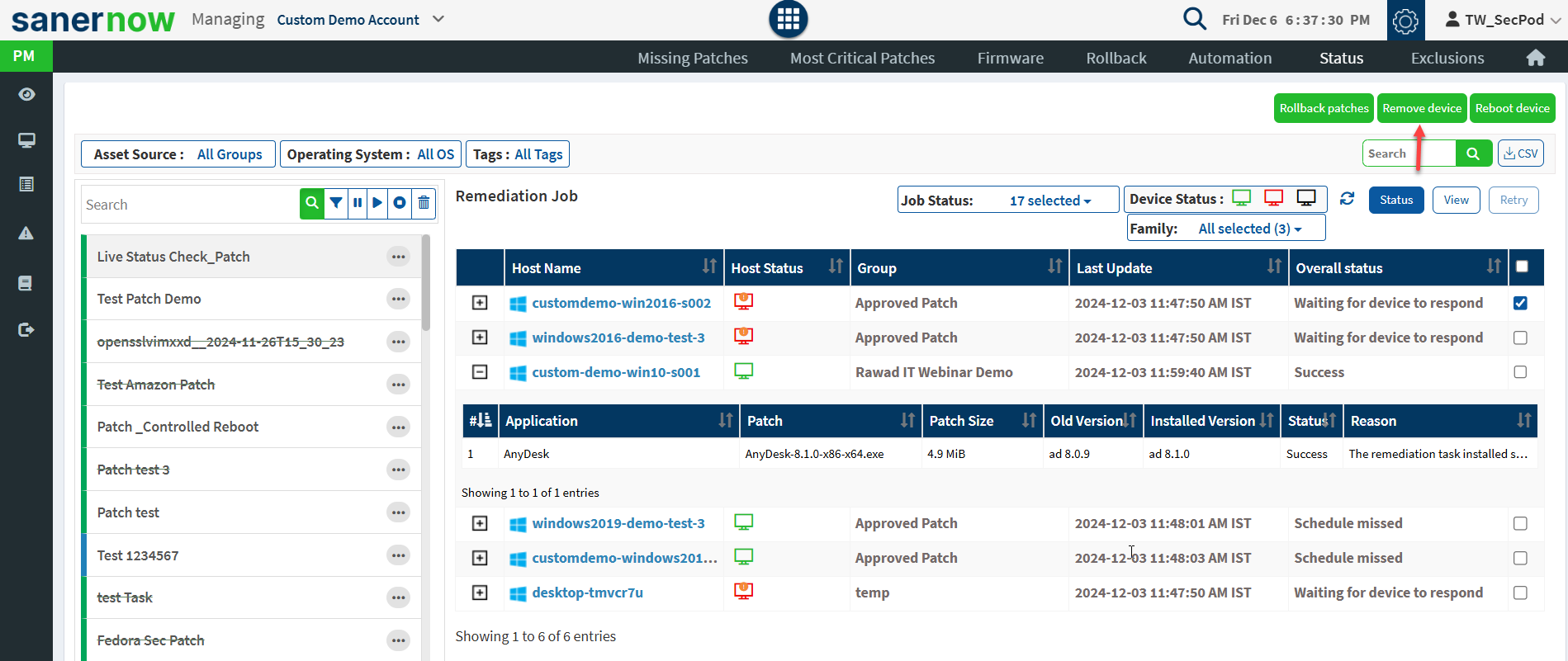
Select a device and click on the Rollback patches button to apply patches to the device.
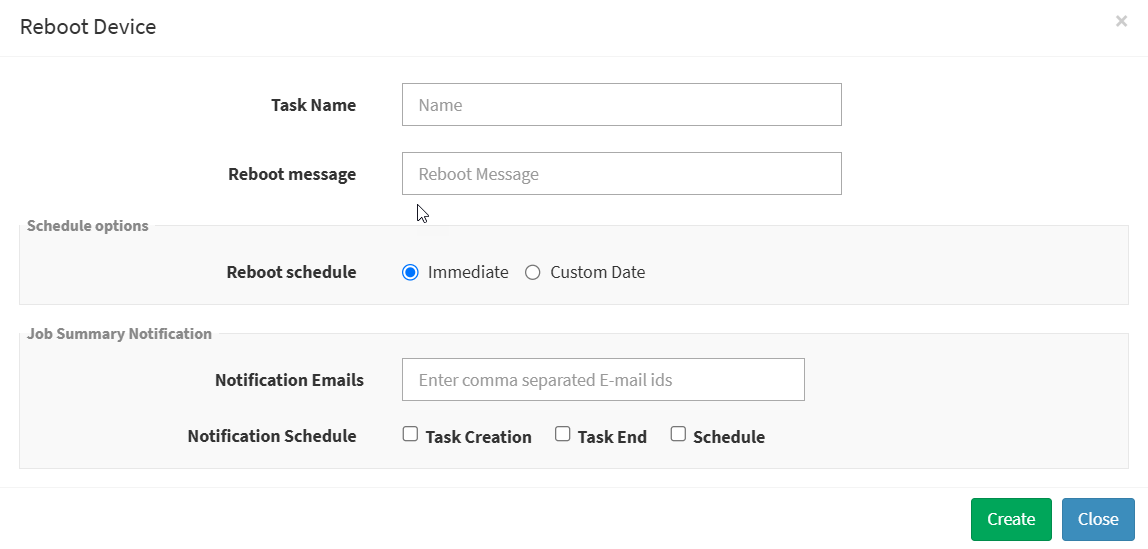
Select a device from the device list and click on the Reboot Device button. Specify the task name, reboot message, and select schedule options as immediate or custom date. Click on the Reboot button.
You can scan devices manually at any time. Once the scan is done, and vulnerabilities are known, remediation is performed by creating a job. The remediation job includes vulnerable/non-compliant assets that can be applied to groups. The remediation job can be executed immediately, scheduled on a particular date, or performed after the scheduled scan.
To Scan Devices Manually
1. Click Manage > Devices > Managed Devices.
2. Select device groups and click on the Scan Now button.
Once the Remediation Job is executed, you can generate a patch report again after 20-30 minutes. Compare this report with the report generated prior to the remediation job to identify how many hosts were affected and how many hosts have been remediated successfully.
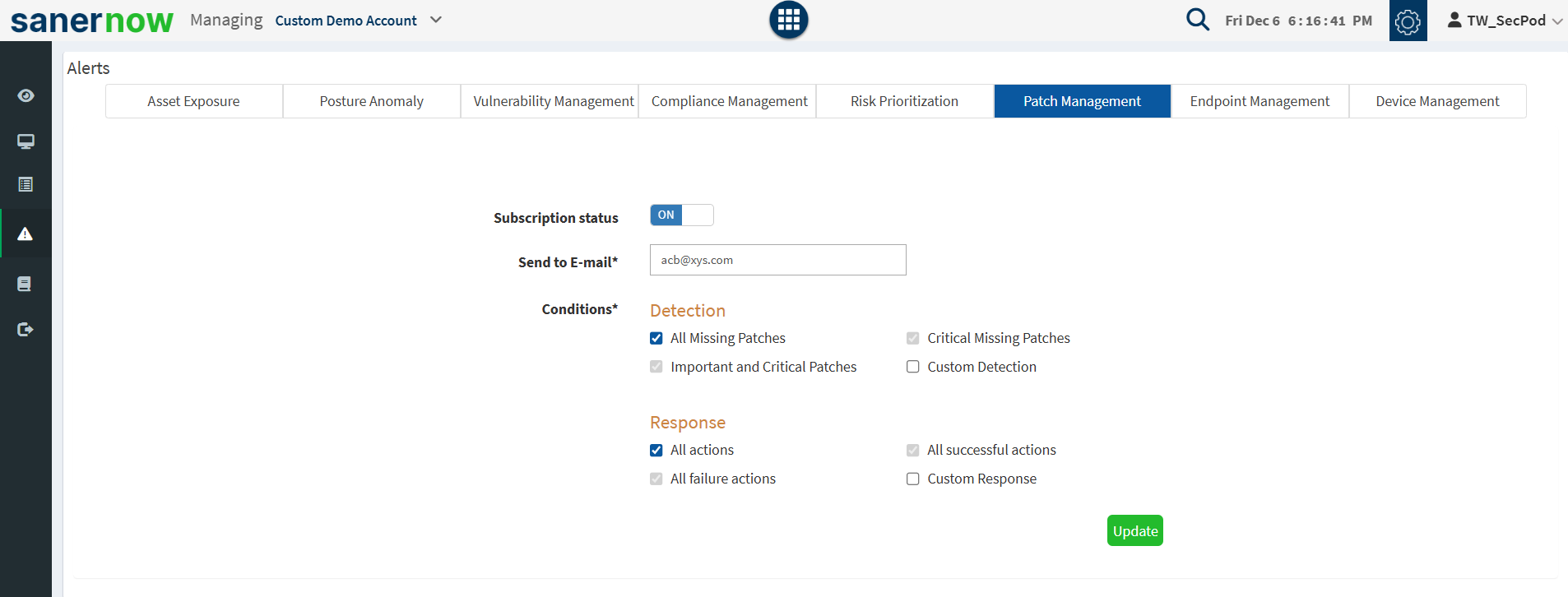
Setting Alerts for Patch Management
To stay on top of the patching tasks vital to maintaining security, you can set alerts.
To Set Alerts for Patch Management
- Click Alerts > Patch Management.
- Set the Subscription status to On.
- Specify the email address to which you want the alerts sent.
- Specify which conditions you want to receive detection and response alerts.
- You can choose to receive alerts related to detection – Important and Critical Patches, All Missing Patches, Critical Missing Patches, and Custom: If you select custom, you must specify the custom values in the Custom Detection box.
- You can choose to receive alerts related to response – All failure actions, All successful actions, All actions, and Custom. You must specify the custom values in the Custom Detection box if you select custom.
- Click on the Update button to complete the settings.
Patch Report
The patch report summarizes all the patch information, such as the missing patches, the critical patches, etc.
To generate a patch report
- Click on the Reports > Saved Report > Patch Report.
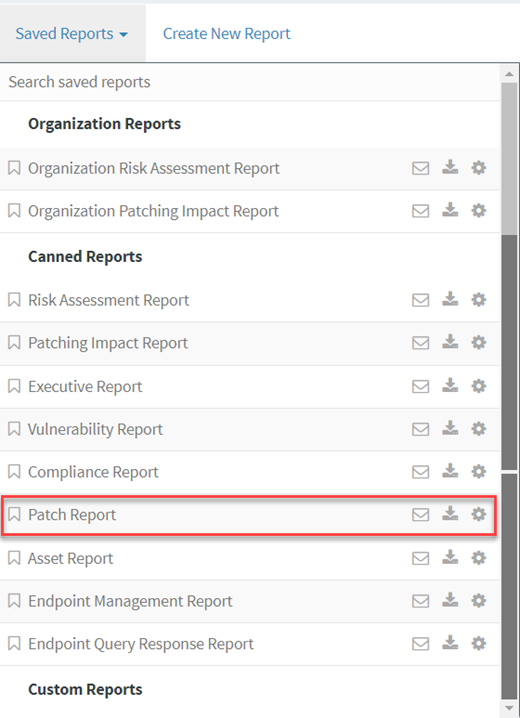
To export the report to a PDF.
- Click on the Download icon to download the PDF report.
To export the report and send it via email:
- Click on the Mail icon in the saved report section to email the report.
- Specify the email addresses.
To Back Up Reports
The backup settings under Reports allow IT, administrators, to obtain report backup. The backup report can be scheduled to run automatically daily or weekly.
To Back Up Reports
To configure backup settings for reports:
- Click Reports on the left pane.
- Click on Saved Reports and select the Patch Report option.
- Select the Settings option beside the Asset Report.
- Report Settings (Patch Report) pop up will be displayed in the image below.
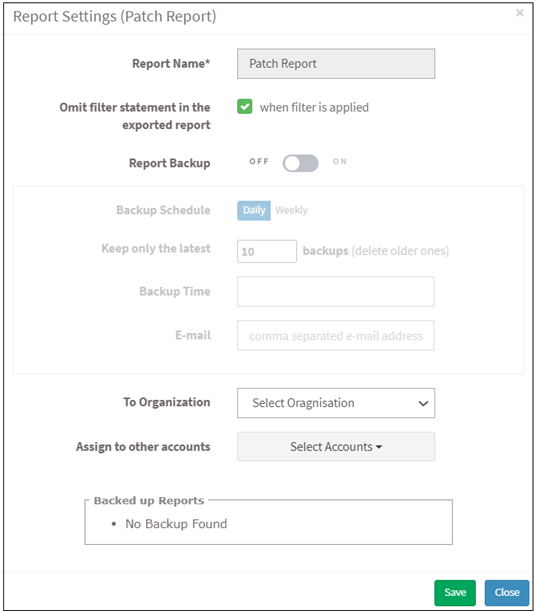
- Click the Omit filter statement in the exported report check box, and users can set the on/off button whether they want to back up the report.
- If the backup is on, select the weekly or daily option.
- Set a number in the Keep only the latest entry box. The report for the specified number of days is archived. If the number is three and the backup option is daily, then the reports from the last three days are maintained. Older files are deleted. You can maintain backups for a maximum of 30 days.
- Specify Email ID address. You can enter more than one email address with a comma-separated.
- Select the organization and accounts you want to apply these settings.
- Click on the Save button.
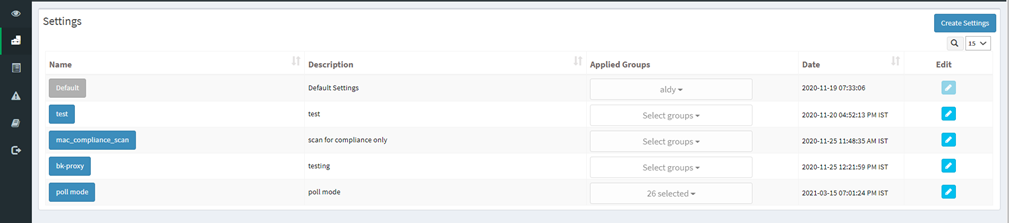
Click on the Create Settings button. By default, the scan scheduled time is 12:00 PM. Users can customize scan time and select any number of groups at the bottom and create the settings. Once the settings are created, the server will push these settings to an agent. Then the agent will start its daily scan at a scheduled time.


